Researchers at IoT security company ForeScout have created a piece of malware to demonstrate how malicious actors could remotely hack into smart buildings.
Smart buildings have become increasingly common. They rely on building automation systems – including sensors, controllers and actuators – to control heating, ventilation, air conditioning, lighting, surveillance, elevators, and access.
The automation systems that power smart buildings are similar to industrial control systems (ICS), but ForeScout warns that their security should be handled differently given that building automation systems are much more open and interconnected compared to ICS. Furthermore, when it comes to the threats targeting these systems, the final payload is much easier to deliver in the case of building systems as the physical processes involved are less complicated.
It’s not uncommon for researchers to find vulnerabilities in building automation systems from major vendors. However, experts from ForeScout have taken a step further and created proof-of-concept (PoC) malware that shows exactly what it takes to hack a smart building.
Attacks involving building automation systems are not only theoretical. While there is no evidence of malware designed to specifically target these types of systems, there have been some reports of security incidents in the past years. For instance, a luxury hotel in Austria was hit by a ransomware attack that prevented it from creating new keycards. Another example involves a residential building in Finland, which had its heating system disrupted by a DDoS attack.
ForeScout has spent a significant amount of time analyzing building automation systems and its researchers discovered a total of 8 vulnerabilities. Six of them were previously unknown, while two were known by the vendor and had been patched, but their existence had never been disclosed to the public.
The previously unknown vulnerabilities included XSS, path traversal and arbitrary file deletion bugs in Loytec products, and XSS and authentication bypass flaws in EasyIO products. The vendors have released patches after being notified by ForeScout, but these weaknesses have a lower severity.
The most serious issues are the two vulnerabilities that were known to the vendor before they were independently discovered by ForeScout. The company has not been named, but researchers said its products used a hardcoded secret to store user credentials and contained a buffer overflow bug that could be exploited to remotely execute code on a PLC. These two vulnerabilities were leveraged by ForeScout to develop its PoC malware.
The security firm noted that malicious actors have several attacks paths into a building automation network, including via PLCs that are directly exposed to the Internet, or through publicly reachable workstations or IoT devices from which they can move laterally to PLCs. If the targeted network is air-gapped, the attacker needs to have physical access to the building network.
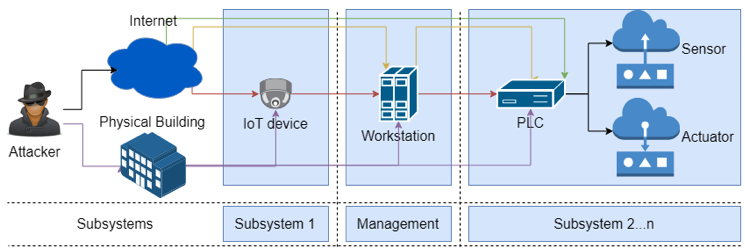
The PoC malware created by the company was written in Go with the final payload developed in Java. The malware was designed to be small (2Mb after being packed) to ensure that it could run on devices with limited space and to make the infection fast and stealthy.
The malware first exploits known vulnerabilities in IP cameras to gain an initial foothold into the targeted network. It then uses misconfigurations and vulnerabilities in various pieces of software to move laterally and identify the targeted PLCs.
The final payload of the malware can, for instance, allow the attacker to manipulate the access control database and add a new user and a new badge to provide them physical access to the building. The attacker can also delete data or simply cause disruption to the building automation systems.
The malware was also designed to clear its tracks by editing log files and ensure that it survives a reboot of the system.
ForeScout says the development of the malware has cost it $12,000, which includes the research and the equipment used for testing.
A search on the Shodan and Censys services for the targeted automation systems revealed nearly 23,000 devices, including over 9,000 that appear to be vulnerable, ForeScout said.
“Although we are aware that achieving the same results in a real life scenario could prove more challenging, especially at scale, we are confident that this is well within the reach of many groups of actors with less positive intentions than ours,” the company said in a blog post.
Related: Unpatched Flaws in Building Access System Allow Hackers to Create Fake Badges
Related: Sauter Quickly Patches Flaw in Building Automation Software
Related: Critical Flaws Expose ABB Door Communication Systems to Attacks
Related: Hotel Rooms Around the World Susceptible to Silent Breach
Related:Flaw in Fingerprint Access Devices Could Make It Easy to Open Doors














