PayPal has fixed a filter bypass flaw and a persistent input validation vulnerability affecting its MultiOrder Shipping application.
PayPal MultiOrder Shipping (MOS) is a tool that helps eBay businesses save time by allowing them to print up to 50 US Postal Service shipping labels at a time directly from their PayPal accounts.
Ateeq ur Rehman Khan, an expert from Germany-based security research firm Vulnerability Lab, is the one who identified and reported the remotely-exploitable vulnerabilities to PayPal.
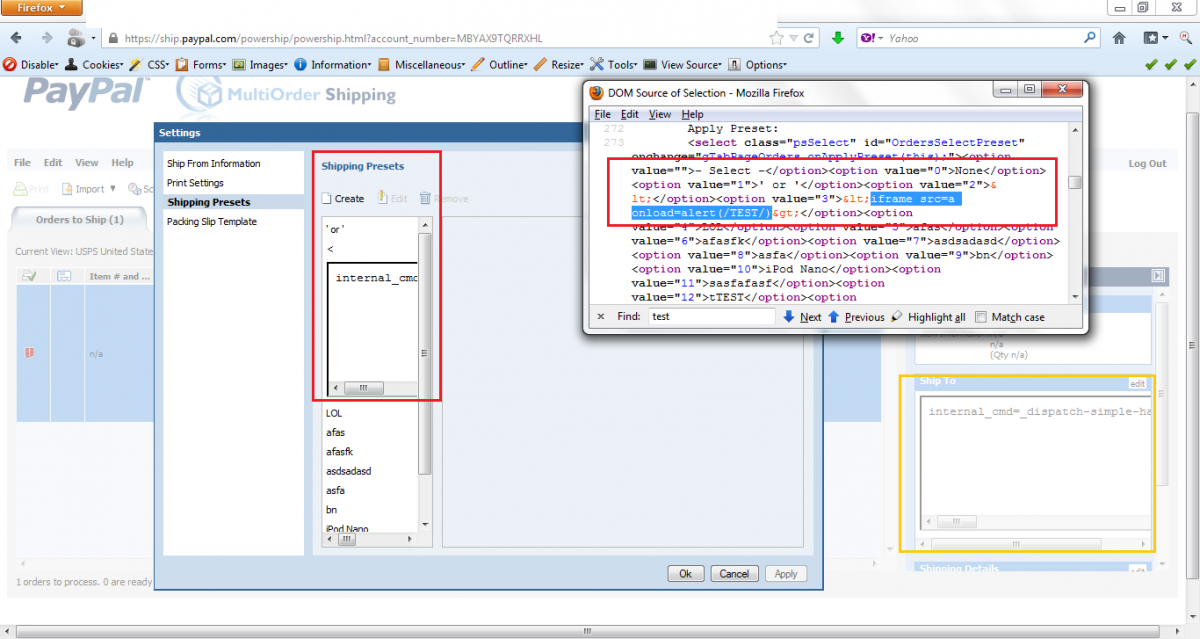
The researcher found a way to bypass security filters by intercepting POST requests and injecting the malicious payload directly without having to use the tool’s Web interface.
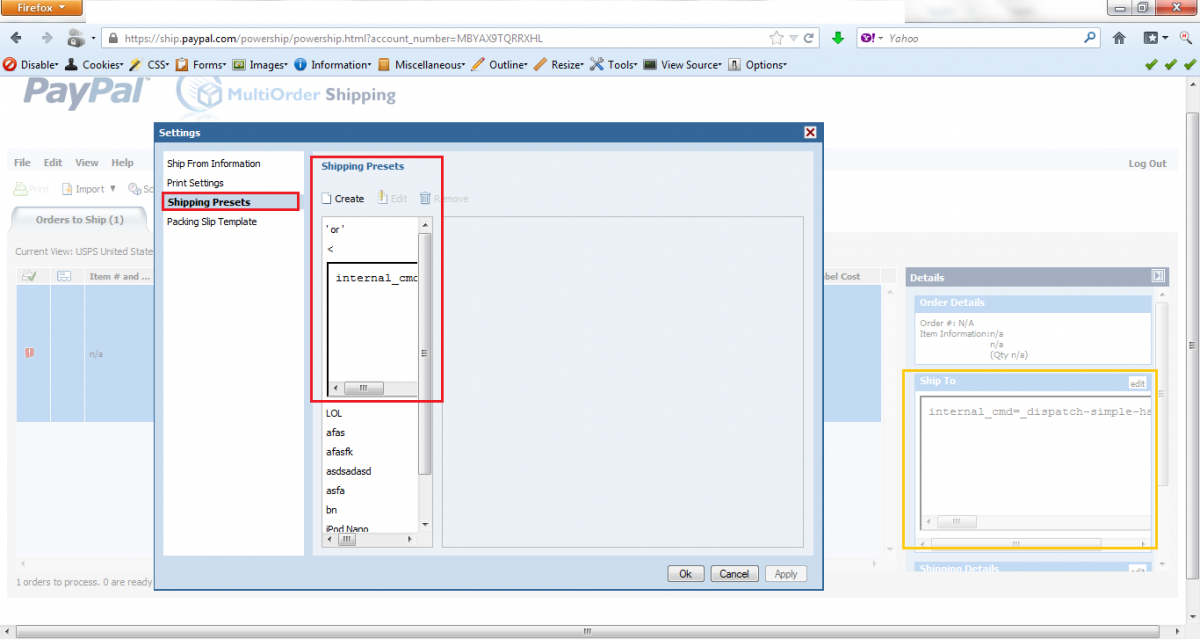
The input validation flaw affected the “Preset Name” field located in the application’s settings menu and it enabled an attacker to inject malicious code. Since the vulnerability was persistent, an attack only required an account with low privileges and limited user interaction.
“The vulnerability is exploitable for stand-alone user accounts but also for multi-accounts in PayPal,” reads the advisory provided by Vulnerability Lab to SecurityWeek. “A remote attacker is able to create multiple customer orders with injected payloads. When the admin merchant account user logs in and checks the Paypal Multi Online Shipping Orders, the exploit gets triggered.”
(Click Images for Larger View)
According to Vulnerability Lab, the flaws could have been leveraged to hijack user sessions, for phishing attacks, persistent external redirects, and persistent manipulation of connected or affected module context.
There’s no evidence that these security holes were exploited in the wild before PayPal fixed them. Vulnerability Lab published a proof-of-concept for this attack only after the issues were addressed.
The vulnerabilities were reported to PayPal in August 2013. However, PayPal confirmed addressing the issues only on May 10, 2014. The security research company published its report on Wednesday.
The payment processor has rewarded $1,000 to the researcher for responsibly disclosing the security holes.