
The war in Ukraine is not following its expected course. The Russian army has not simply marched across the country, and the invasion was not accompanied by a massive increase in cyber operations aimed against Ukrainian critical infrastructure.
This could all change in a moment – but for now the Russia/Ukraine conflict is likely to redefine the relationship between kinetic and cyber warfare. It began as expected: an increase in military power at the border and an increase in cyber operations against Ukraine designed to prepare the battlefield.
Those cyber operations have continued but have not escalated to the extent expected. New destructive malware has been detected on Ukrainian computers, but for the most part they are targeted and not in themselves designed to cause widespread infrastructure damage. They started with WhisperGate detected by Microsoft in January, but have been followed by HermeticWiper, IsaacWiper, and FoxBlade (although there are some suggestions that HermeticWiper and FoxBlade are separate names for the same malware).
There is currently no public proof that these malwares are state operations – but it seems likely. Wipers do not offer criminal gangs an easy method of monetization. While they could be developed and used by ‘patriotic’ hackers wishing to further their own cause, all these examples were developed well ahead of the conflict.
Escalation could, of course, still occur. “The expectation that cyber activity by Russia against Ukraine will be ratcheted down now the invasion has begun is wrong,” Tim Kosiba (currently CEO at Bracket f, a company owned by [redacted], but a former technical director at U.S. Cyber Command) told SecurityWeek. But why it hasn’t yet, at least to the time of writing this, remains a mystery.
If you want to bring a nation to its metaphorical knees, the quickest route would likely be through its power distribution. “Disrupt electrical power and you have an immediate impact that gets worse with time,” explains Lou Steinberg, CTM Insights founder and managing partner. “With no power, food rots. Medicines spoil. Gas stations can’t operate pumps, so fuel for trucks is stuck in underground tanks. No trucks mean no replacement food and medicine. Water and sewage treatment plants stop. People die.”
Russia has already tested cyber operations against Ukrainian power in 2015 and late 2016. In 2022 it chose a different route – it captured the Zaporizhzhia nuclear power plant through military action. We don’t know whether this was because it couldn’t destroy the plant’s operation through cyber means, or whether it is part of a wider motive to occupy Ukraine (which would require leaving the infrastructure largely operational) or destroy Ukraine (which would not require an operational infrastructure).
This is the primary problem we have in understanding the current and potential future use of cyber in this war. It is impossible to second-guess Putin’s plans (if he has any) or motives (which can change at any time).
What is clear, however, is that the entire globe is under threat of something that could start as a spreading global cyberwar and spill over into a global kinetic and even nuclear war. The two primary ways this could happen is a Russian response to western sanctions, and/or an effect of the uncontrolled activity of non-state ‘patriotic’ hackers on either side.
Sanctions
Sanctions are a delicate balancing act. They must be tough enough to hurt the other side without being so tough they do equal damage to the home market and cause the loss of public support. The current western-led sanctions are tough and could be made tougher if they have no effect.
The International Institute for Strategic Studies (IISS) believes that Putin made a major strategic error in invading Ukraine. He underestimated Ukrainian resistance, he overestimated domestic support, and he united the globe in condemnation of and sanctions against Russia.
“Putin badly underestimated Western cohesion and resolve,” writes Nigel Gould-Davies, senior fellow for Russia and Eurasia at the IISS. “Russia now faces a range of sanctions never inflicted on a major economy, notably the freezing of central bank assets. German policy has undergone a seismic shift: the suspension of the Nord Stream 2 gas pipeline, the exclusion of Russian entities from SWIFT, and the historic decision to send weapons to Ukraine.”
It is Putin’s possible response to these sanctions that is the concern. On Saturday March 5, 2022, he declared that crippling western sanctions are ‘akin to a declaration of war’. Asked what might tip Russia into directing cyber operations against the critical infrastructure of the U.S. and NATO countries, most observers respond with ‘sanctions that he considers too harsh’.
This is a concern. Security observers have been warning for years that adversarial states, including Russia, have been surveilling and embedding themselves within U.S. and European critical infrastructure ‘just in case’. This fear is amplified by the unknown potential that Russian state actors may have been able to make use of the SolarWinds attacks and the Log4j vulnerability of last year. The danger is that Putin may feel that the ‘just in case’ time has come – especially if the sanctions are so severe that he feels he has nothing left to lose.
However, Andras Toth-Czifra, senior analyst of global Intelligence at Flashpoint, suggests that western sanctions policy is to hit Russia so hard and fast that Putin’s political ability to respond is degraded. “It appears that the sanctions strategy aims to extract fast results or precipitate a fast and radical policy change in Russia, relying on the social discontent and the elite fissures that these measures will exacerbate,” he told SecurityWeek. “The risk of the Russian president reacting in an asymmetrical and escalatory manner is present, however, domestic support for the war in Ukraine is thin and is likely to weaken further as the Russian military and the Russian economy suffer heavy losses.”
Dr Danny Steed, lecturer in cybersecurity at Cranfield University, has a similar view. “What should be of great concern to Western nations is how Russia might deploy cyber means as a counter to efforts such as sanctions,” he warns. “With the West clearly not favoring their own military response, the use of sanctions could invite cyberattacks against Western economies as a Russian response.”
So far, it appears as if western agencies have refrained from direct cyber operations against Russia in response to its invasion of Ukraine. Could this be maintained if Russia unleashed major damage in, say, the U.S. with attacks against the CNI? That is unlikely. All ‘western’ nations with a cyber strike capability – notably the U.S., the UK, Australia and possibly Israel would be forced to respond. That is escalation, and there is no knowing where it could lead.
Unfettered patriotic hacker activity
Sanctions are not the only potential cause of an escalation of hostilities beyond the borders of Ukraine. It appears as if Russian state actors are making efforts to target their activities and prevent their malware escaping into the wider world like NotPetya did in 2017. Similarly, western agencies are apparently making efforts to control their own cyber operations. But criminal gangs and individual hackers have neither the same level of discipline nor skills to guarantee that their actions will not escalate the situation. And these gangs and individuals are rapidly taking sides in the conflict.
The Anonymous collective was one of the first. It announced on Twitter on February 24, “The Anonymous collective is officially in cyber war against the Russian government.” Its Twitter feed is now full of claims of hacks and successful DDOS attacks on, and sensitive information leaks from, Russian news and government sites.
Conti was one of the first criminal gangs to side with Russia – but a twist shows the complexity of the situation. On February 27, 2022, Conti issued a warning, “We will use our resources in order to strike back if the well-being and safety of peaceful citizens will be at stake due to American cyber aggression.”
Calvin Gan, Senior Manager at F-Secure’s tactical defense unit, comments, “It has long been known that ransomware groups often have developers in both Russia and Ukraine, and this strong stance from Conti has resulted in their Ukrainian members leaking internal info.” The Conti leaks have been posted by the Ukrainian members to Twitter, starting the day after the ‘warning’ and continuing today.
Security vendors are rushing to analyze these leaks. Malwarebytes warns that it will take a while, but comments, “What we know already is that there is extremely valuable information about the Conti ransomware group, in particular about how they work as an organization and how they target their victims. While Conti is quite resourceful and will probably rebound, there is no doubt that these leaks will cost them a great deal of money and possibly instill fear about their identification as individuals.”
On March 4, 2022, Flashpoint reported that the underground Raid Forums website – notorious for large database leaks – has mysteriously disappeared. There have been no claims for responsibility, but Flashpoint notes that there has been a growing pro-Ukraine sentiment. On the day the invasion began, one of the admins (‘moot’) declared the site would ban all users attempting to connect from a Russian IP address. A day later, Kozak888 leaked a database belonging to a Russian express delivery service. It contained 800 million records including full names, email addresses, and phone numbers. Kozak888 said the database leak was a consequence of Russia’s invasion of Ukraine (the Cossacks are a famed old cavalry with strong ties to Ukraine).
 On February 26, 2022, Mykhailo Fedorov (the minister of digital transformation of Ukraine) announced the recruitment of a private IT army.
On February 26, 2022, Mykhailo Fedorov (the minister of digital transformation of Ukraine) announced the recruitment of a private IT army.
This new civilian IT army is directed via Telegram. At the time of writing this, the Telegram account has 35,483 subscribers. Most will be researchers, journalists and government agents – but there is little doubt that there will be many private developers and hackers wishing to ally themselves with Ukraine.
Apart from individuals, known cyber groups have also been taking sides in the conflict. A character known as CyberKnow has been tracking this development. His (or her) latest update was published on March 4, 2022, with the comment, “This is attempting to capture what the cyber battle space could look like in any conflict.”
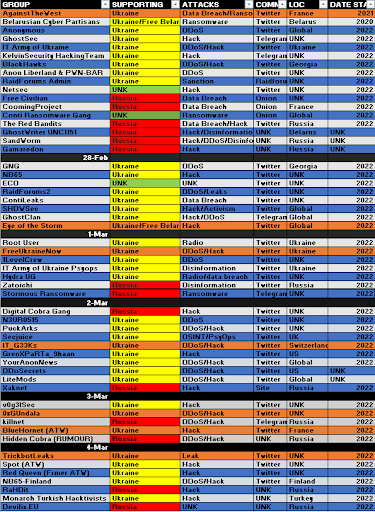 The red and yellow colors indicate the basic affiliations. “The groups in Orange are now inactive on Twitter – they have either shut-down their profiles or, they have been shut-down,” says CyberKnow. What is clear, however, is that the Russia/Ukraine war is having a very polarizing effect among cybercriminals.
The red and yellow colors indicate the basic affiliations. “The groups in Orange are now inactive on Twitter – they have either shut-down their profiles or, they have been shut-down,” says CyberKnow. What is clear, however, is that the Russia/Ukraine war is having a very polarizing effect among cybercriminals.
The danger is that these groups are not centrally controlled, and do not have the discipline, nor most likely the skills, of state actors. The possibility of these independent groups directly attacking the critical infrastructure of the other side, or the accidental leakage of destructive malware such as wipers outside the geographical boundaries of the war zone, cannot be ignored.
Some of these groups may well believe they are protected by the so-called non-attributability of the internet. This is a fallacy. Western intelligence agencies know who the groups are, where they operate, and what they do. However, their false beliefs may tempt them to engage in destructive attacks against US/NATO military and civilian critical infrastructure. This is a major potential for the escalation of cyber activity. How western governments respond to such attacks – if they occur – will be critical.
It is clearly a threat the western powers understand and at least partially expect. “Destructive malware can present a direct threat to an organization’s daily operations, impacting the availability of critical assets and data,” announced CISA. “Further disruptive cyberattacks against organizations in Ukraine are likely to occur and may unintentionally spill over to organizations in other countries. Organizations should increase vigilance and evaluate their capabilities encompassing planning, preparation, detection, and response for such an event.”
In the UK, Lindy Cameron, chief executive of GCHQ’s National Cybersecurity Centre, said: “In a world that relies so heavily on digital assets, cyber resilience is more important than ever… The UK is closer to the crisis in Ukraine than you think… If the situation continues to worsen, we could see cyberattacks that have international consequences, whether intentional or not.”
Corporate response to the situation
Any company anywhere in the world that considers itself too small or too innocuous to be at risk from cyber spillover from this war should reconsider. The speed with which NotPetya spread around the world, and the indiscriminate nature of its victims should be a warning. It is not a certainty that cyber aggression will spread beyond Russia/Ukraine, but it is a distinct possibility.
All organizations should prepare themselves as well and as rapidly as possible. It is the basics that are most urgent – starting with a knowledgeable and aware workforce. Each cyber-aware member of staff is effectively a human firewall.
Beyond that, all patching should be brought up to date as quickly as possible. Anti-malware applications should be maintained at the latest possible version, and set to perform frequent automatic scans.
And, if not already implemented, MFA should be installed and activated as soon as possible.
Related: Russia, Ukraine and the Danger of a Global Cyberwar
Related: Russia vs Ukraine – The War in Cyberspace
Related: Talking Global Cyberwar With Kaspersky Lab’s Anton Shingarev
















