While October is National Cyber Security Awareness Month (NCSAM) in the U.S., security awareness is a quaint idea when the news is regularly full of security breaches.
NCSAM is an annual campaign, sponsored by the Department of Homeland Security and the National Cyber Security Alliance since 2004, to “raise awareness about the importance of cybersecurity, provide them with tools and resources needed to stay safe online, and increase the resiliency of the Nation in the event of a cyber incident.”
Their primary approach for raising awareness is a social media campaign designed to share the “Stop.Think.Connect. Toolkit,” which is a useful collection of security best practices that can be tailored to different users such as students, government, small business or young professionals. Last year’s campaign results are noted in the following infographic (Image Credit: DHS):
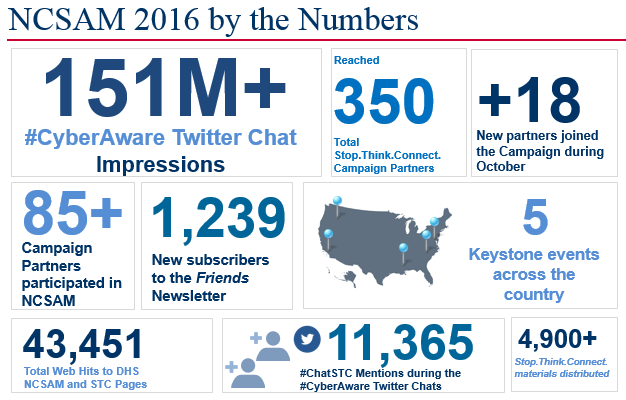
It’s an impressive set of numbers and it’s a worthwhile effort if you agree that people are the weakest link in security.
Yet, when the mainstream media is covering breaches, and the breach reach has expanded to ensnare all types of industry and almost every adult in the US, awareness of cyber security threats doesn’t really seem to be the issue. Raising awareness of the implications and steps to prevent breaches is helpful, but only to the point that people actually take action to reduce the risk for themselves, their families and their organizations.
Growing numb to attacks
There is risk involved with too much awareness. Like the proverbial boy who cried wolf, every warning that brings no consequence serves to numb the average person to the risks of cyber attacks. Following the Equifax breach, only about a quarter of the U.S. adult population checked their credit score or credit report in the first two weeks. Less than 1% of consumers have put a credit freeze in place. For all the visibility this attack has brought, it’s produced a collective yawn from consumers.
That consumer callousness can translate into employee ennui. Employees are consumers in a different context, prone to ignore security best practices as well. Expediency is rarely sacrificed for security. For all the encouragement to not reuse passwords and make them impossible to guess, the top 25 most common passwords don’t change all that much. Many don’t think twice about connecting to free public Wi-Fi and transmit sensitive data while traveling. And weaponized email containing malware or phishing scams continue to work well for hackers.
How do we improve awareness?
If awareness isn’t working to change the behavior of employees and consumers, is there anything that can be done? Perhaps it isn’t the general public that really needs the attention. While every person has a role to play in security, if we really want to help improve security postures, we need to focus awareness at the top of organizations.
Boards need to have the expertise to understand cyber security practices and demand accountability to standards from executives. That should include anticipating and mitigating the likely human failures, including these scenarios:
• Servers and applications will accidentally remain unpatched. But a vulnerable server isn’t worth much to a hacker if the sensitive data stored on it is encrypted.
• People will forget to change the default admin password. But if two factor authentication is in place, then the password alone won’t be sufficient to access a server.
• No matter how much training is provided on spotting a malicious email, users will click a link to something that interests them. But user behavior analytics can identify if a user’s account starts behaving strangely due to compromised credentials.
• Privileged users are generally loyal employees, though it only takes one disgruntled one to become your Edward Snowden. Restrict the amount of access privileged users have, and monitor and record their activities with privileged account management to deter malicious activity.
• Developers don’t intend to use a code library with a known vulnerability. But at the speed of DevOps, security testing must shift left into the continuous delivery pipeline to avoid being forgotten.
Human nature being what it is, even 100 percent awareness of cyber security challenges isn’t going to significantly improve the security postures of our organizations. We have to consider the downside of over-awareness in generating disinterest as well. Maybe it’s time to strive for less awareness on the part of general users and focus more security awareness on the decision makers who can make a bigger difference in improving the security posture of our organizations.












