The CERT Coordination Center (CERT/CC) at Carnegie Mellon University this week announced the launch of a new version of the network traffic analysis tool CERT Tapioca.
CERT Tapioca was first released in 2014 as a network-layer man-in-the-middle (MITM) proxy virtual machine designed for identifying apps that fail to validate certificates and investigating the content of HTTP and HTTPS traffic.
CERT Tapioca has been used to identify Android applications that fail to properly validate SSL certificates and expose users to MitM attacks. More than one million apps have been checked and over 23,000 of them failed dynamic testing.
The tool can be used to analyze network traffic not only on smartphones, but also on IoT devices, computers and VMs.
Will Dormann, vulnerability analyst at CERT/CC and developer of CERT Tapioca, on Thursday announced the release of version 2.0, which introduces a graphical user interface and can be installed on multiple Linux distributions, including Red Hat, CentOS, Fedora, Ubuntu, OpenSUSE, and Raspbian.
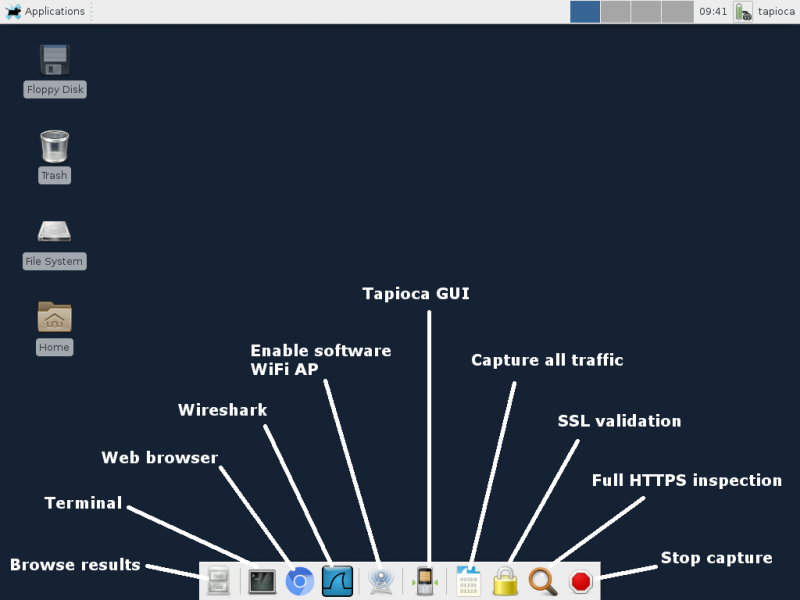
CERT Tapioca 2.0 also allows users to set up a HOSTAP-compatible Wi-Fi adapter for wireless connectivity, and it can save results from multiple tested systems.
In addition to checking HTTPS validation, verifying an application’s use of modern cryptography standards, and observing the hosts contacted by an application, Tapioca now allows users to search network traffic for specified strings, such as passwords.
The CERT Tapioca 2.0 source code, along with additional details and usage instructions, are available on GitHub.
Related: Kaspersky Releases Open Source Digital Forensics Tool
Related: Secureworks Releases Open Source IDS Tools
Related: UK’s GCHQ Spy Agency Launches Open Source Data Analysis Tool













