A vulnerability fixed only partially by eBay earlier this month because it was unlikely to be exploited has been leveraged by cybercriminals for phishing attacks and car sale scams, according to UK-based security firm Netcraft.
On February 2, researchers at Check Point disclosed the existence of a vulnerability in eBay that can be exploited for phishing and malware attacks.
eBay allows users to insert active content into item descriptions in their stores, but uses cross-site scripting (XSS) filters in an attempt to prevent abuse. However, experts discovered that by using a technique known as JSFuck, which allows the insertion of a remote JavaScript file into a page using a combination of only six characters (i.e. [ ] ( ) ! +), eBay’s XSS filter can be bypassed.
Check Point has demonstrated that attackers can trick users into handing over their credentials on a phishing page or download malware simply by setting up a malicious eBay store and getting victims to visit it. And since the phishing pages and malware appear to be connected to the legitimate ebay.com domain, many users might take the bait.
eBay said it implemented security filters based on Check Point’s findings and noted that malicious content is highly uncommon on its marketplace. The e-commerce giant also pointed out that it had not seen any fraudulent activity leveraging the vulnerability reported by experts.
However, it appears eBay’s partial fix is not enough to prevent malicious actors from exploiting the flaw. Netcraft reported on Thursday that it had seen several fraudulent eBay listings designed to exploit the vulnerability.
According to Netcraft, cybercriminals have set up their malicious code on compromised eBay accounts, including ones created several years ago and which have a 100 percent positive feedback.
In one of the attacks, the fraudsters copied the content of a genuine listing for an RV sold on eBay three months earlier and posted it on a hijacked store created in April 2010. Users who accessed the post were immediately redirected to a site designed to mimic eBay.
On the fake eBay site, the RV, which had been sold for £19,295 by the legitimate seller, was offered for just £6,300. In this case, the attacker was not after the victim’s eBay credentials and instead attempted to trick users into “buying” the vehicle.
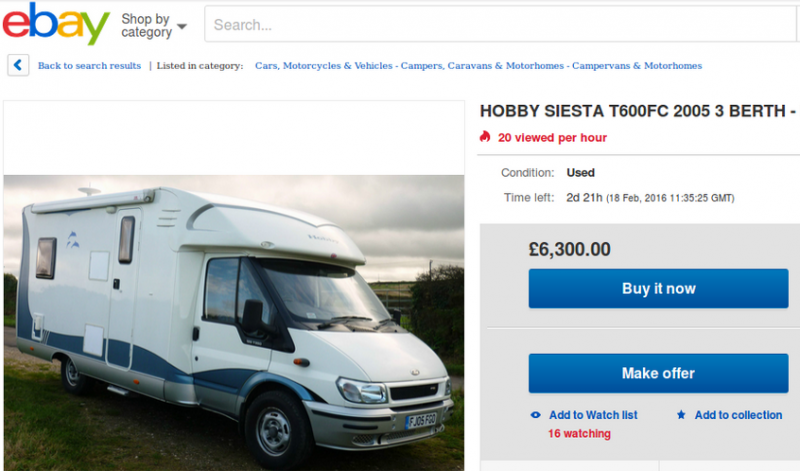
When users click the “Buy it now” or “Make offer” buttons on the fake website, they are simply asked for an email address where the fraudsters will contact them in an attempt to trick them into sending the money for the product via bank transfer. In an effort to make the scam look legitimate and gain their victim’s trust, the cybercrooks also use a fake escrow service.
These types of scams are common on eBay and they have been known to help fraudsters make millions of dollars.
“This particular phishing attack demonstrates some interesting evolutions in the fraudsters’ methodologies. Not only is it rather cleverly launched from the legitimate eBay site, and uses randomly-named files that are deleted to evade detection, but it also tries to avoid leaving any evidence in eBay’s server logs: While all of the pictures used on the spoof auction page are stolen from the earlier legitimate auction, they are either encoded as inline Base64-encoded images, or are served from the fraudster’s own website. This means that no Referer headers will be transmitted to eBay’s web servers, which would otherwise give away the location of the phishing site,” explained Netcraft’s Paul Mutton.
A different eBay posting likely set up by the same fraudster takes victims to another fake eBay website where they are asked to enter their username and password when clicking the “Buy it now” button. The harvested credentials can be used by the attacker to create other fraudulent posts on the victim’s legitimate eBay account, Netcraft said.















