Researchers at Trusteer have discovered a type of attack that is targeting Android users via their desktops, with the aim of controlling both endpoint devices. So far the malware itself is limited to Spain, Germany, the Netherlands, and Portugal.
Trusteer’s discovery offers some additional insight into the development of SpyEye and Tatanga, the families of malware making headlines recently. In May, Trusteer observed Tatanga mixing traditional social engineering with browser hijacking in an attempt to fool the victim into legitimately approving wire transfers.
This time, Tatanga is combined with elements form SpyEye and used in a clever scheme to entice users to install an alleged security application. Based on what Trusteer has published, it appears that this latest set of attacks are an upgrade and not a new infection point. Once an infected system visits a specialized or pre-determined domain (often banking related), Tatanga will use web injects to entice the user to install the security application.
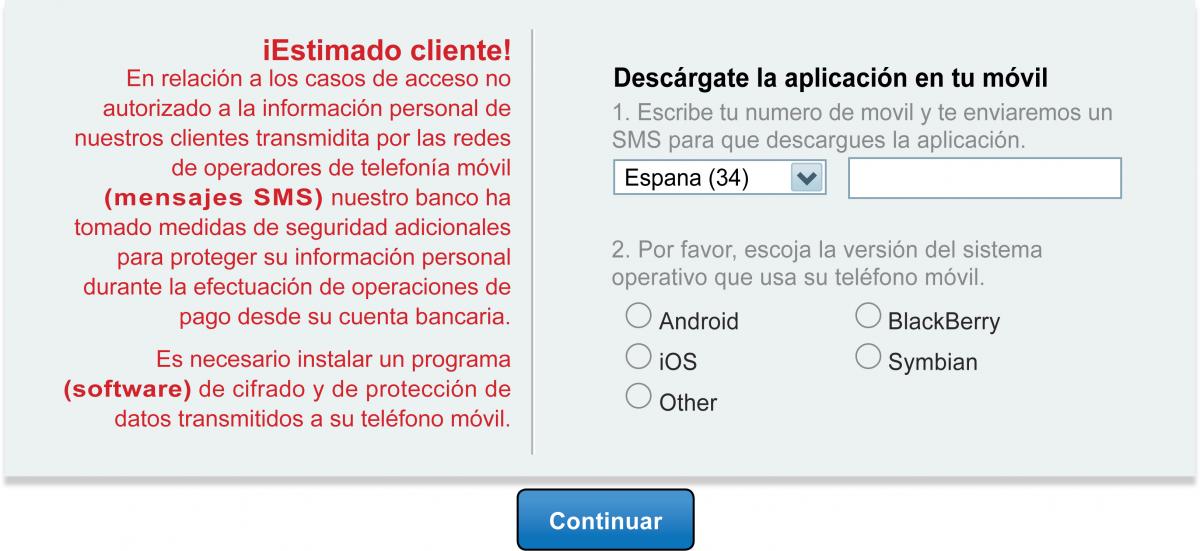
“In most attacks, if the victim is using an operating system other than Android the malware informs the user that no further action is required. However, for all Android users, the desktop component [of the attack] requests the victim’s phone number and notifies them that a link for downloading the security application has been sent (via SMS) to their mobile device. The user is directed to install the fake application from this link and enter the activation code provided by the malware,” Trusteer explains.
If the attack is successful, the malware captures all SMS traffic, including any security codes that may be sent to the device.
The full blog post is here, which explains how the attacks work to some degree in each of the targeted areas. They’re all the same for the most part, but each one hammers home an important point; don’t download financial applications from unknown sources.
If the bank’s Web site is encouraging the use of a mobile security application – seemingly out of the blue – question them about it. It takes no time at all to initiate a phone call to the local branch.












