2011 Cost of Data Breach Study Shows Organizations Employing a CISO With Overall Responsibility for Enterprise Data Protection, Paid Less after a Breach, Saving as much as $80 per compromised Record
A report released by Symantec and Ponemon Institute this week, shows that while data breaches can still be costly to an organization, the overall monetary pain dropped in 2011. Now in its seventh year, the most recent report, the “2011 Cost of Data Breach”, showed that both the total overall cost of data breach and the cost per lost or stolen record declined in 2011. Moreover, those with a CISO reported lower costs associated with a breach.
 The 2011 study analyzed the costs incurred by 49 U.S. companies in 14 different industry sectors after those companies experienced the loss or theft of protected personal data and then had to notify breach victims as required by law.
The 2011 study analyzed the costs incurred by 49 U.S. companies in 14 different industry sectors after those companies experienced the loss or theft of protected personal data and then had to notify breach victims as required by law.
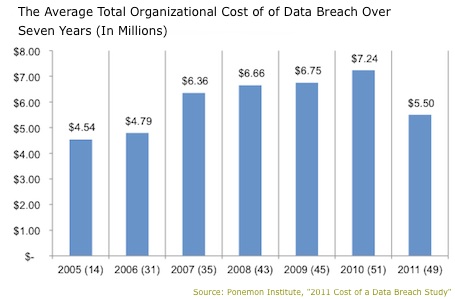
According to the report, the average organizational cost per breach equaled $5.5 million. This is a 24% drop from the $7.2 million reported in 2010, and the lowest average cost since 2007. The cost per record declined from $214 to $194.
The data is built from a rather small sample set, and does not include data breach incidents with more than 100,000 compromised records. This was done in order to prevent the stats from being skewed, the report explains. For example, two massive breaches that occurred in 2011, the Sony PlayStation Breach and the Epsilon breach, would have skewed these numbers significantly.
Along with the good news that costs associated with data breaches has fallen, the number of malicious attacks resulting in a breach fell too. In fact The study also noted that organizations with a CISO tasked with overall responsibility for enterprise data protection, paid less after a breach and saved as much as $80 per compromised record. Those that used an external consultant during the aftermath of a breach had a savings of nearly $41 per record.
“One of the most interesting findings of the 2011 report was the correlation between an organization having a CISO on its executive team and reduced costs of a data breach,” said Dr. Larry Ponemon, chairman and founder of the Ponemon Institute.
“As organizations of all sizes battle an uptick in both internal and external threats, it makes sense that having the proper security leadership in place can help address these challenges.”
With that said, the study does have some down notes.
Organizations that had their first ever data breach spent on average $37 more per record. However, those that acted too fast, and notified customers too quickly without a thorough assessment of the data breach, paid an average of $33 more per record lost. Data breaches caused by third parties or a lost or stolen device increased the cost by $26 and $22, respectively.
“Again, the pattern of results in 2011 is consistent with prior years, when the most costly breaches typically involve malicious acts against the company rather than negligence or system glitches. Accordingly, companies that experience malicious or criminal attacks have a per capita cost above the mean ($222) and companies experiencing negligence have a per capita cost below the mean ($174),” the study found.
Thirty-nine percent of organizations say negligence was the root cause of the data breaches. For the first time, malicious or criminal attacks account for more than a third of the total breaches reported in this study. Since 2007, they also have been the most costly breaches.
Accordingly, Symantec says, organizations need to focus on processes, policies and technologies that address threats from careless and malicious insiders and outsiders. The entire report is online and available here.














