Web Application Security gurus, WhiteHat Security, released a report this week that examines the severity and duration of Web application security related vulnerabilities discovered in 2011. When the numbers are stacked against those from similar reports published since 2007, the number of major vulnerabilities has fallen dramatically.
![]() WhiteHat’s numbers come from scans performed on approximately 7,000 websites in a wide range of vertical markets. The notion of a substantial vulnerability, for clarity, are those with a high, critical, or urgent ranking as defined by PCI-DSS. This most recent report represents the largest amount of data that they’ve ever studied, and the number of websites scanned for the data is twice the amount of last year’s study.
WhiteHat’s numbers come from scans performed on approximately 7,000 websites in a wide range of vertical markets. The notion of a substantial vulnerability, for clarity, are those with a high, critical, or urgent ranking as defined by PCI-DSS. This most recent report represents the largest amount of data that they’ve ever studied, and the number of websites scanned for the data is twice the amount of last year’s study.
Based on the raw data, there were only 79 substantial vulnerabilities discovered on average in 2011. To compare, there were 230 vulnerabilities on average discovered in 2010, 480 in 2009, 795 in 2008, and 1,111 in 2007.
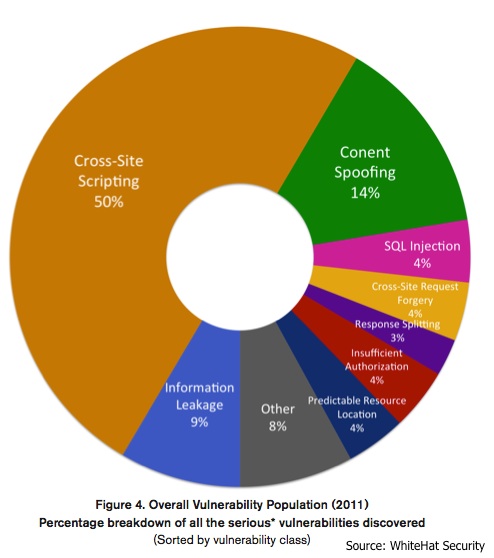 As for the types of flaws discovered, Cross-Site Scripting (XSS) remained the number one problem, followed by Information Leakage, Content Spoofing, Insufficient Authorization, and Cross-Site Request Forgery (CSRF) flaws. SQL Injection, an often mentioned attack vector online – was eighth on the top ten.
As for the types of flaws discovered, Cross-Site Scripting (XSS) remained the number one problem, followed by Information Leakage, Content Spoofing, Insufficient Authorization, and Cross-Site Request Forgery (CSRF) flaws. SQL Injection, an often mentioned attack vector online – was eighth on the top ten.
While the decline is a positive thing, the problem is a persistent one that needs monitored. As the report explains, WhiteHat researchers discovered that while organizations were quick to remediate high-level problems, “the higher the severity of vulnerability, the more likely the vulnerability would reopen in the future.”
“While there are likely to be a number of causes, one likely explanation is a deficient ‘hot-fix’ process. This is when a high-severity vulnerability is fixed quickly, live on the website, but the change is back-ported to development, and a future software release overwrites the patch.”
Point in case, 26% of the SQL Injection flaws and 24% of the XSS flaws were reopened after they were previously patched. Another related note of interest from the report is that vulnerabilities exploited by injecting malicious data into URL parameters tend to reopen more often than business logic flaws. Overall, 20% of the vulnerabilities identified by WhiteHat’s Sentinel scans were reopened at some point in time, some of them several times.
As for the industry comparison, banking finished on top with an average of 17 vulnerabilities, while retail remained on the bottom with 121. In addition, the energy and manufacturing sectors earned top marks for fixing their flaws the fastest. Overall, the entire report is worth reading, as it is one of the few with measurable real-use data.
Web Application Firewalls are making a positive impact
WhiteHat reported on the positive impact Web Application Firewalls (WAFs) are having, mainly because of their ability to mitigate particular vulnerability classes such as Cross-Site Scripting, Content Spoofing, SQL Injection, and Response Splitting. According to WhatHat’s numbers, a WAF could help mitigate the risk of at least 71% of all custom Web application vulnerabilities.
The full report can be found here.
Related Reading: Web Application Firewalls – Three Benefits You May Not have Considered
Related Reading: Why Web Application Firewalls Are Not the Enemy of the SDLC













