Researchers from Trend Micro say they have identified the piece of malware that appears to have been used in the recent cyberattack targeting the corporate network of Sony Pictures.
The group of hackers that targeted Sony, called GOP (Guardians of Peace), claims to have obtained terabytes of data from the company’s networks, including unreleased movies, business documents and employee information.
The FBI has launched an investigation into the attack, and the agency has sent out an alert to warn organizations of a destructive piece of malware that had been utilized in an attack against a target in the U.S. The FBI memo doesn’t mention Sony as the victim, but experts say the federal law enforcement agency’s five-page “flash warning” describes the attack on the entertainment company.
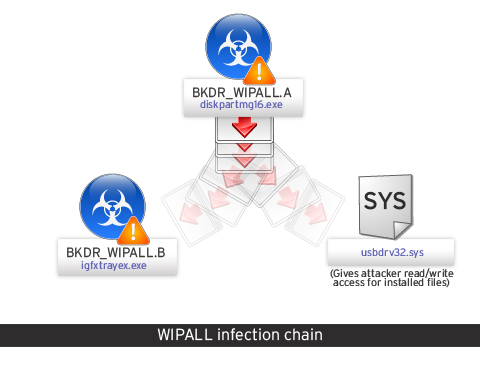
Trend Micro detects the threat as BKDR_WIPALL. Researchers have determined that the attack starts with BKDR_WIPALL.A, which is the main installer and is disguised as an executable file named “diskpartmg16.exe.”
The threat uses an encrypted set of usernames and passwords to log into the targeted organization’s shared network. The goal is to grant full access to everyone that accesses the system root, researchers explained in a blog post.
BKDR_WIPALL.A drops BKDR_WIPALL.B (disguised as a file named “igfxtrayex.exe“), which is the piece of malware responsible for causing damage. Once it’s dropped, BKDR_WIPALL.B sleeps for 10 minutes, after which it starts deleting files and stops the Microsoft Exchange Information Store service. The threat then sleeps for two hours and forces a system reboot.
According to researchers, BKDR_WIPALL.B also executes copies of itself with various parameters to carry out tasks such as deleting files stored on fixed and remote drives, and dropping additional components, including “usbdrv32.sys,” which gives attackers read/write access to installed files.
Trend Micro made the connection between BKDR_WIPALL and the Sony Pictures attack after discovering a different variant, detected as BKDR_WIPALL.D, that is designed to drop BKDR_WIPALL.C. In turn, BKDR_WIPALL.C drops an image file called “walls.bmp,” which is the exact “Hacked by GOP” picture that was seen by Sony employees just before the company’s corporate network was shut down due to the attack.
Reports surfaced last week about a possible involvement of North Korea in the operation against Sony. The attack was believed to be in response to “The Interview,” a comedy about an attempt to assassinate North Korean leader Kim Jong-Un. North Korean officials denied that the country had anything to do with the hack and Sony representatives said the reports were “not accurate.”
On Wednesday, Sony said the “brazen” cyberattack netted a “large amount” of confidential information, including movies as well as personnel and business files.
The investigation into the attack is ongoing, and while Sony has not provided many details so far, the company has hired FireEye-owned Mandiant to help with the forensics aspect of the investigation.
Related: Sony Slams ‘Malicious’ Hack Attack, Mum on North Korea
















