Microsoft-owned social media giant LinkedIn has once again put user data and privacy at risk by allowing a TLS certificate to expire.
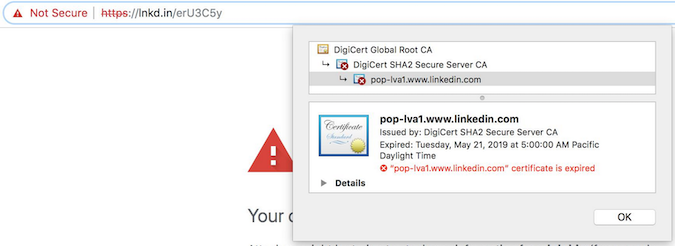
Some users noticed on Tuesday that when they tried to access LinkedIn from their desktop or laptop computer they were greeted by an alert that said the connection was not secure. It turned out that the company had forgotten to renew the TLS certificate for its lnkd.in URL shortener.
The company quickly took action after being notified. The new certificate is valid until May 2021.
This is the second time this has happened. In November 2017, LinkedIn forgot to renew a certificate for country-specific domains, such as uk.linkedin.com and de.linkedin.com.
“Large organisations with hundreds of millions of users globally should be setting the standard for security practices and unfortunately this is the second time that LinkedIn failed to update their SSL certificate, effectively putting user data and privacy at risk,” Carl Leonard, principal security analyst at Forcepoint and one of the individuals who reported the incident to LinkedIn, told SecurityWeek.
“Although this expired certificate only appeared to affect desktop users of LinkedIn, users had to rely on their browsers to alert them to the risks associated with the site. In some cases this may have led to confusion or encourage users to override error messages without understanding the security implications,” Leonard said.
“It isn’t enough for organisations to be reactive,” the expert added. “They should proactively ensure that are consistently implementing cybersecurity practices which act to protect sensitive information from being intercepted or exposed, whilst preserving the user experience. Humans will always make mistakes and have lapses in judgement and it is the role of the appropriate technology to address these issues to ultimately keep data safe.”
UPDATE. LinkedIn told SecurityWeek that it had a brief delay in its SSL certification update. The company said the issue was quickly fixed and user data was not affected.
Related: TLS Certificates for Many .gov Domains Not Renewed Due to Government Shutdown
Related: LinkedIn Responds to Criticism of its SSL Implementation














