A new method of launching distributed denial-of-service (DDoS) attacks dubbed “pulse wave” can be highly effective against organizations using “appliance first, cloud second” hybrid mitigation solutions, Imperva Incapsula warned on Wednesday.
The cloud-based security services provider has seen pulse wave DDoS attacks being launched over the past few months, some of them lasting for days and reaching as much as 350 gigabits per second (Gbps).
Typical DDoS attacks show a sawtooth pattern when visualized on a graph due to the ramp-up time needed for cybercriminals to mobilize botnets and reach their maximum potential.
In the case of pulse wave attacks, there is no ramp-up period — the DDoS traffic peaks almost immediately and drops shortly after. The process is repeated at regular intervals, which indicates that the attackers have precise control over their botnets.
Experts believe the malicious actors are capable of switching targets on-the-fly. A web resource can often be disrupted quickly with a powerful DDoS attack, but it can take hours for it to recover. That is why threat groups can launch an attack on one target, then quickly move to a different target, and then return to the initial target. During the time when there is no activity on the graph, the attack is likely aimed at another victim.
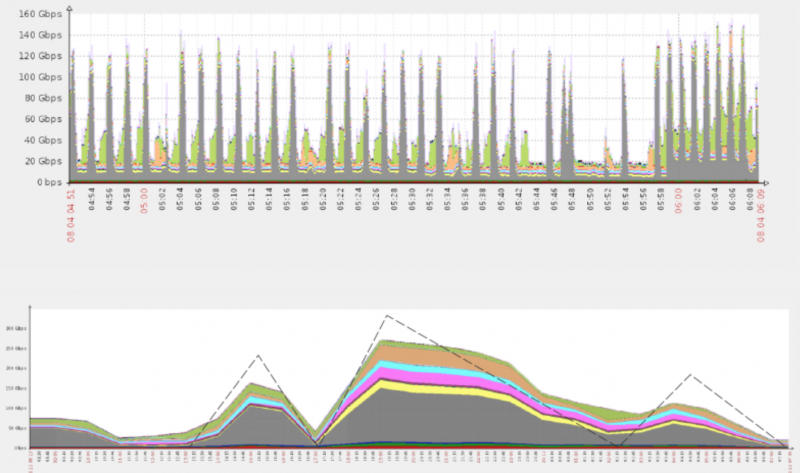
According to Imperva Incapsula, the peak capacity is reached within a few seconds and a new pulse is launched roughly every 10 minutes. Assaults last for at least one hour, but in most cases they can go on for several hours and even days.
Experts believe these types of attacks are particularly effective against “appliance first, cloud second” hybrid mitigation solutions, where on-premises DDoS protection appliances represent the first line of defense and the cloud is used as a backup option for when the appliance cannot handle the attack traffic on its own. The cloud platform is activated by the on-premises appliance, which sends it attack information that can be used to scrub incoming traffic.
The problem is that a single pulse in pulse wave attacks is enough to completely congest a network pipe, causing a DoS condition and preventing the appliance from activating the cloud platform.
“For the pulse duration, the entire network shuts down completely. By the time it recovers, another pulse shuts it down again, ad nauseam. If at some point the cloud is reconfigured to automatically activate itself at the sign of trouble, the scrubbing process is still significantly delayed because of the verification process,” explained Igal Zeifman, director of marketing at Imperva Incapsula.
“Additionally, the lack of communication prohibits the appliance from providing information required to create an attack signature. Even if the cloud does eventually come online, it still has to resample the traffic from scratch before initiating the filtering process,” Zeifman added.
Imperva Incapsula has observed such attacks against several high-value targets, including gaming and financial technology (fintech) companies. The security firm believes other threat actors will likely turn to pulse wave attacks in the future as it provides an easy way for them to double their attack output.
Related: U.K. Student Charged for Running DDoS Service
Related: Don’t Be In Denial About DDoS













