Trusteer’s new exploit prevention platform protects enterprises from zero-day and social engineering attacks from successfully compromising endpoints.
Called Trusteer Apex, the platform blocks sophisticated attacks from exploiting unpatched vulnerabilities in widely deployed client applications to download malware, Trusteer said. The platform is designed to detect when an attempt to write to the machine or download something is not part of standard operations or behavior, and prevent the action from succeeding, Mickey Boodaei, CEO of Boston-based Trusteer, told SecurityWeek.
Attackers are increasingly crafting sophisticated campaigns exploiting vulnerabilities in Web browsers, Adobe Acrobat, Flash, Java, and Microsoft Office. These attacks rely on malicious Web pages, spear phishing emails, and weaponized documents to compromise endpoints and gain a foothold inside the enterprise network.
“Advanced malware protection continues to be a losing battle for enterprises because malware is constantly evolving to evade detection. Current security controls require constant care that enterprises simply cannot afford,” Boodaei said in a statement.
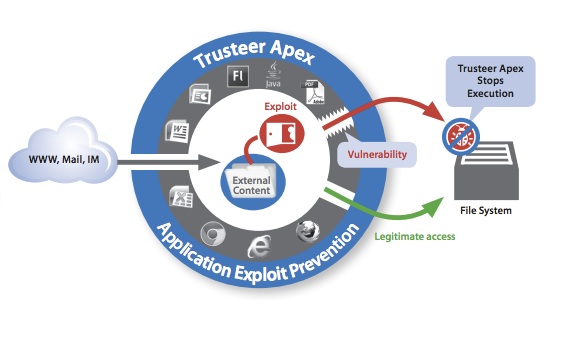 Apex is different from traditional blacklisting and whitelisting technologies. Cyber-criminals are constantly changing their tactics to evade detection, making it difficult to keep the blacklists up-to-date with the newest tricks. Whitelists, which allow only the “known good” applications to execute, are difficult to manage.
Apex is different from traditional blacklisting and whitelisting technologies. Cyber-criminals are constantly changing their tactics to evade detection, making it difficult to keep the blacklists up-to-date with the newest tricks. Whitelists, which allow only the “known good” applications to execute, are difficult to manage.
Trusteer Apex monitors endpoint applications and analyzes what every single process is doing, what it is interacting with, and what code is being executed, Yishay Yovel, vice-president of marketing at Trusteer, told SecurityWeek.
Trusteer Apex associates operations the application is running with appropriate processes. This way, every action taken by the application is placed in context, so the product can tell the difference between Internet Explorer legitimately downloading a new executable as part of an update operation versus stealthily downloading malware by exploiting the unpatched vulnerability in the browser, Yovel said.
Apex’s technology automatically terminates an application exploitation process by stopping applications from performing out-of-context operations, Trusteer said. With this platform, malicious code embedded in Web pages and business documents cannot trigger vulnerabilities in client applications and download malware.
The platform also restricts untrusted files from executing sensitive operations that are potentially malicious. Untrusted files are sent to Trusteer for further analysis and if determined to be malicious, are automatically removed from the endpoint.
Trusteer has worked over the years with financial institutions around the world to help protect banking customers from sophisticated and evasive malware attacks, Yovel said. Rapport, Trusteer’s client application, scans the customer’s computer for malware and protects the user’s online banking session. Trusteer used the insights and expertise gained in monitoring client applications to develop Trusteer Apex, Yovel said.
Trusteer Apex can be deployed quickly, taking mere days to roll out to tens of thousands of managed and unmanaged endpoints, the company said. Designed specifically for large and complex environments, Trusteer said the platform doesn’t require a learning period or ongoing configuration.
“With Trusteer Apex, enterprises can protect themselves against exploitation of the constant flurry of application vulnerabilities and stop data exfiltration with zero management effort,” Boodaei said.















