A mitigation proposed by Microsoft and others for the new Exchange Server zero-day vulnerabilities named ProxyNotShell can be easily bypassed, researchers warn.
The security holes, officially tracked as CVE-2022-41040 and CVE-2022-41082, can allow an attacker to remotely execute arbitrary code with elevated privileges.
Researcher Kevin Beaumont named the vulnerabilities ProxyNotShell due to similarities to the Exchange vulnerability dubbed ProxyShell, which has been exploited in the wild for more than a year. It seems that Microsoft’s patches for ProxyShell do not completely remove an attack vector.
However, unlike ProxyShell, the new issues can only be exploited by an authenticated attacker, although even standard email user credentials are sufficient.
The high-severity flaws were discovered and reported to Microsoft by Vietnamese cybersecurity company GTSC, whose researchers saw them being exploited in August by a threat actor believed to be linked to China.
Microsoft’s own analysis indicates that a single state-sponsored threat group has chained the Exchange vulnerabilities in attacks aimed at fewer than 10 organizations, but the tech giant expects other malicious actors to start leveraging them in their attacks.
Patches for these vulnerabilities have yet to be released, but Microsoft says it’s working on fixes on an accelerated timeline.
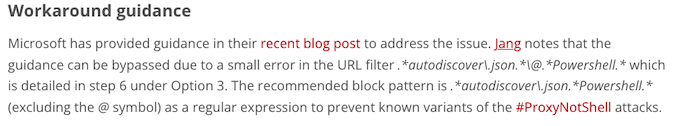
In the meantime, GTSC and Microsoft have proposed a mitigation that involves setting a URL rewrite rule that should block attack attempts. However, a researcher known as Jang noted that the rule is not efficient and can be easily bypassed. Jang did propose a very similar rule that should work.
The CERT Coordination Center at Carnegie Mellon University has released its own advisory for CVE-2022-41040 and CVE-2022-41082, and provided an explanation regarding the problematic mitigation.
Microsoft has released a tool that should automate the mitigation, but at this point it likely applies the rule that can be bypassed.
While details have not been made public for the vulnerabilities in order to prevent abuse, some individuals have been offering ProxyNotShell proof-of-concept (PoC) exploits that have turned out to be fake.
However, some members of the security industry do have working exploits, Beaumont said.
Since exploitation of the vulnerabilities requires authentication, mass exploitation is unlikely at this point, but the flaws can be very valuable in targeted attacks. Some members of the cybersecurity community have released open source tools that can be used to detect the presence of the vulnerabilities.
Microsoft has told Exchange Online customers that they don’t need to take any action, but Beaumont believes that is not true.
Related: Microsoft Links Exploitation of Exchange Zero-Days to State-Sponsored Hacker Group
Related: Microsoft Exchange Attacks: Zero-Day or New ProxyShell Exploit?













