Security researchers with threat intelligence firm Cyble have warned organizations about three new ransomware families named Lilith, RedAlert and 0mega.
Written in C/C++ and targeting 64-bit Windows systems, Lilith appends the “.lilith” extension to the encrypted files, after which it drops a ransom note on the system to demand a payment. The ransomware operators also steal victim data to perform double extortion.
The ransomware features a hardcoded list of processes that it searches for once it is executed on a victim’s machine, and terminates any of those found running, to ensure they would not block its access to the files targeted for encryption.
Targeted processes include those for Outlook, Thunderbird, Firefox, SQL, Steam, and more.
The ransomware also searches for services running on the system, by gaining access to the service control manager database, and then calls specific APIs to take control of target services and stop them, Cyble explains.
Next, Lilith enumerates the system’s drives and gathers information on each of them, after which it searches for files to encrypt by enumerating file directories on the machine.
Victim files are encrypted using a set of cryptographic APIs and a random key generated locally. The encrypted files feature the “.lilith” extension and are used to replace the original files on the disk.
It ignores files with the extensions EXE, DLL, and SYS, as well as a series of directories and file names, including the file that stores the local public key the Babuk ransomware would use for decryption, which might indicate a connection between the two ransomware families.
Before beginning the encryption process, the ransomware drops a ransom note in multiple folders. The note informs the victim they have three days to contact the ransomware operators and negotiate a payment.
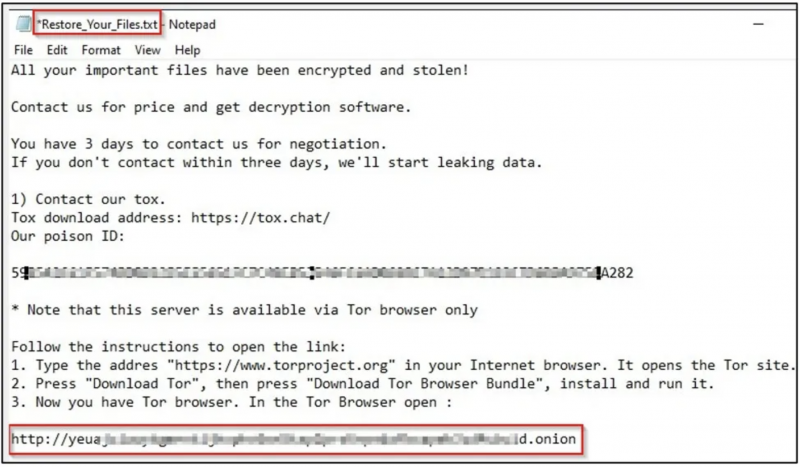
The threat actor also threatens to make the victim’s data public if the ransom is not paid before the deadline. The ransom note also includes a link to a Tor domain that the attackers use as their leak site.
Cyble also warns of an increase in attacks using two rather new ransomware families, namely RedAlert and 0mega. For 0mega, which employs the double-extortion tactic, indicators of compromise have yet to be published.
For the past weeks, RedAlert has been targeting Linux VMware ESXi servers, stopping all virtual machines and encrypting all files related to them. The malware is executed manually, supports multiple pre-encryption commands, and only accepts ransom payments in Monero.
“Ransomware groups continue to pose a severe threat to firms and individuals. Organizations need to stay ahead of the techniques used by threat actors besides implementing the requisite security best practices and security controls,” Cyble notes.
Related: Black Basta Ransomware Becomes Major Threat in Two Months
Related: Researchers Devise Attack Using IoT and IT to Deliver Ransomware Against OT
Related: New Malware Samples Indicate Return of REvil Ransomware















