A researcher has conducted an analysis to see how major companies could track user activity through their mobile in-app browsers, and released a free and open source tool that allows anyone to check what code is being injected by such browsers.
Some mobile applications use built-in browsers to allow users to quickly access third-party websites. Other apps include a browser to load their own resources, which may be needed to perform various activities. However, these internal browsers could also pose security and privacy risks.
Researcher Felix Krause published a blog post earlier this month claiming that the iOS apps of Instagram and Facebook could monitor everything a user does on an external website opened through the application’s internal browser. This claim was based on the JavaScript code the applications inject into the website displayed by the in-app browser.
Later tests showed that TikTok also injects JavaScript code that modifies the content of the third-party websites opened through the social media app. TikTok appears to monitor all keyboard inputs and screen taps, potentially allowing the company to collect passwords and other sensitive information entered via the built-in browser.
Meta said the code is being injected as part of an App Tracking Transparency (ATT) mechanism that helps the company respect users’ privacy choices. TikTok confirmed that the keylogging code exists, but said it’s not actually being used.
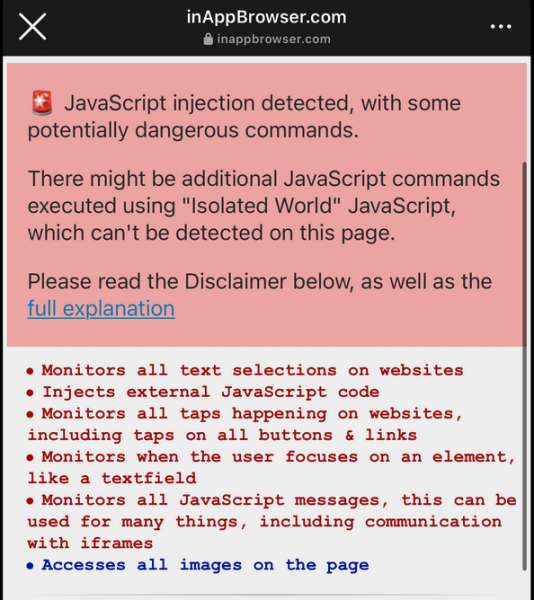
However, Krause says his analysis highlights the potential security and privacy risks associated with JavaScript code getting injected by in-app browsers into third-party websites. That is why last week he released a free and open source tool that anyone can use to check what code is being executed through these in-app browsers.
The online tool, named InAppBrowser, displays the JavaScript code that is injected when the website inappbrowser.com is opened with an in-app browser. It also provides information on what each command does.
While the tool can provide some useful information, Krause pointed out that it cannot detect all the JavaScript executed by the browser and it also does not provide any information on the tracking mechanisms implemented using native code. In addition, some applications can hide their JavaScript activities, including by using Apple’s WKContentWorld object, which is designed to separate the app from the webpages and scripts it executes.
On the other hand, the researcher noted, “Just because an app injects JavaScript into external websites, doesn’t mean the app is doing anything malicious. There is no way for us to know the full details on what kind of data each in-app browser collects, or how or if the data is being transferred or used.”
Users who are concerned about the potential risks should always open websites in their phone’s browser rather than the in-app browser. Popular apps often provide the ‘Open in browser’ option for this task, or users could simply copy and paste the URL.
Krause also noted that some iOS apps follow Apple’s recommendation and use Safari or the Safari view controller for accessing external websites, and this prevents them from injecting their own code.
The InAppBrowser source code is available on GitHub. The app can work for both Android and iOS applications.
Related: Apple to Tighten App Privacy, Remove Apps That Don’t Comply
Related: Google Details New Privacy and Security Policies for Android Apps
Related: Google Introduces ‘Privacy Sandbox’ for Ads on Android













