A threat group tracked by Symantec as Orangeworm has been targeting healthcare organizations in the United States, Europe and Asia, but the attacks do not appear to be the work of a nation state.
A report published on Monday by the security firm revealed that Orangeworm was first identified in January 2015. The group has focused on organizations in the healthcare sector, which accounts for nearly 40% of targets, but it has also launched attacks on other industries that are somehow related to healthcare, including IT (15%), manufacturing (15%), logistics (8%), and agriculture (8%).
Specifically, victims in other sectors include medical device manufacturers, IT firms that provide services to clinics, and logistics companies that deliver healthcare products. Researchers say companies outside the healthcare industry have been targeted in supply chain attacks with the ultimate goal of gaining access to the systems of the intended entity.
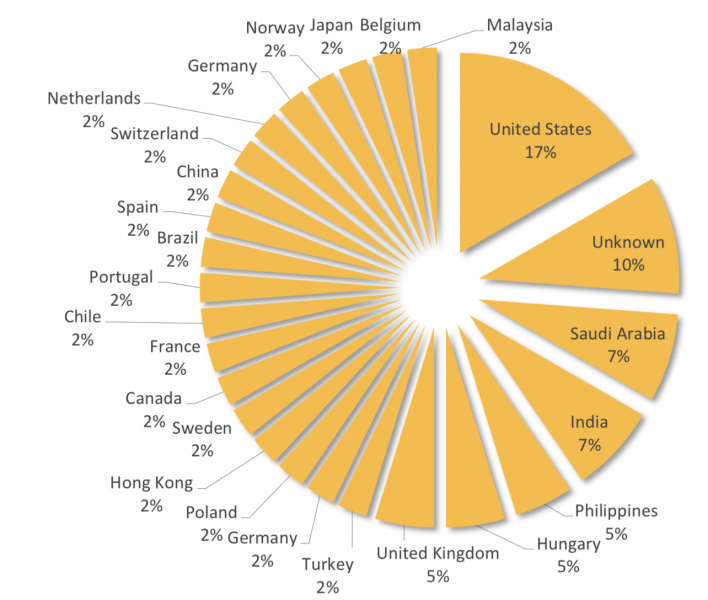
The highest percentage of victims has been spotted in the United States (17%), but Orangeworm has also targeted organizations in Saudi Arabia, India, Philippines, Hungary, United Kingdom, Turkey, Germany, Poland, Hong Kong, Sweden, Canada, France, and several other countries around the world.
“While Orangeworm has impacted only a small set of victims in 2016 and 2017 according to Symantec telemetry, we have seen infections in multiple countries due to the nature of the victims operating large international corporations,” Symantec said in its report.
Once they gain access to the targeted organization’s systems, the hackers deploy a custom backdoor tracked by Symantec as Trojan.Kwampirs. The malware allows attackers to remotely access the compromised machine.
The malware first collects information about the computer to determine if it may be of interest or if it’s a device belonging to a researcher. If the victim is of interest, the backdoor is “aggressively” copied to other systems with open network shares.
Symantec points out that Kwampirs has been found on machines hosting software used for high-tech imaging devices, such as MRI and X-Ray machines. The malware was also spotted on devices used to assist patients in completing consent forms. However, experts say the exact motives of Orangeworm are unclear.
The list of commands sent by the attackers to the malware include instructions for collecting system and network data, and obtaining information on running processes, system services, network shares, account policies, and local and domain admin accounts.
Symantec says it does not have any information that could help determine the threat group’s origins, but the company believes Orangeworm is likely conducting corporate espionage and there is no evidence that the operation is backed by a nation state.
Experts noted that the actors behind Orangeworm do not appear to be concerned about their activities being detected. The method used by Kwampirs to propagate over the network has been described as “noisy” and the attackers have done few changes to the malware since it was first discovered by researchers. The trojan uses an older propagation method that mainly works on Windows XP, but the technique may still work in the healthcare sector, which has been known to use legacy systems on older platforms.
Related: The Latest Strains of Attacks on the Pharmaceutical and Healthcare Sector
Related: Healthcare’s Unique Cyber Risk Management Challenges















