A researcher who discovered many vulnerabilities in Cisco’s Data Center Network Manager (DCNM) product has made public some proof-of-concept (PoC) exploits and technical details.
In early January, Cisco informed customers that it had released updates for DCNM to address several critical and high-severity vulnerabilities.
The vulnerabilities rated critical can be exploited by a remote attacker to bypass authentication and execute arbitrary actions with administrator privileges on the targeted device. Such attacks are possible due to the existence of hardcoded encryption keys and credentials.
The high-severity vulnerabilities can be exploited for SQL injection, path traversal and command injection. While they require authentication, they can be exploited in combination with the critical flaws, which can grant hackers elevated privileges on the targeted system.
The flaws were reported to Cisco by Steven Seeley of Source Incite through Trend Micro’s Zero Day Initiative (ZDI) and Accenture’s iDefense service.
Nearly two weeks after Cisco released patches, the researcher published a blog post describing his findings and also provided PoC exploits for the authentication bypass flaws.
While Cisco only assigned 11 CVE identifiers to the vulnerabilities found by Seeley, the researcher says he has identified well over 100 exploitable bugs. This includes more than 100 instances of SQL injection, four instances of hardcoded keys and credentials, four cases of XML external entity (XXE) injection, two command injections, and 20 file read/write/delete issues.
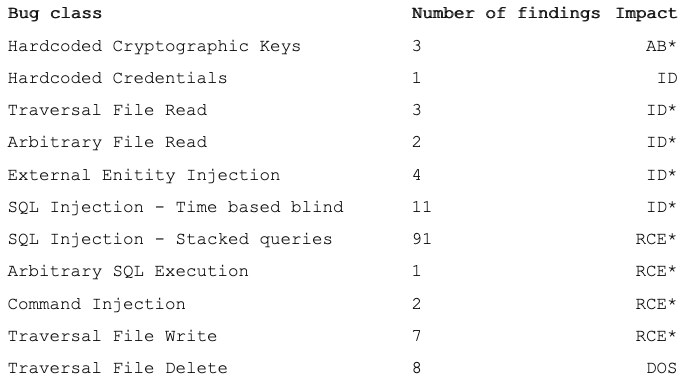
In his blog post, Seeley described three remote code execution chains and various methods that he used for his exploits.
Cisco has updated its advisories to reflect the public availability of PoC exploits.
Hackers have been known to target Cisco systems. The company warned in December that a vulnerability patched in 2018 in its Adaptive Security Appliance (ASA) and Firepower Appliance products had still been targeted in attacks.
Related: Cisco UCS Vulnerabilities Allow Complete Takeover of Affected Systems
Related: Cisco Patches Many Serious Vulnerabilities in Unified Computing Products














