Researchers have uncovered a targeted attack against political rights activists in China in which a malicious Word document exploits a vulnerability in Microsoft Office to take control of the victim computer.
The attack email advertises a suffrage movement seminar event, and appears to target members of social groups involved in various political rights movements in China, Amanda Stewart, a malware research engineer at FireEye Labs, wrote on the FireEye blog Tuesday. The email contains a link to a Google form which appears to be some kind of a registration form and came with a malicious Excel attachment. The file, which appears to have the same contents as the email, triggered remote code execution vulnerability in Microsoft Office’s MSCOMCTL component (CVE 2012 0158), Stewart said.
Exploits for this vulnerability were observed last year in Tibetan-themed targeted attacks and in information-theft campaigns against Russian victims, among others. Microsoft patched the vulnerability in April 2012.
In the current campaign, when the Excel file is opened, the malicious code downloads a decoy document and other payloads. The decoy pretends to be a detailed agenda and description of the alleged seminar. While the user is viewing the decoy file, the payload extracts the Microsoft file OINFOP11.exe, OInfo11.ocx DLL, and compressed shellcode sections from Oinfo11.iso, all elements of a standard Windows operating. The executable loads the DLL file and runs the ISO file in memory.
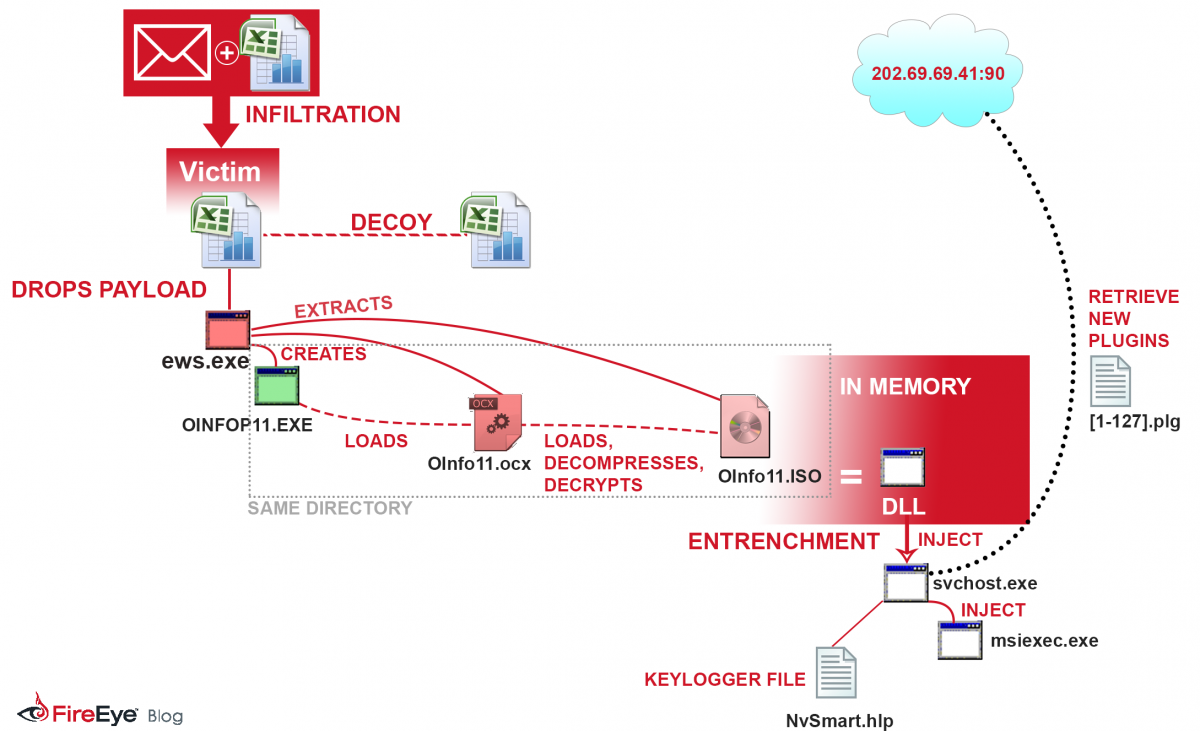
“The malicious execution is never dropped to the file system and is therefore not seen by filesystem-based antivirus detectors,” Stewart wrote.
FireEye researchers identified the remote access tool being used as PlugX, which has used similar sideloading techniques in the past with executables from McAfee, Intel, Lenovo, and NVIDIA, among others. PlugX uses legitimate applications to load malicious DLL components in order to evade detection.
Most of the variants which have been identified so far appear to have been based in Asia, particularly China, Japan, and Taiwan. PlugX was also used in the Winnti gaming malware discovered by Kaspersky Labs researchers last month.
The DLL is essentially a loader which decompresses and decrypts the malicious payload in memory, Stewart said. Malware authors use sideloading techniques to evade endpoint security products, Stewart said. As of Tuesday afternoon, only one out of 46 vendors listed on VirusTotal had flagged the file as malicious.
Once the malicious code executes, the malware creates a keylogging file which collects input information and transfers the information to a command and control server based in Hong Kong. The malware is capble of accessing disk drives to modify files, list network shares and TCP/UDP connections, map ports, stop or start processes, modify registry keys and services, send system commends to the workstation or communicated with the C&C server, make SQL database queries, and startup a telnet server on the compromised computer.














