Researchers have described two new attack methods that can be used to “blind” cybersecurity products that rely on a logging mechanism named Event Tracing for Windows (ETW).
ETW, which is present by default in Windows since Windows XP, is designed for tracing and logging events associated with user-mode applications and kernel-mode drivers. The ETW in Windows 11 can collect more than 50,000 event types from roughly 1,000 providers, including operating system services, cybersecurity tools, common applications, DLLs, the OS kernel, and drivers.
ETW is leveraged by several endpoint detection and response (EDR) solutions to monitor security-related events and detect malware.
Threat actors, including profit-driven cybercriminals and state-sponsored cyberspies, have been known to disable ETW in their attacks in an effort to evade detection. Examples include China-linked APT41, the U.S.-linked Slingshot campaign, and the LockerGoga ransomware.
In addition to threat actors, ETW has also been increasingly targeted by security researchers, with well over a dozen vulnerabilities identified in 2021 alone, and tens of attack techniques presented over the past years.
New ETW attack methods were presented last week at the Black Hat Europe cybersecurity conference by researchers at Binarly, a company that specializes in solutions designed to protect devices against firmware threats.
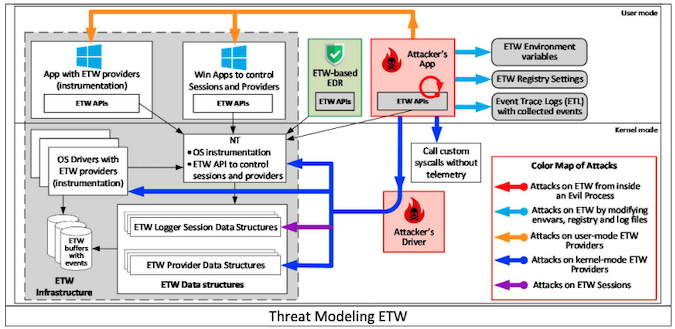
Binarly researchers have identified two new ETW bypass techniques, which they have demonstrated against Microsoft’s Process Monitor and Windows Defender.
In the case of Process Monitor, which is popular for malware analysis, the researchers showed how a malicious application with admin privileges on the targeted system can stop the running ETW session associated with Process Monitor and start a fake session. This results in the application no longer receiving network activity telemetry — basically being blinded by the attacker — and the problem does not get fixed even if Process Monitor is restarted.
In the case of Windows Defender, the researchers showed that it can also be blinded, by assigning zero to registry values that correspond to ETW sessions. This can be done by a malicious kernel driver, by modifying — in kernel memory — fields in kernel structures corresponding to Windows Defender ETW sessions.
Binarly on Thursday published a blog post describing its findings. The company has also developed open source tools that can be used to identify and prevent ETW attacks. These tools will become available in the upcoming period.
While Binarly’s blog post and Black Hat presentation focused on Process Monitor and Windows Defender, the company pointed out that these types of attacks can disable an entire class of security solutions.
Claudiu Teodorescu, CTO and founder of Binarly, told SecurityWeek that they have targeted Process Monitor and Windows Defender “because they are free, wide-spread and leverage the ETW ecosystem in the same way an EDR solution will do.” The company has performed tests on other commercial solutions as well, but they “don’t want to point fingers,” Teodorescu said.
“We want to raise awareness about the architectural problems and help the industry get fixed. That’s the main reason why we pick the neutral ones to demonstrate the attacks,” Teodorescu explained.
When asked if Microsoft has been informed about the findings, the researcher said the types of design and architectural problems highlighted by this research are typically not classified as vulnerabilities by the tech giant.
“MSFT frequently shows ignorance towards design issue submissions because they are not easy to fix and need significant effort from product teams. Basically, it isn’t easy to fix vulnerabilities related to architecture for a technology which has been developed and repurposed over the years,” Teodorescu said.
The researcher said there is no indication that these methods have been exploited in the wild yet, but pointed out that exploitation would be difficult to detect given that the goal of these attacks is to blind EDR products. However, he believes there’s a high chance malicious actors could leverage these methods due to the fact that “they offer another level of stealth-ness by blinding EDRs which are meant to detect anomalous behavior.”
“The methods we describe are very practical, raising awareness to the security community that ‘secure’ ETW sessions can be altered (queried/stopped) by modifying several fields in a kernel structure. For this reason, we chose to keep the source code for the tools we presented private to make sure attackers don’t have an easy path to a successful bypass,” Teodorescu said.
Related: Vendors Respond to Method for Disabling Their Antivirus Products via Safe Mode
Related: Microsoft Will Not Patch Security Bypass Flaw Abusing MSTSC
Related: Microsoft: Ongoing, Expanding Campaign Bypassing Phishing Protections














