Blockchain, or distributed ledger, is sometimes described as a ‘solution in search of a problem’. There are many valid applications outside of pure cybersecurity — for example, reducing transaction costs in complex legal situations like house purchase, or tracking the location of physical goods in distribution or supply chains — but improving cybersecurity has had few valid and proven proposals.
Seema Haji, who leads product marketing for Splunk’s emerging markets group, is confident that blockchain has a future in IoT, but suggests it won’t happen overnight. “Blockchain’s ability to scale to accommodate the sheer volume of data produced by IoT devices in the next five to 10 years,” she says, “will be a major hurdle to overcome. Additionally, processing billions of data exchanges between devices on a daily basis will likely be a resource-intensive and expensive endeavor.”
One company that believes it has solved this scaling and resource problem is Xage (pronounced ‘zage’), which claims that its latest software will “increase the scale of protection for trillions of industrial devices and applications across many organizations and locations at once.” Key to this new version are two innovations: a hierarchical-tree and conditional consensus providing scaling potential; while nodes that can run on devices as small as a Raspberry Pi keep resource requirements low.
The Xage Security Fabric uses blockchain to control, enforce and distribute IoT and ICS policy to every individual device. Since you cannot bring the industrial devices to the data center for protection, you need to distribute that protection to the devices. “Blockchain,” Xage CEO Duncan Greatwood told SecurityWeek, “is an inherently distributed system. The way we use it is to allow security policy to be set centrally, but then use the tamper-proof blockchain fabric to replicate the policy out to nodes in the field and into all the different sites that need to use it.”
Any confidential data — such as a device password — is scattered within multiple nodes in the blockchain, so no single node can control everything, and — like the Bitcoin blockchain — multiple nodes would have to be hacked simultaneously for a hacker to gain anything. The blockchain controls the security policy, including who is allowed access to which devices, and an audit trail of what was done with each device. The access control imposed can include RBAC groups.
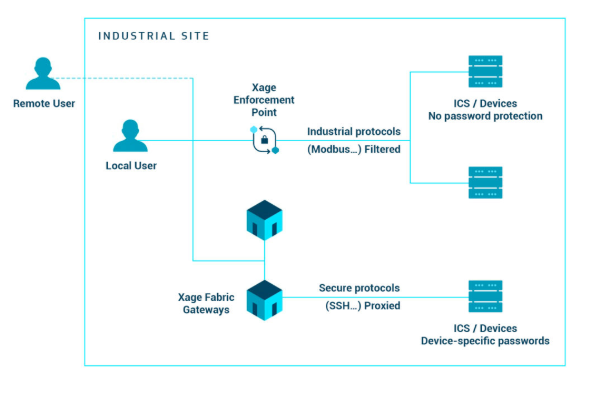
When the fabric is implemented, it changes the password for all devices that have one, and stores the new password within the fabric. “People who want to access a device,” explained Greatwood, “have to log into the Xage fabric in order to get proxy access into the devices — they can no longer log in directly.” Where devices do not or cannot have passwords, they are protected by physically close Xage Enforcement Point (XEP) nodes.
“These sit in line with a poorly protected machine on the network,” said Greatwood, “and will filter the information going into and out of the device and guarantee its validity. Crucially, it asks the fabric, ‘is this particular user properly authenticated and authorized to carry out the access they are attempting?’ For instance, if you are a technician working for a west coast utility, you might be a member of the Mountain View Technician Group; and if you are a member of that group then when you try to access a substation controller in Mountain View, you’ll have to log into the Xage fabric and the XEP will check the details and provide access where proven.”
Because fabric nodes can be implemented in low computational devices, if they cannot be implemented within existing computers, they can be sited in very close proximity to the devices they protect. The protection is effectively placed over the top of the device, and provides RBAC, encryption, and other capabilities of the system.
The combination of the XEP and the proxy access with passwords is the primary enforcement mechanism the fabric uses to control access into and out of the devices. Both styles of protection leverage the fact that you have multiple nodes in the fabric and no single point to hack in order to compromise the system. It effectively includes a distributed password management system designed for the specific access problems of IoT and industrial devices.
The hierarchical distributed nature of the fabric is fundamental to the ability for it to scale. It is deployed both in the cloud and on premise throughout an industrial operation. “It is deployed everywhere in the industrial operation,” said Greatwood. “For example, in a utility it is in the substations, in the controllers, and in the central management data centers. In an oil and gas company, it is in the well pads, in the local control centers, and it is in the cloud where the cloud is used. The fabric plays a big role in maintaining integrity between the edge and the center. So, one of the key new innovations announced now is the delivery of a hierarchical blockchain fabric. What that means for example in the oil and gas scenario, is that each well pad has its own subsystem blockchain deployed with typically just a few nodes for each well pad; but then at the higher level of the hierarchy there is a global blockchain that spans all of the well pads.”
The hierarchy means that each local environment has its own small blockchain. If the local blockchain gets separated from the global blockchain, there is enough information stored on the local blockchain to provide all the necessary security services, so it is still doing access control and providing authentication locally. An oil and gas well pad might just have one such sub-system; while a factory could have hundreds. The result is huge scope for horizontal scaling.
“When the local blockchain reconnects to the global blockchain,” continued Greatwood, “it resynchronizes between the local and global fabric. That brings everything up to date in a tamper proof fashion and allows for reverification of any changes made locally. So even if someone does hack the local blockchain, (say, there were five fabric nodes and all five got compromised simultaneously) the global system would overwrite any changes when it gets reconnected.”
A further innovation in the new Security Fabric blockchain version is the introduction of what Xage calls ‘supermajority consensus’. Consensus is used to assess the validity of a transaction — if the majority of nodes accept it, it is valid. But in today’s multi-company supply chain environments where multiple companies share information, this could lead to one company with thousands of nodes having the ability to out vote a company with fewer nodes.
“What we found as we started to deploy the Security Fabric across supply chain applications is that a simple consensus is not enough,” explained Greatwood. “People are sharing data via the fabric and they want to know not only that the majority of nodes have to agree, but also that no one company or no couple of companies can just exercise a majority vote and say, I want access to that data, or change that thing. The new capability is that we’ve created a mechanism for protecting minority rights in these situations — so, in one example in an oil refinery we have four suppliers plus the oil refinery itself. In order to make a change in the ledger, there must be a majority agreement not only across the whole fabric, but also within each of the individual companies involved. In other words, the refinery cannot outvote the supplier and the supplier cannot outvote the refinery — they both have to agree in their internal majority before the global majority can take place.”
Robust cybersecurity, he added “is the necessary foundation for Industrial IoT operations, which are growing to include trillions of devices and interactions across multiple organizations and varying sites. The Xage Fabric’s hierarchical blockchain and supermajority consensus ensure secure multi-party collaboration and governance, and improved operations and efficiency across rich industrial ecosystems.”
In the video below, Susanto Irwan, Co-founder and VP of Engineering at Xage Security, discusses Protecting ICS with Decentralization and Blockchain at SecurityWeek’s ICS Cyber Security Conference in 2018.
Related: Blockchain Security Firm Fireblocks Emerges From Stealth With $16M in
Related: Transmute Launches Blockchain Framework Focused on Identity
Related: Blockchain Security Startup CipherTrace Emerges With $15M in Funding
Related: How Cybercriminals Are Using Blockchain to Their Advantage











