Global Survey Shows Organizations Struggle to Identify Security Threats and Pass Regulatory Audits
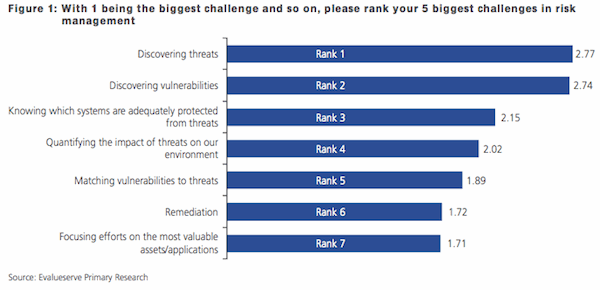
A recent survey revealed that the biggest challenge companies face is identifying security threats, with 41 percent of respondents saying their organization is not well aware of or protected against IT security risks. Additionally, 40 percent of the 353 IT decision makers surveyed said that they are not completely confident they can accurately deploy countermeasure products. These findings come from “Risk and Compliance Outlook: 2011”, a report released today, commissioned by McAfee and conducted by market research firm EvalueServe.
Additionally, respondents appeared to have some insecurities (pardon the pun) with regards to regulatory compliance, with 75 percent admitting they aren’t confident they they will pass a regulatory audit. Audit failure wouldn’t be new to these folks, as more than half said that they have already failed an audit, with nine percent saying that audit failures resulted fines. These results seem to line up well with another recent report, which surveyed Oracle Applications Users Group members and revealed that forty-three percent of respondents were most-concerned with passing compliance audits, however, only fifty-six percent have successfully passed audits most or all of the time, while thirty-six percent are unsure on their standing.
The biggest challenge to comply with these mandates? Databases. Risk and Compliance Outlook survey respondents ranked databases as the biggest infrastructure challenge in terms of complying with regulatory mandates.
But there is good news! The report found that to address these concerns, nearly half of all companies plan to spend an average of 21 percent more in 2011 on Risk and Compliance solutions, indicating strong growth for risk and compliance products in 2011 with the majority of CSO’s and other decision-making executives demanding integrated and automated solutions rather than point products.
Additional Key Discoveries:
• 45% of companies are patching systems weekly
• 25% of the time, compliance is the main driver for initiating an information security project
• 41% of companies indicating they will be investing in Database Activity Monitoring
• 49% of companies stated that they try to ‘over protect’ by patching everything
• 84% of the respondents feel that their business and security operations are impacted due to out-of-cycle patches
• 37% are not confident in knowing which assets need to be patched when a new threat materializes
• 24% of organizations are spending more than $250,000 annually on auditors
• More than 40 percent of organizations get into “fire-fight mode” when a regulatory audit approaches, diverting critical resources away from strategic priorities
• 39% are not confident of being able to translate IT risks into business risks
• 56% of organizations indicated adding “Countermeasure-Awareness” to their risk analysis would provide the biggest benefit
• 60% of the respondents believe that up to 10% of downtime is attributable to unauthorized changes that take place over the entire year
“Organizations are under increasing pressure to protect customer information and privacy, as well as their own sensitive business information, driving the need for a strong focus on risk and compliance management,” said Stuart McClure, senior vice president and general manager of risk and compliance for McAfee. “As the results of this study show, companies recognize the need to improve risk management through better identification of threats, vulnerabilities and countermeasures, as well as the need to improve policy compliance through more automation of IT controls.”
Gary Davis, who manages the Risk and Compliance portfolio for McAfee and is a regular SecurityWeek contributor, suggests that meeting compliance is overrated and that companies should manage risk. “Efficient, effective risk management is the key to ensuring the possible security posture and, by extension, meeting compliance. Too many companies are caught up in a “checkbox compliance” mentality or just “spraying and praying” that they get the threats before the threats get them. As we’ve seen, that approach simply isn’t sustainable,” Davis states in a recent column. “Start a program in your company to gain visibility of threats and vulnerabilities, and put controls in place to mitigate your risks. With the right controls in place—integrated, automated controls that take the guesswork out of when and where to focus security efforts—you’ll be able to boost security and ensure regulatory compliance, while saving time and money,” he added.
Overall, the Risk and Compliance Outlook report suggests that forward-thinking companies are avoiding check-box compliance and fire drill responses to security incidents in favor of sustained, continuous, and auditable risk management and compliance initiatives that address IT security as a business risk.
Responses used to compile the Risk and Compliance Outlook report came from 353 IT decision makers, consultants and security analysts from companies with more than 500 employees who are involved in evaluation, selection, day-to-day management and maintenance of security products. Geographical location of the respondents was fairly even, coming from in Australia, Canada, France, Germany, New Zealand, Singapore, United Kingdom and United States.













