Ransomware can attack data in the cloud and launch attacks on cloud infrastructure
Researchers have discovered a functionality within Office 365 that could allow attackers to ransom files stored on SharePoint and OneDrive. On disclosure to Microsoft, the researchers were told the system ‘is working as intended’. That is, it’s a feature, not a flaw.
It has long been considered that files stored and edited in the cloud are resilient to encryption extortion – the autosave and versioning features should provide sufficient backup capability.
Researchers at Proofpoint have demonstrated that this is a false assumption. They report, “Our research focused on… SharePoint Online and OneDrive… and shows that ransomware actors can now target organizations’ data in the cloud and launch attacks on cloud infrastructure.”
There are two ways this can be achieved through the Microsoft versioning function (which allows the user to specify the maximum number of older versions to be stored). Old versions beyond this limit are by design difficult if not impossible to restore. The first attack is more theoretical than practical, but the second is eminently practical.
The default maximum number of versions of a document that will be stored is 500. The attacker simply edits and encrypts the file 501 times. The edits do not have to be major – just enough to make the system store the new (encrypted) version. By the end of the process, all versions of the document will be encrypted, and the file will be irrecoverable without the decryption key.
This attack is theoretical. In practice it would be noisy and prone to discovery. The second approach is more realistic – use the built-in user-controlled versioning function to minimize the number of stored versions to one. Every document library in SharePoint and OneDrive has a user-configurable setting for the number of saved versions, found within the versioning settings under list settings for each document library.
Setting the version limit to zero doesn’t work for an attacker, because it doesn’t remove existing versions which can still be recovered by the user. But if the limit is set to one, the file only needs to be encrypted twice before its content becomes inaccessible to the user. And if it is exfiltrated prior to encryption, the attacker has the option of initiating double extortion.
The attack chain comprises initial access by compromising or hijacking user identities; account takeover and discovery; versioning reduction, file exfiltration and file encryption; and extortion.
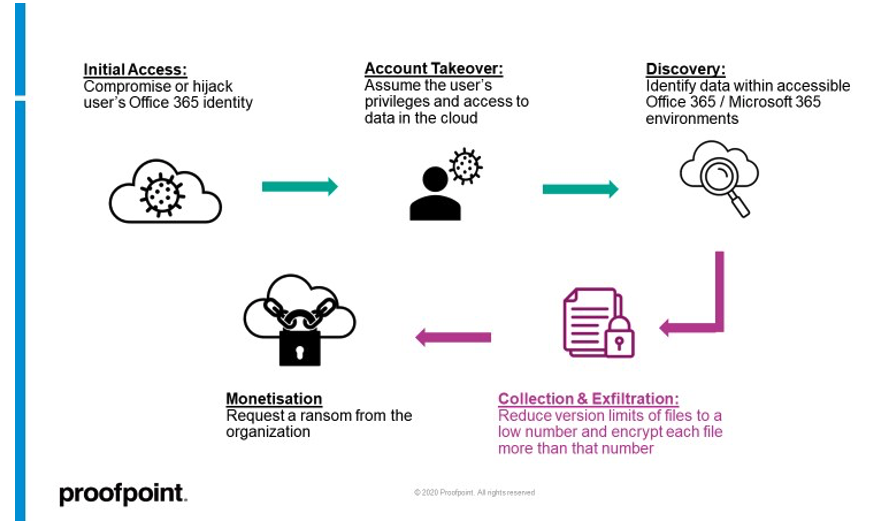
The impact of this attack will be reduced if the file owner maintains a local copy of the file. Here the attacker will need to compromise both the endpoint and the cloud account to ensure success.
Before publicly disclosing what it considers to be a genuine vulnerability, Proofpoint followed the Microsoft disclosure path and reported it to Microsoft. Microsoft responded that firstly, the versioning settings works as intended, and secondly, older versions of files can be potentially recovered and restored for an additional 14 days with the assistance of Microsoft Support.
“However,” write the researchers, “Proofpoint attempted to retrieve and restore old versions through this process (i.e., with Microsoft Support) and was not successful. Secondly, even if the versioning settings configuration workflow is as intended, Proofpoint has shown that it can be abused by attackers towards cloud ransomware aims.”
The moral is simple: do not assume that files stored and edited in the cloud are immune to extortion attacks. Ransomware mitigation controls still need to be in place.
Related: Beating Ransomware With Advanced Backup and Data Defense Technologies
Related: Microsoft Patches Critical SharePoint, Exchange Security Holes
Related: PoC Released for Critical Vulnerability Exposing SharePoint Servers to Attacks
Related: Microsoft SharePoint Vulnerability Exploited in the Wild
















