In a year dominated by kinetic/cyber war in Ukraine, North Korea doubles down on cryptocurrency thefts, China and Iran continue to take advantage, and a new form of personal intimidation of company personnel emerges.
Mandiant published its M-Trends 2023 report on Tuesday, the latest edition of its annual report based on Mandiant Consulting Investigations of targeted attack activity between January 1, 2022 and December 31, 2022.
Global cyberattack trends
Globally, Google-owned Mandiant found a general increase in the number of incidents first reported to victims by an external source (that is, not by internal detection). However, this increase is not consistent across the three regions of the Americas, APAC, and EMEA. External detection is highest in EMEA (74%) and lowest in the Americas (55%).
This implies that companies’ own detection capabilities are improving, although noticeably, internal detections are falling in APAC. However, the figures are likely to be influenced by other factors such as geopolitics and changing attacker practices and priorities in different regions.
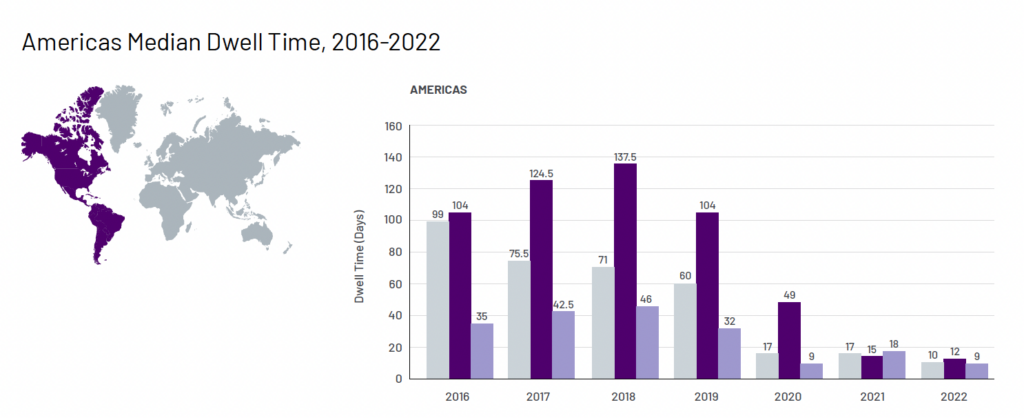
Similar regional (and attack type) differences are found in dwell times. Overall, there has been a decline in the median dwell time from 21 days to 16 days. By region, this comprises 17 days down to 10 days in the Americas, an increase from 21 days to 33 days in APAC, and a decline from 48 days to 20 days in EMEA.
The ransomware specific dwell times are also different. The overall number of ransomware investigations declined from 23% to 18% while the overall dwell time increased from five days to nine days. Interpreting ransomware statistics is always difficult because of changing tactics (such as scatter-gun to targeted to whaling), and the largely unknown extent of non-reporting by victims.
The dwell time for ransomware in the Americas has remained static at five days; has increased from nine days to 18 days in APAC; and has increased from four days to 33 days in EMEA.
For all attacks, where it could be detected, exploits (32%), followed by phishing (22%), followed by stolen credentials were the most common initial infection vector. Again, this varied by region. In the Americas, exploits were the most common vector at 38%. in APAC it was prior compromise at 33%. And in EMEA it a phishing at 40%.
In short, the attackers are not using the same attack paths across the globe. “Adversaries continue to leverage the intrusion vector that is the most effective to gain access to their targets that reside in each region,” says Mandiant.
Financially motivated attacks declined from 30% to 26%; 18% of which were ransomware attacks. Data theft as a priority increased from 29% to 40%, within which 8% was ransomware. Twenty-two percent of attacks were thought to prioritize intellectual property or espionage purposes.
Mandiant tracked more than 900 new threat groups during 2022. A total of 343 unique threat groups were identified, and 265 were first identified in 2022. The threat groups included four named APTs from China and Russia, five named FIN groups, and 335 uncategorized (UNC) groups. (Mandiant graduated UNC1130 to APT43 in March 2023.)
Five hundred and eighty-eight new malware families were tracked, indicating little change over previous reporting periods. The top five malware categories are backdoors, credential stealers, downloaders, droppers, and launchers (71% of all the new families).
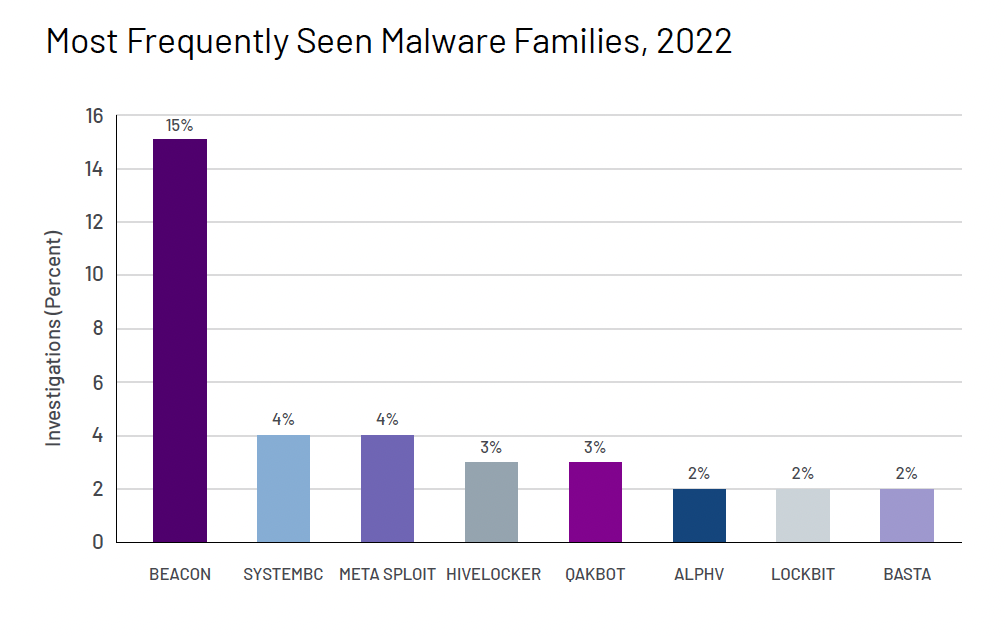
The five most seen malware families were Beacon (15%), SystemBC 4%, Metasploit (4%), HiveLocker (3%) and Qakbot (3%). This varied by region, with Beacon most prevalent in APAC, and least prevalent in EMEA. TankTrap was the third most prevalent in EMEA (5%), probably due to the Ukraine conflict. In APAC, the Sodinokibi ransomware was second at 8%, with the DragonJuice reconnaissance tool third at 7%.
Windows remains the most attacked operating system, but there is a growing tendency for attackers to adopt malware that can run on multiple OSs. VMkernel is included within the operating systems for the first time.
“While the general volume of malware effective on this operating system is not significant,” says Mandiant, “this is notable for defenders due to the prevalence of VMWare architecture, specifically ESXi hosts. These types of operating systems do not have significant capability for Endpoint Detection and Response (EDR) tool monitoring. As a result, monitoring and investigations into the platform can be challenging for defenders.”
Ukraine
The report takes a close look at the Russia/Ukraine war. This is the first time that a major cyber power has simultaneously been involved in a large-scale kinetic war. Lessons learned may be important for the future.
Mandiant delineates five separate phases in the cyberwar aspect of the conflict. The first, it suggests, started in 2019 and continued until January 2022. It describes this phase as ‘strategic cyber espionage and pre-positioning’ and highlights the Shadylook and Paywipe malware.
The second phase, from February 2022 until April 2022 is described as the ‘initial destructive cyber operations and military invasion’. Skyfall, Partyticket, Nearmiss, SDelete, CaddyWiper, Junkmail, Industroyer2, SoloShred, and AwfulShred are highlighted.
The third phase ran from May 2022 to July 2022, and is described as ‘sustained targeting and attacks. This is almost entirely CaddyWiper targeting government institutions.
The fourth phase, from August 2022 to September 2022 is described as ‘renewed espionage targeting’. No further details are given.
The fifth phase, October 2022 to December 2022 (the end of the reporting period, but not the end of the war) is a ‘renewed campaign of disruptive attacks – involving CaddyWiper, Dharma, Partyticket, Presstea, and Ransomboggs.
Notably, the report mentions a deviation in practice from APT28 (aka Sandworm, Fancy Bear, Sofacy) following the outbreak of the war. It has developed a preference for ‘living off the edge’ (this preference is also growing elsewhere in the cybercrime ecosphere). This is a persistence technique involving the compromise of routers and other internet connected devices.
“Where destructive actions necessitate the loss of direct access to endpoints, compromised edge devices allow for continued re-entry to the network. Compromise of these routers can also be harder for defenders to detect as most EDR technologies do not cover these types of devices.”
For general cybercriminals, this tactic can allow re-entry either at some future date or following disruptive activity from the cyber defenders.
Apart from the five phases of the cyberwar, Mandiant also notes a strong Russian disinformation campaign, which it expects to increase. This is targeted not only at Ukrainians and NATO countries, but also at the Russian populace. The intent in all cases is to demoralize Ukraine, weaken support for Ukraine, and make the Russian people more pro-war.
“Russia’s invasion of Ukraine has demonstrated the potential overlap of cyber operations and kinetic warfare as a new de facto standard,” concludes the section. “The war has consumed almost every aspect of Russia’s international relationships and has evolved as nearly the sole driver of cyber threat activity from Russia in 2022.”
North Korea and financial operations
While the report mentions that both China and Iran are continuing the cyber pursuit of their own national interests, it takes a close look at North Korean activities. “Alongside their traditional intelligence collection missions, in 2022 DPRK operators showed more interest in stealing—and using—crypto, with their activity expanding to new parts of the digital asset ecosystem as the regime looks to mitigate the economic impact of sanctions,” says Mandiant.
While DPRK groups remain interested in targeting large financial institutions, Mandiant has observed increasing interest in targeting cryptocurrency. The firm notes that DPRK groups have reportedly stolen $1.7 billion during 2022, and are thought to have $170 million in unlaundered currency (presumably held for their own reserves). The UN believes the stolen crypto is used to finance the country’s missile programs. The number of DPRK groups involved in attacks has expanded over the year – and NFTs and bridges are now included in the targets.
Bridges allow the movement of assets between different blockchains without the need for cryptocurrency exchanges. They grow in value as they are more widely used, and consequently become an attractive target. An example was the $100 million compromise of Harmony’s Horizon Bridge during 2022. The FBI attributed this attack to North Korea.
North Korean ransomware and espionage activities have not disappeared. Mandiant’s research suggests that continuing ransomware attacks may have more to do with self-funding for future activities than with furthering the nation’s financial response to sanctions.
At the same time, says the report, “Mandiant has continued to witness DPRK campaigns and operations of a traditional espionage nature.”
Changes in criminal activity
There is one further emerging development, which can hardly yet be called a trend, but may become one. Much has been written about the increasing ‘professionalism’ of cyber gangs – typified, perhaps by ransomware gangs’ acknowledgement of the importance of good customer (for which read victim) support.
This approach was abandoned by two new groups: UNC3661 (known publicly as Lapsus) and UNC3944. Lapsus first targeted companies in South America, but soon expanded to global corporations. The motive didn’t seem to be primarily financial and was more like seeking notoriety (perhaps closer to the ‘50 days of lulz’ from LulzSec a dozen years ago). The group often demanded that corporations should release intellectual property as open source and would conduct Telegram polls to determine their next victim.

More recently, a separate group, UNC3944, emerged with some similar characteristics but a financial motivation. Both groups leveraged the data found in underground cybercrime markets, used clever social engineering schemes and even bribes to carry out intrusions and account takeovers. Neither group relied on zero days, custom malware, or new tools. “Furthermore,” says the report, “these adversaries demonstrated a willingness to get personal with their targets, bullying and threatening many of them.”
In a separate blog announcing the M-Trends report, Jurgen Kutscher, VP, Mandiant Consulting at Google Cloud, comments, “Another common trend… featured in M-Trends 2023 is increasing attacker aggression and boldness. Attackers are showing willingness to eschew the traditional cyber rules of engagement, to bully and threaten and get very personal with targets, and to show up to places in person to enable initial access. Organizations across the globe need to be thinking about how to protect their employees from these much more personal threats.”
Summary
The annual Mandiant M-Trends report is a major factual analysis of emerging threat trends, beginning to rival the Verizon DBIR in importance. This year’s report covers more than we have discussed here; including, for example, a red team case study, and pages of MITRE ATT&CK mappings.
We haven’t included those because they are not strictly ‘trends’ (as in M-Trends). Our hope is that Mandiant can constrain the content of this report and not allow it to grow into something verging on being bloated – as could now be said of the DBIR. If it concentrates on its title, M-Trends is likely to become even more beneficial and important than it has already become.
Many topics addressed in the M-Trends report will be discussed at Mandiant’s mWISE (Mandiant Worldwide Information Security Exchange) conference, held in Washington, D.C. from September 18–20, and also available virtually.
Related: Mandiant Investigating 3CX Hack as Evidence Shows Attackers Had Access for Months
Related: Exploitation of 55 Zero-Day Vulnerabilities Came to Light in 2022: Mandiant
Related: Google Completes $5.4 Billion Acquisition of Mandiant


















