Researchers at F5 Networks Security Operations Center (SOC) are warning of a new campaign of the Dridex web fraud malware. Previous campaigns had recently focused attacks on financial institutions in the United Kingdom, but among the new campaign’s malware configurations, only 6 percent of the targeted institutions are UK brands, versus 80 percent in the US and 5 percent in Canada.
Dyre is out, Dridex back in
The resurgence of the Dridex malware isn’t a surprise, as its main competitors for PC-based web fraud–SpyEye, Dyre, and Zeus–have all come under pressure from international law-enforcement agencies.
Two main operators of the SpyEye family have been shut down. Earlier this month, SecurityWeek reported that US authorities sentenced Russian national Aleksandr Andreevich Panin to nearly ten years in prison. Panin was attempting to travel through Atlanta, Georgia in the US when he was captured. The same court sentenced another fraudster, Algerian national Hamza Bendelladj, aka Bx1, to 15 years in prison and three years of supervised release.
The Dyre malware family has been in decline since February, when the Federal Security Service of the Russian Federation (the FSB) raided a Moscow film studio and arrested Dyre’s main operators.
Zeus is still among the most mature of the malware families. Its operator, Evgeniy Mikhailovich Bogachev, aka Slavik, is still at large. He’s one of the FBI’s most wanted; they’re offering a $3 million reward for information leading to his capture. The Zeus source code became open-source when it appeared on github (it is not clear if the leak was intentional). Since then, Zeus has been observed moving into the lucrative ransomware market.
With the Dyre and SpyEye arrests, and with Zeus moving to an adjacent market, Dridex and other malware will be working to grab their market share.
Dridex VNC backdoor
Dridex activates a Virtual Network Computing (VNC) backdoor, enabling its operators to remotely connect to their victim during the credentials theft and piggybacking the fraudster into the financial institution.
Dridex isn’t the only malware to utilize VNC; the Neverquest and Citadel malware families are also known to use the remote desktop software. The technique of remote-controlled desktops is ancient, tracing back even beyond the Cult of the Dead Cow’s Back Orifice tool in the previous millennium.
New form-grabbing targets
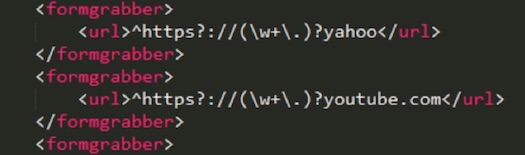
Dridex also steals social media credentials for non-financial accounts, both over HTTP communication and HTTP over SSL (HTTPS) encrypted communication. According to F5, Dridex targets Yahoo, Microsoft, Twitter, Facebook, and AOL login pages. These credentials may then be used to attempt authentication against other internet properties with high-value asset logins.
F5 SOC researchers remind people that the general defense against the theft of online credentials is proper security hygiene. Two-factor authentication can help to avoid re-usage of credentials for other websites. Using different passwords for different websites is also common sense today, along with up-to-date endpoint security software.
















