In a series of posts on Twitter, Microsoft on Tuesday warned of an uptick in gift card-themed business email compromise (BEC) attacks targeting K-12 school teachers by impersonating their colleagues.
“We detected a recent spike in business email compromise (BEC) attacks soliciting gift cards primarily targeting K-12 school teachers. Attackers impersonate colleagues or school officials to ask recipients to purchase various gift cards,” Microsoft Security Intelligence warned.
The attackers create fake email accounts impersonating K-12 school personnel. The accounts are created based on publicly available information, which is harvested from various websites or social media platforms. They then use these accounts to send scam emails to their targets.
The attackers abuse free email services, including Gmail, Outlook, Mail.ru, Hotmail, iCloud, and Yahoo. Microsoft said the scammers have not used email spoofing, only newly registered accounts.
Typical to BEC scams and phishing attacks, the threat actors employ various lures and scenarios to fabricate a sense of legitimacy and to suggest urgency.
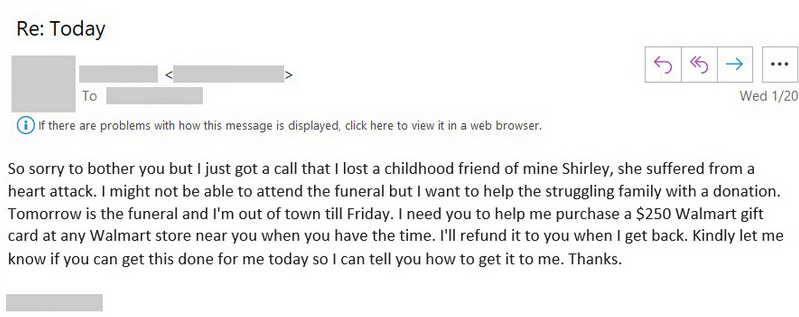
In some of the examples the tech company has shared on Twitter, the attackers asked victims to purchase physical gift cards and send them photos of those cards, promising quick reimbursement.
According to Microsoft, the same threat actors previously used COVID-19 lures in similar gift card BEC campaigns.
In replies to Microsoft’s tweets, security researchers said such BEC attacks have been ongoing for over a year, and that universities too are being targeted, alongside K-12 environments.
Contacted by SecurityWeek on the matter, Microsoft could not share information about the number of observed attack attempts. The company hasn’t tied these incidents to previous BEC campaigns.
To stay protected from this type of BEC attacks and other malicious activity, organizations are advised to use security solutions capable of identifying domain spoofing and impersonation attempts, and to instruct staff to always be vigilant about the content of the messages they receive.
Related: BEC Scammers Exploit Flaw to Spoof Domains of Rackspace Customers
Related: Cybercriminals Stole $15 Million From 150 Companies in BEC Attacks
Related: FBI Warns of Auto-Forwarding Email Rules Abused for BEC Scams















