With no bad behavior, the mobile apps are difficult to detect by automated security scans
Between March 2020 and March 2021, the value of bitcoin rose from $6,483 to $58,734 (Statista.com). The value is roughly $32,500 at the time of publishing. There’s money in cryptocurrency; and where there’s money, there’s criminals.
Researchers at mobile security firm Lookout have identified more than 170 Android apps that target and scam users interested in cryptocurrencies. Twenty-six of these were found on the official Google Play store — the remainder on third-party stores.
The apps are hardly sophisticated — but scams don’t need to be sophisticated, they just need to work. These work. The Lookout researchers report that the apps have scammed more than 86,000 people, and have stolen at least $350,000.
These apps cannot even be classified as ‘malware’ since they do nothing typified as malicious and don’t contain a payload. This is the height of their sophistication. With no bad behavior, they are difficult to detect by automated scans.
The purpose is solely to steal money through legitimate payment processes. The services paid for are never, of course, delivered. “If there is any kind of media hype happening — such as the rise in cryptocurrency values — the bad guys are going to jump on it no matter what it is,” Christoph Hebeisen, director of security intelligence research at Lookout, told SecurityWeek. “They will do that by any means possible. Here they have been innovative by going after users via an Android app.”
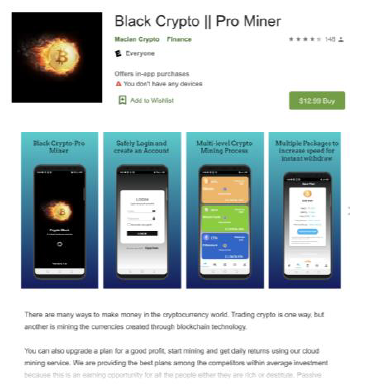 Lookout classified the apps it discovered into two families: BitScam and CloudScam. Despite technical differences, the two families use the same business model — something Hebeisen describes as ‘convergent evolution’ rather than an indication of any relationship between the app authors.
Lookout classified the apps it discovered into two families: BitScam and CloudScam. Despite technical differences, the two families use the same business model — something Hebeisen describes as ‘convergent evolution’ rather than an indication of any relationship between the app authors.
The BitScam apps are put together using an app builder framework that requires no programming experience or understanding of how an app actually works. “We have seen this framework used for nefarious app development before — such as adware,” said Hebeisen;” “but again there is no malicious code included. The whole purpose of using the framework is to make use of a business operation rather than to develop malware. It is perfectly possible that this approach to scam development will increase in the future.”
However, he added, “The distinction between frameworks and SDKs is beginning to blur, and as the frameworks improve and JavaScript is included, it is possible that this basic method will be used to generate true malware in the future.”
The CloudScam apps are built in Java, by someone with some coding expertise. Both app families offer (but neither deliver) crypto mining services — a legitimate occupation that appears more attractive as the value of cryptocurrencies increases.
The apps are ‘paid for’, giving the criminals the bulk of their income. “Both CloudScam and BitScam also offer subscriptions and services related to crypto mining that users can pay for via the Google Play in-app billing system,” note the researchers.
This area of income is diminishing, however, since it only applies to the apps purchased from Google Play; and these were rapidly removed when Lookout reported its findings. The BitScam family, however, provides an option to buy ‘virtual hardware’ in the cloud to increase the rate of mining. The cost ranges from $12.99 to $259.99, and can be paid either through Google Play (if available) or by transferring bitcoin and/or Ethereum to the developer’s wallet.
Crypto mining scams have already been discovered in PC apps — indeed, the bravenewcoin website warns, “Crypto scams are at an all-time high, so tread carefully.” The Lookout findings are the first time such scams have also been found in mobile apps.
To maintain the fiction of actual mining, and to persuade victims to pay for additional in-app upgrades for additional subscriptions and services, the mobile apps display a fictitious coin balance for the user. This is nothing more than a simple counter slowly incremented over time.
“In some of the apps analyzed,” comment the researchers, “we observed this happening only while the app is running in the foreground and is often reset to zero when the mobile device is rebooted, or the app restarted.” In some apps, user attempts to withdraw the fictitious balance are met with a message saying ‘pending’, while the counter is reset to zero; or that the balance is too small to withdraw. There is, of course, nothing to withdraw.
Some mobile security products (such as Lookout’s own) can detect these scam apps. But because they contain no malicious code, nor engage in malicious activity, this is not always so. Either way, if a user’s security detects the app as a scam, it is possibly already too late — the user has already paid the criminal.
“One of the best defenses,” Hebeisen told SecurityWeek, ” is to check the online reviews before paying for or downloading an app. Some of these will be false, glowing, planted reviews. But if you also see a pattern of complaints saying things like ‘I cannot download the balance’, or ‘the balance value keeps reverting to zero’, then you know there is something wrong here.” As always with Android apps, he adds, “It is a case of ‘buyer beware’.”
Related: Cryptocurrency Fraud: In the Midst of a Gold Rush, Beware of Scammers
Related: Fake Netflix App Luring Android Users to Malware
Related: Lookout Raises $150 Million to Grow Enterprise Mobile Security Business
Related: Kubeflow Deployments Targeted in New Crypto-mining Campaign












