A team of researchers has described seven new variants of the notorious Meltdown and Spectre attacks, and they claim some of these methods are not mitigated by existing patches, but Intel disagrees.
The Meltdown and Spectre attacks exploit vulnerabilities in Intel, AMD, ARM and other processors. These vulnerabilities, typically related to mechanisms designed to improve performance, can allow malicious applications to obtain potentially sensitive data from a device’s memory.
Researchers initially disclosed three variants of Meltdown and Spectre in early January 2018, but several others were discovered and made public over the next months.
Now, teams from universities in Belgium, Austria and the United States, including some of the experts who were involved in the original Meltdown and Spectre research, have disclosed seven new variants that rely on a method known as transient execution.
One technique used by modern CPUs to improve performance relies on having complex instructions split up into simpler micro-operations. Once each of these micro-operations is processed, the results are committed to the CPU’s architectural state. However, some results are never committed to the architectural state – these are known as transient instructions.
“While the execution of transient instructions does not influence the architectural state and, thus, cannot be observed architecturally, the microarchitectural state can change,” the researchers explained in their paper. “Transient execution attacks exploit these microarchitectural state changes to extract sensitive information by transferring the microarchitectural state into an architectural state. Usually, these attacks use the CPU’s cache, as changes in it can be observed rather easily. However, transient execution attacks are not limited to the cache: any microarchitectural state that can be changed and observed can be used.”
A detailed analysis of transient execution attacks has led to the discovery of two new Meltdown variants: Meltdown-PK (Protection Key Bypass), which affects only Intel processors, and Meltdown-BR (Bounds Check Bypass), which impacts both Intel and AMD processors.
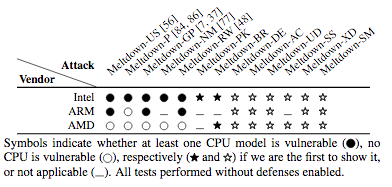
In the case of Spectre, researchers identified five new variants related to Spectre-PHT (Pattern History Table) and Spectre-BTB (Branch Target Buffer). Some of these attacks were found to work on processors from Intel, AMD and ARM, even if exploitation was limited in some cases.
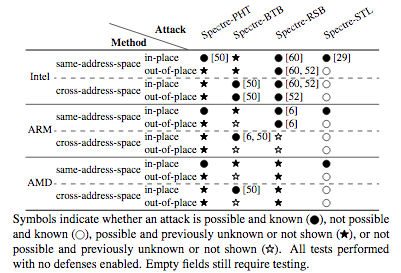
In their paper, the researchers also evaluate existing defenses and claim that they are not successful in mitigating all the attacks they have found.

“Some transient execution attacks are not successfully mitigated by the rolled out patches and others are not mitigated because they have been overlooked,” the researchers wrote. “Hence, we need to think about future defenses carefully and plan to mitigate attacks and variants that are yet unknown.”
Intel, however, told SecurityWeek that if existing mitigations are applied correctly the methods outlined in the research paper should not work.
“The vulnerabilities documented in this paper can be fully addressed by applying existing mitigation techniques for Spectre and Meltdown, including those previously documented here, and elsewhere by other chipmakers. Protecting customers continues to be a critical priority for us and we are thankful to the teams at Graz University of Technology, imec-DistriNet, KU Leuven, & the College of William and Mary for their ongoing research,” Intel said.
SecurityWeek has also reached out to AMD and ARM and will update this article if the companies respond.
UPDATE. ARM also told SecurityWeek that the recent Spectre and Meltdown vulnerabilities identified by academic researchers can be addressed by applying existing mitigations as described in a previously published white paper.














