Threat researchers from Cisco have shared details on a new and rapidly spreading attack targeting web servers running on systems powered by outdated versions of Linux.
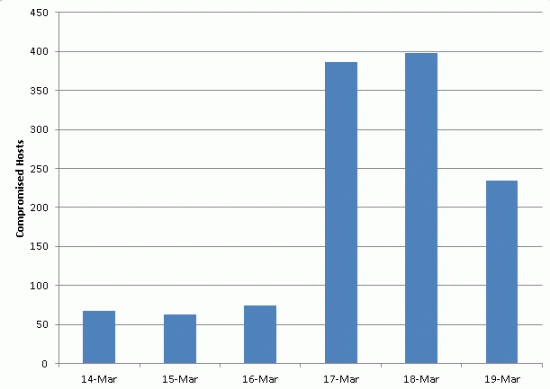
According to Cisco, upward of 400 different hosts were affected each day on March 17 and 18, with attackers successfully compromising more than 2,700 URLs at the time of publishing.
The attackers are compromising legitimate websites, Cisco said, with most of the affected web servers running on the Linux 2.6 kernel—an outdated version that was first released in 2003. The location of compromised servers have been found throughout the world, but have a particularly high concentration in Germany and the United States.
“It is possible that attackers have identified a vulnerability on the platform and been able to take advantage of the fact that these are older systems that may not be continuously patched by administrators,” Cisco’s Martin Lee wrote in a blog post late Thursday.
In order to execute the attack, cybercriminals compromise an existing website, insert a line of JavaScript to multiple .js files hosted on the site, causing visitors to load and execute a new JavaScript file served from compromised third-party host.
“We observed the second stage sites serving what appears to be pay per view fraud pages, where the visitor’s browser loads multiple advertisements to generate revenue for the attacker,” Lee said. “However, there is anecdotal evidence that visitors have been infected with Trojan malware as part of this final step.”
Many of the affected hosts have been identified as compromised and cleaned, Cisco said.
Lee explained that some security products may detect the JavaScript redirect as being similar to that previously used in the Blackhole exploit kit, but Cisco has no evidence suggesting that the attacks are related to Blackhole rather than an example of code reuse.
“This large scale compromise of an aging operating system, highlights the risks posed by leaving such systems in operation,” Lee said.
“Systems that are unmaintained or unsupported are no longer patched with security updates,” he continued. “When attackers discover a vulnerability in the system, they can exploit it at their whim without fear of it being remedied. In April 2014, Windows XP will become unsupported. Organizations urgently need to review their use of unsupported systems in operation. Such systems need to be upgraded where possible, or regularly monitored to detect compromise.
Just yesterday, researchers from Imperva issued a threat advisory about an old PHP vulnerability that was patched in 2012 but actively being exploited in attacks. While this particular PHP flaw was discovered in March 2012 and patched in May, a public exploit began making the rounds in October 2013, Imperva said in its advisory. Imperva’s honeypots detected more than 30,000 campaigns using some form of the exploit within three weeks of its publication. The fact that the exploit became publicly available more than a year later suggests criminals were still enjoying some degree of success targeting this vulnerability, Barry Shteiman, director of security strategy at Imperva, told SecurityWeek.
“Large numbers of vulnerable unpatched systems on the Internet are tempting targets for attackers,” Cisco’s Lee said. “Such systems can be used as disposable one-shot platforms for launching attacks. This makes it all the more important that aging systems are properly maintained and protected.”
Cisco has provided a list of compromised URLs here and here, which can be used for blacklisting and URL filtering in order to prevent users from visiting those pages.
Earlier this week, ESET warned of a widespread attack campaign that has infected more than 25,000 Linux and UNIX servers around the world. According to ESET, the servers are being hijacked by a backdoor Trojan as part of a campaign the researchers are calling ‘Operation Windigo.’ Once infected, victimized systems are leveraged to steal credentials, redirected web traffic to malicious sites and send as much as 35 million spam messages a day.













