The function of cybersecurity is not to eliminate all attacks and compromises – that’s impossible – but to make the attack so expensive and time-consuming on the attacker that he simply moves on to an easier target. That is the purpose of a new product/service designed to make commodity ransomware attacks less easy for the attacker.
Security experts at Qualys have analyzed 36 leading ransomware families and their attacks over the last five years. They find that unpatched vulnerabilities, device misconfigurations, internet-facing assets and unauthorized software consistently rank among the top attack vectors.
Leveraging its own VMDR cloud platform and applying the results of its research, Qualys has developed a tailored service – the Ransomware Risk Assessment Service – designed to detect and remediate the most common routes taken by ransomware attacks.
Their researchers isolated the 110 CVEs most used by the criminals in these attacks. In almost all cases, these vulnerabilities have been patched by the vendor, but left unpatched by the victim. For example, the top five CVEs exploited by ransomware gangs are CVE-2013-1493 (used by Exxroute, vendor patched in March 2013); CVE-2013-0431 (used by Reveton, patched in February 2013); CVE-2012-1723 (Urausy, June 2012); CVE-2019-1458 (NetWalker, December 2019); and CVE-2018-12808 (Ryuk/Conti, August 2018).
If these CVEs had been patched by the victims, the attacker would be required to find a different entry point, or just as likely moved on to an unpatched site. As it stands, a Qualys report suggests that just these five CVEs have, through ransomware, “negatively impacted millions of assets across organizations worldwide.”
The importance of patching is well understood – the continued failure of organizations to patch thoroughly is less easy to understand. A study by Trustwave at the end of September 2021 found that despite all the warnings and publicity, more than 20% of the world’s Microsoft Exchange Server installations had not patched the ProxyShell and ProxyLogon vulnerabilities by August 31, 2021. This is concerning. If whitehat researchers can discover these servers, it is certain the blackhat criminals also know them.
So, the cornerstone of the Qualys service is to first locate the existence of these vulnerabilities, and then automatically patch them. This requires complete knowledge of the customer’s IT real estate – a knowledge that many companies do not have. New servers are spun up in the cloud, used for a single purpose (such as testing) and then forgotten and abandoned, but still extant. Other servers are just abandoned in the data center, replaced by newer hardware but still connected to the internet. Anything connected to the internet can be found and exploited by the criminals, but may effectively be unknown to the company.
Part of the Qualys solution includes a global asset discovery and software inventory that locates and identifies all internet-facing assets and unauthorized software to eliminate the blind spots in a company’s security defenses. The necessary patches can then be applied automatically to everywhere they are needed.
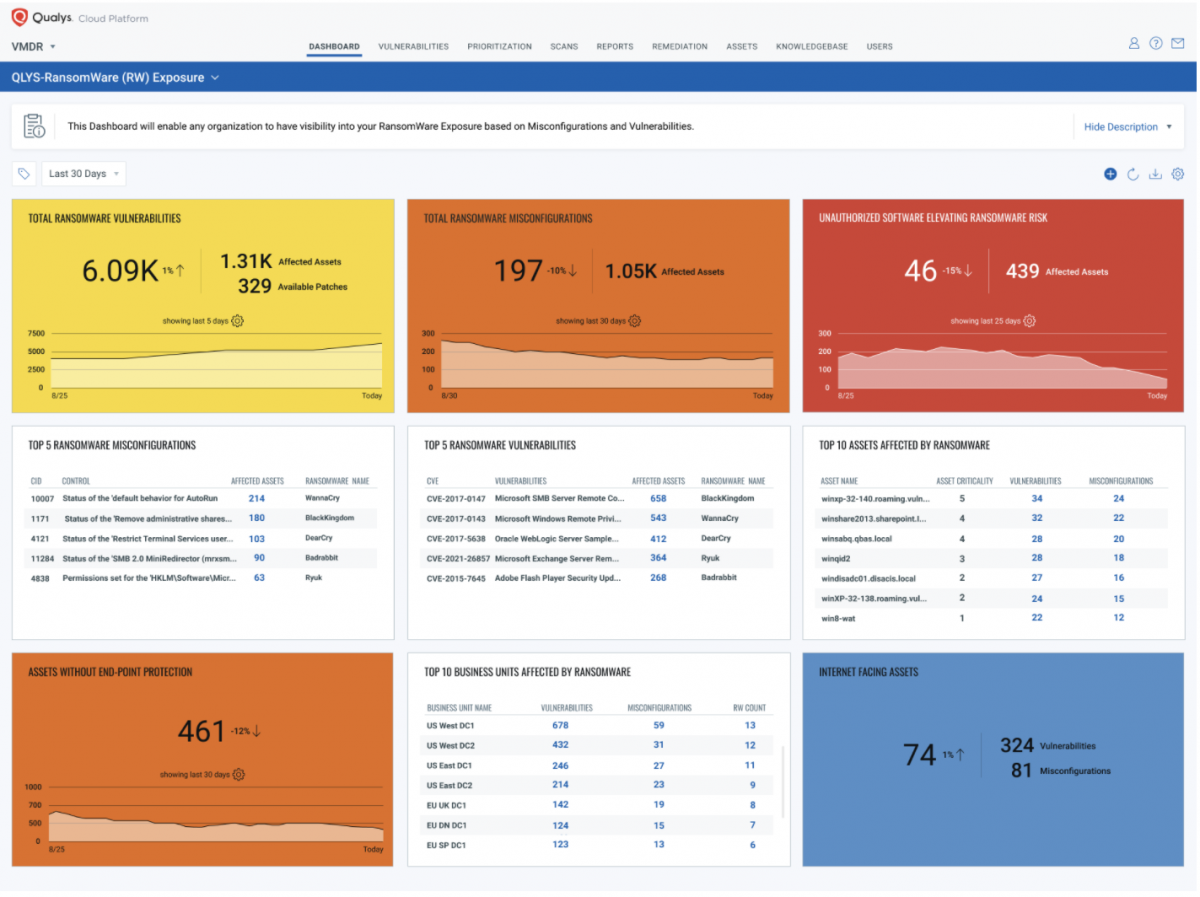
Qualys Ransomware Risk Assessment dashboard
This just leaves misconfigurations as the remaining attack vector leveraged in ransomware attacks. The researchers have isolated the most used misconfiguration, such as insecure RDP and admin shares, and have mapped them to the relevant MITRE ATT&CK techniques. The result is 237 configuration checks across five security areas such as RDP hardening, user controls, network, protocol, and port configuration security, share and password policies and software update policies – enabling companies to shut down 20 of the attack techniques used in ransomware.
“Ransomware risk is top of mind for CISOs who are no longer satisfied with reactive tools and generic guidelines. They want actionable information to reduce risk proactively,” says Sumedh Thakar, president and CEO of Qualys. “The Qualys security team has extensively researched past ransomware attacks as well as CISA, MS-ISAC and NIST guidance and operationalized it into a prescriptive, actionable plan so companies can proactively remediate to stay ahead of ransomware attacks and reduce their overall risk.”
The result is not a solution to ransomware, but a way in which individual companies can harden their systems against ransomware. It is the same principle used in physical policing – a long-standing concept known as CPTED (crime prevention through environmental design). CPTED does not prevent crime delivered by a determined criminal, but it makes it too difficult for the average criminal who will simply move on to a less secure target
“While there is no silver bullet to prevent ransomware, companies can take charge with proactive measures including solid cybersecurity hygiene, patching for known ransomware vulnerabilities, changing configurations and adjusting security policies,” said Jim Reavis, co-founder and CEO of the Cloud Security Alliance. “Qualys Ransomware Risk Assessment puts cybersecurity teams in control by operationalizing government guidelines and providing a company-specific ransomware heatmap so they can eliminate an area of risk and shrink their attack surface.”
The Qualys Ransomware Risk Assessment service, like CPTED, does not eliminate the crime – it is aimed at deflecting the criminal to an easier victim.
Related: CISA Adds Ransomware Module to Cyber Security Evaluation Tool
Related: Two ‘Prolific’ Ransomware Operators Arrested in Ukraine
Related: Links Found Between MSHTML Zero-Day Attacks and Ransomware Operations
Related: FBI: 16 Conti Ransomware Attacks Targeted Healthcare, First Responders in U.S.














