More than 19 months after it was patched by Drupal developers, a critical SQL injection vulnerability in the popular content management system is still being exploited by malicious actors to hack websites.
The vulnerability in question, tracked as CVE-2014-3704 and dubbed by researchers “Drupalgeddon,” is related to a database abstraction API used in Drupal 7. The flaw allows attackers to execute arbitrary SQL queries, which can lead to privilege escalation or code execution. A patch was released on October 15, 2014.
Just two weeks after the availability of the patch was announced, Drupal warned users that all installations should be assumed compromised unless the fix was applied within 7 hours after its release.
Even today, there still are some organizations that haven’t patched the vulnerability. For instance, a version of Drupal plagued by this flaw had powered a customer portal of Panama-based law firm Mossack Fonseca, from which hackers recently leaked millions of emails, databases, images and documents.
Web security firm Sucuri has been monitoring attacks targeting CVE-2014-3704. According to the company, after the initial attacks in October and November 2014, when thousands of websites were targeted, the number of attacks dropped, but remained consistent throughout 2015 and 2016.
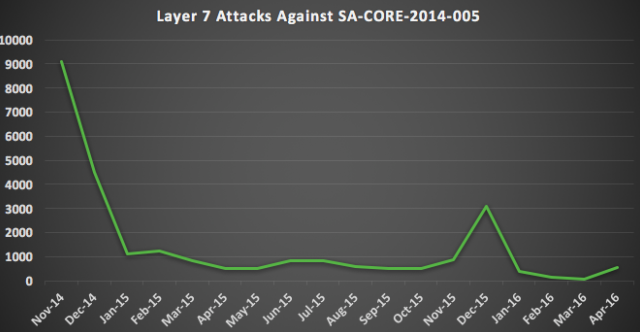
“If someone had not patched, they are surely compromised now. But that doesn’t stop attackers from trying to find new entry points and even compromise already compromised sites,” Sucuri explained in a blog post on Tuesday.
In most cases, malicious actors have leveraged the SQL injection vulnerability to create new admin accounts on Drupal websites, including ones named Derevos, Holako and Mr.R00t2_404. It’s unclear what attackers are doing once they gain access to these sites because Sucuri blocked all the attempts it detected before hackers could cause any damage.
However, the security firm noted that it has observed an increase in SEO spam attacks against Drupal 7 websites.
Related Reading: Critical Drupal Updates Patch Several Vulnerabilities
Related Reading: Drupal Starts Patching Update Process Flaws
















