Boston-based Rapid7 has acquired Seattle-based Mobilisafe to add mobile security offerings to its security product portfolio.
![]()
Mobilisafe offers a cloud-based service that helps organizations manage the risks of having employee-owned devices in the enterprise. The acquisition marks the first foray into the mobile security space for Rapid7, the security company behind the popular Metasploit and Nexpose testing frameworks, Mike Tuchen, CEO of Rapid7, told SecurityWeek.
![]()
With the “explosion” of sophisticated phones on the market, more and more employees are using their own personal devices to check their work email and access corporate resources, Tuchen said. Security managers need to understand the risk facing the enterprises by allowing Bring Your Own Device, and Mobilisafe provides that level of visibility, Tuchen said.
“We are really excited about moving into the mobile space,” Tuchen said.
Financial terms were not disclosed.
In conversation with its customers, Rapid7 found that “literally 100 percent” were focused on the mobile security problem, Tuchen said. The fact that Mobilisafe’s platform was simple, easy to use, and powerful at the same time was a unique and attractive combination, he said.
Mobilisafe’s cloud-based risk management solution perfectly complements Rapid7’s existing security assessment and management products, the company said in a statement. Organizations need visibility within their environment to understand the threats they face, manage and prioritize risk, and take targeted action to improve their security. Mobilisafe gives Rapid7 customers that level of visibility when trying to manage the Bring Your Own Device trend, the company said.
Rapid7’s focus on giving defenders the tools to identify relevant threats and prioritize remediation and mitigation effort is “totally in-line with our own view,” Giri Sreenivas, CEO and co-founder of Mobilisafe, said in a statement.
Tuchen was very careful to note that Mobilisafe wasn’t “quite” a mobile device management product, but rather a mobile risk management product, although there was some overlap with what MDM products do.
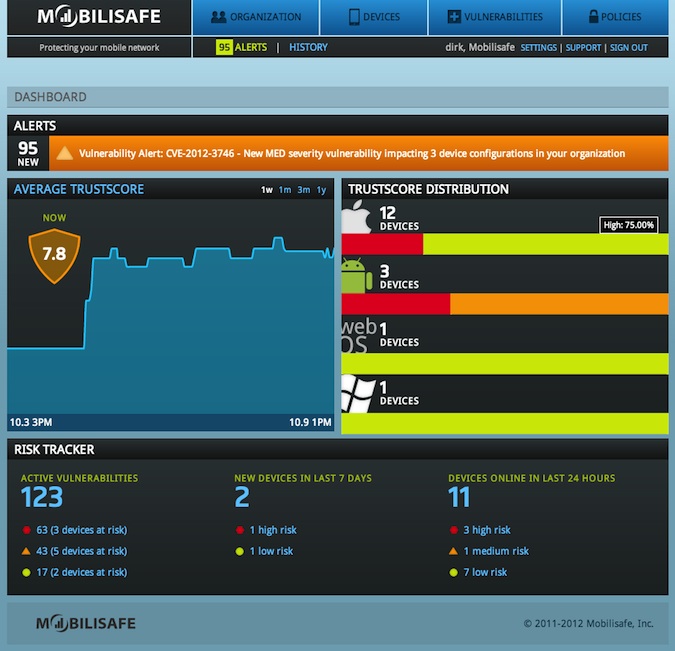
Mobilisafe shows the overall risk of the devices found in the enterprise, what each device is running, as well as what kind of vulnerabilities are unpatched on that device, Dirk Sigurdson, founder and CTO of Mobilisafe, told SecurityWeek. Each device gets assigned a TrustScore, ranging from 1 for worst to 10 for best, to give administrators an overview of how much of a risk that device poses to the organization. With the platform, IT administrators can set policies to allow devices to connect that meet a certain set of security standards to minimize the overall risk, Sigurdson said
“Mobilisafe gives visibility to the company,” he added.
Mobilisafe’s mobile risk management platform will remain a stand-alone product and be rebranded as Rapid7 Mobilisafe, Tuchen said. A free download is available on the Website for anyone interested in trying out the service, and Rapid7 will be reaching out to both Mobilisafe and Rapid7 customers.
Rapid7 has already implemented Mobilisafe internally, and it took “only 15 minutes,” Tuchen said, adding, “it was really easy to deploy.”
Rapid7 announced that it had secured a massive $50 million in funding round in November, 2011.
The combination of Rapid7 and Mobilisafe accelerates the adoption of the product to a larger group of customers, Sreenivas told SecurityWeek.
All seven Mobilisafe employees are expected to remain with Rapid7, and Mobilisafe’s office in Seattle will stay open, Tuchen said.