As the saying goes, a chain is only as strong as its weakest link. And in the technology world, while encryption is an instrumental component in protecting sensitive data, encryption is only as strong as its key management.
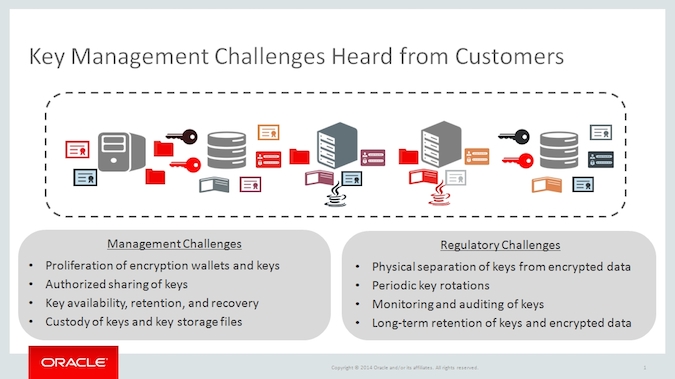
As organizations increasingly encrypt data to comply with regulatory requirements, fend off government snooping, and protect from malicious attackers, managing a growing list of encryption keys and credential files has become a major challenge.
 In an effort to help customers address the challenges surrounding key management, Oracle today introduced Oracle Key Vault, a solution that allows customers to centrally manage assets including Oracle wallet files, Java KeyStores, Kerberos keytab files, SSH key files, and SSL certificate files.
In an effort to help customers address the challenges surrounding key management, Oracle today introduced Oracle Key Vault, a solution that allows customers to centrally manage assets including Oracle wallet files, Java KeyStores, Kerberos keytab files, SSH key files, and SSL certificate files.
Deployed as a software appliance, Oracle Key Vault is the latest addition to the Oracle Database security portfolio and gives enterprises an efficient tool for managing these critical credential that are often scattered across servers.
Resource: Is Your Enterprise Managing Certificates? Three Reasons It Should Be
The new offering puts the database giant in competition with niche key management vendors such as Venafi, Vormetric and Entrust, among others.
Built for x86-64 hardware, the software appliance runs on Oracle Linux and is optimized for the Oracle technology stack, including Oracle Database and Oracle Fusion Middleware.
Oracle Key Vault can be deployed in existing environments, Oracle says, and offers features including:
• Archival and recovery – Archiving Oracle wallet files, Java KeyStores, and other credential files in a master repository, supporting fast, easy file sharing and recovery.
• Centralized management. A browser-based management console offers point-and-click administration, simplified server enrollment, and audit reports.
• Streamlined sharing – Customers can securely share Oracle wallet files across database clusters or disaster recovery environments. The solution currently supports Oracle Real Application Clusters, Oracle Active Data Guard, and Oracle GoldenGate.
• Flexibility – In Oracle Database environments using Oracle Advanced Security with Transparent Data Encryption (TDE), Oracle Key Vault manages TDE keys over a direct network connection as an alternative to a local Oracle wallet.
• Standards Compliance – Based on the OASIS Key Management Interoperability Protocol (KMIP), Oracle Key Vault can manage keys from KMIP-compliant clients.
“Encryption is no longer optional for managing enterprise data. It has become an essential element of end-to-end data protection,” said Carl Olofson, IDC research vice president, Application Development and Deployment.
“Following Heartbleed, every CISO, IT security manager, and incident responder understood the impact of not being able to trust webservers, cloud services, and devices,” Kevin Bocek, VP of Security Strategy and Threat Intelligence at Venafi, told SecurityWeek.
According to recent research, only 3 percent of external-facing servers in the world’s largest companies have been fully protected from the Heartbleed vulnerability, researchers found. In a scan of external servers owned by the Global 2000 companies, 97 percent of the machines were still vulnerable to the OpenSSL flaw, Venafi said in its Q3 Heartbleed Threat Research Analysis report released on late last month.
“From The Mask to Energetic Bear, adversaries of all types are increasingly attacking keys and certificates to gain trusted status to evade detection and expand their attacks,” Bocek said.
“Along with others in the IT security community, Oracle is recognizing the need to secure and protect all types of keys and certificates: from SSL keys and certificates that protect customer privacy for application servers to SSH keys that provide privileged access for apps and admins to virtual machines and cloud services.”
“Organizations’ failure to control and protect keys and certificates, the foundation of digital security and online trust, leaves the front doors open for attackers to enter at will and pilfer whatever sensitive data they want, whenever they want,” Bocek continued. “It’s clear that certificate- and key-based attacks have become the attack vector of choice. As Oracle has acknowledged with this announcement, enterprises must implement effective controls to ensure the safety of their network to avoid attacks, loss of intellectual property, and reputational damage.”
Additional Resources:
• Is Your Enterprise Managing Certificates? Three Reasons It Should Be.













