“It’s not the daily increase but daily decrease. Hack away at the unessential.”–Bruce Lee
The rapid growth of innovation in cybersecurity technologies has presented a nearly endless range of new security offerings to address vulnerabilities in our computing environment. But what happens if more is not better?
In the data center and public cloud infrastructure world, the layering of technology at the perimeter—sometimes called defense in depth—has a followed a progression from the perimeter firewall to IDS/IPS to APT technologies, just to name a few waves of innovation. While all are important building blocks in protecting the data center edge, an increasing amount of attacks come from the inside out, not the outside in. Human error, malware, and hackers have presented a growing recognition that more focus is needed on the inside of the data center.
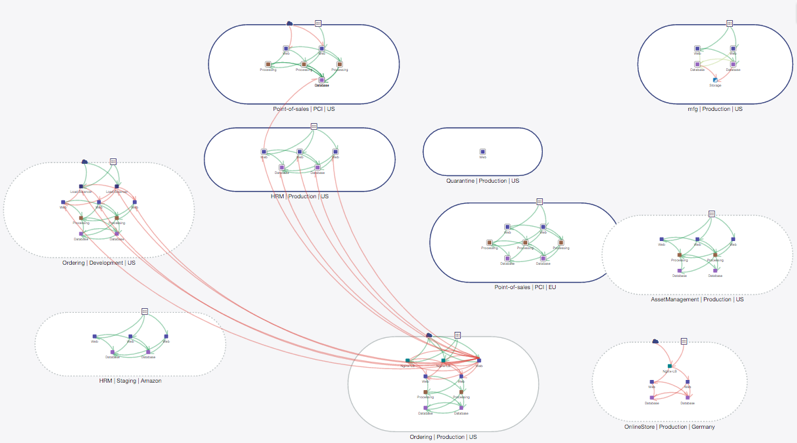
Take the diagram below: can you find the offending server? Would perimeter security technology capture an attempted port scan within the data center interior?
So we should put more technology inside, right? Maybe not.
One of the key security insights the past decade has shown is that adding more technology—particularly adding more layers of infrastructure technology inside the data center—may actually create more harm than good. To wit, if you spoke to any CISOs at the recent RSA conference (warning: tongue-in-cheek comment ahead) they can feel as much under siege from new vendors as from bad guys.
Organizations already have a large amount of infrastructure and security technology to manage. Infrastructure technologies like firewalls create both complex traffic steering as well as “policy debt.” Ask a large business about its firewall rules: how many do you have? How often do you decommission out-of-date rules/policies? How do you feel about the things you do not know? Trust me, this is rarely a pleasant conversation.
If a company is at least 25 years old, its infrastructure is a little like Rome: it is built on layers of technology.
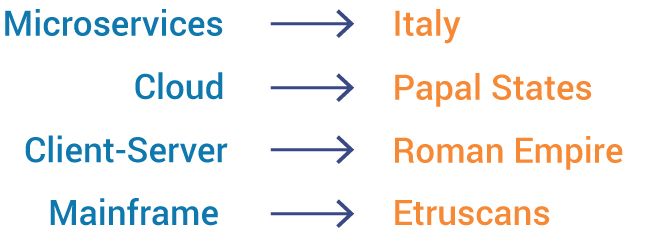
Visiting Rome, you can see many examples of how one society builds on top of the previous (on your next trip, take a look at Bernini’s Elephant outside of the Hotel De Minerve near the Pantheon). If you look in a modern data center, you will see the multiple layers of technology co-existing as well.
One common refrain now is to virtualize your compute stack to better protect it (i.e., gain isolation and security from the hypervisor). There are a lot of good operational benefits to running software on virtual machines, but is rewriting and migrating your servers the right answer all of the time? What happens if you want to move from bare metal to containers and skip the virtualization step? In the past, applications had to fit the infrastructure—remember WinTel, when Intel created a chip and Microsoft figured out how to maximize its utilization.
Today it is the opposite, security and infrastructure vendors now have to chase applications, not the reverse. The computing world is too complex, too heterogeneous for today’s infrastructure-only security answers. I might use bare metal for transaction processing, VMs in the cloud for web servers, and containers for my development organization. How does security work across those environments?
Security technologies that force more—or lock in existing—infrastructure into the data center are increasingly untenable as computing evolves along with the notion of what a data center is (e.g., AWS, Azure, Google Compute).
It is time to look at ways to take advantage of what already exists, rather than always adding an additional layer of complexity that has to be managed. If I add more chokepoints, including virtual devices, I add more things to be managed and more traffic that requires steering. How does this help over-taxed infrastructure and security teams keep up?
What happens if I can activate security controls that are already available everywhere inside my data center and cloud, then marry them to my other security investments? By utilizing security technologies that are “invisible” to the infrastructure, I can reduce, rather than add to, IT and security’s burdens. What happens if my compute plant became an activated citizenry in its own protection?
Using security technologies that activate existing security controls rather than simply layer in new devices follows Occam’s Razor, the teachings of a 14th-century English logician who suggested entities should not be multiplied unnecessarily. Simply said, less is more.
Coming up next, An Occam’s Razor for Security Part 2…













