Network-attached storage (NAS) solutions manufacturer QNAP on Wednesday warned users of a DeadBolt ransomware campaign targeting their devices, encouraging them to correctly secure any Internet-facing NAS and routers.
The attacks started only recently, but they already made multiple victims, with many of them heading to QNAP’s forums and Reddit over the past several days to disclose that DeadBolt has locked them out of their NAS device.
After successfully infecting an appliance, the ransomware appends the .deadbolt extension to the encrypted files and hijacks the device’s login page to display a note informing the victim they have been infected and asking for a 0.03 Bitcoin (roughly $1,100) payment in exchange for the decryption key.
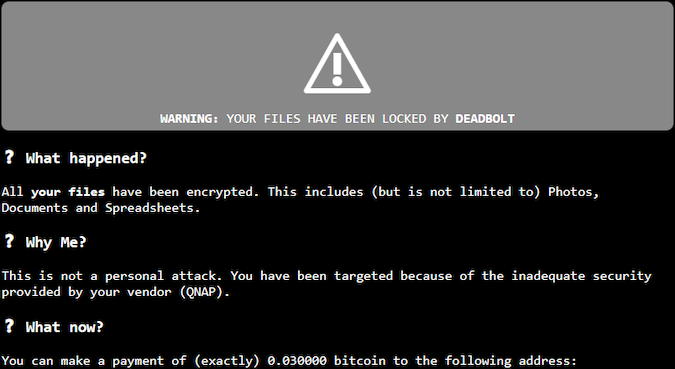
DeadBolt’s operators claim they are exploiting a new zero-day vulnerability in QNAP’s NAS devices, and are asking 5 Bitcoin (worth roughly $180,000) in exchange for information on the security bug.
They also say they are willing to sell the master decryption key for the ransomware (paired with full details on the exploited zero-day), for 50 Bitcoin (approximately $1.8 million).
On Wednesday, the Taiwan-based manufacturer issued an alert to remind users to correctly secure their NAS devices that are directly accessible from the Internet.
“QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP NAS and routers, and immediately update QTS to the latest available version,” the company says.
First, users should check if their NAS is Internet-facing and also verify which ports on their routers are exposed to the Internet. Next, they should disable port forwarding on the router, as well as the UPnP function on the NAS, the company says.
QNAP’s products have long been targeted in ransomware and brute-force attacks and the company has issued numerous warnings of compromise attempts, yet many users continue to leave their devices exposed to the Internet.
Related: QNAP Warns of New Crypto-Mining Malware Targeting NAS Devices
Related: QNAP Patches Critical Vulnerabilities in QVR Software
Related: QNAP Urges Users to Secure Devices Against Brute-Force Attacks













