Following a takedown operation earlier this month, authorities are taking steps towards cleaning up systems infected with the Emotet malware.
One of the most prevalent botnets over the past decade, Emotet has been around since 2014, helping cybercriminals deploy their own Trojans, ransomware, and other types of malware onto compromised machines.
Serving as a malware loader, Emotet has been associated with the distribution of well-known malware families, including TrickBot and Ryuk ransomware, among others.
This week, Europol announced that, as part of an international operation that saw the participation of law enforcement agencies from eight different countries, Emotet’s infrastructure has been dismantled.
Authorities were able to take over the infrastructure, which included hundreds of servers worldwide, used to manage bots, spread Emotet, serve customers, and improve the network’s resilience.
The Ukrainian police announced that two suspected Emotet infrastructure operators have been arrested, while other cybercriminals associated with the botnet’s activities have been identified and are being pursued. Emotet’s operators face up to 12 years in prison.
Codenamed LadyBird, the takedown operation also resulted in the seizure of hardware, credit cards, and cash, along with login credentials, keys to encrypted services, and information related to the infected companies. Authorities also identified 600,000 compromised email addresses, with passwords.
“The police have used their hacking powers to penetrate and investigate Emotet’s cyber-criminal infrastructure. It was necessary to take action simultaneously in all countries concerned in order to be able to effectively dismantle the network and thwart any reconstruction of it,” the Dutch police said.
Authorities in the Netherlands also reveal that the investigation into Emotet, which started in 2019, has helped identify the various servers used for infrastructure, as well as over 1 million infected machines.
With law enforcement having taken control of the infrastructure, an update is being served to all infected machines, from the Dutch central servers.
“All infected computer systems will automatically retrieve the update there, after which the Emotet infection will be quarantined,” the Dutch police said.
No specific timeframe for when the cleanup process will begin has been provided, but a security researcher suggested on Twitter that March 25, 2021, might be the day, based on lines of code found in the update that’s being sent to Emotet bots.
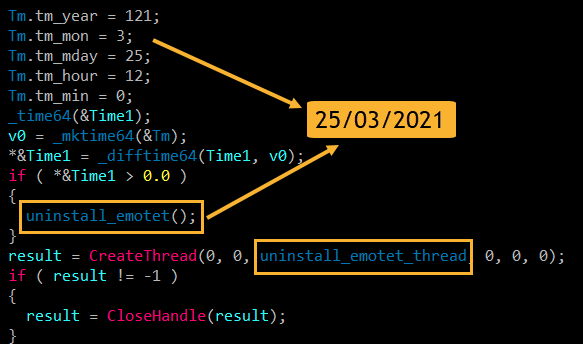
The researcher also discovered that all of the command and control (C&C) server IP addresses that Emotet now uses are located in Germany.
SecurityWeek has contacted the Bundeskriminalamt (BKA), Germany’s central criminal investigation agency, for confirmation on the actions taken to clean up the Emotet infections, but hasn’t received a reply yet.
Emotet’s operations, which helped many cybercriminals conduct illicit activities, are estimated to have caused hundreds of millions of dollars in losses. According to Ukrainian authorities, such losses may be in excess of $2.5 billion.
UPDATE: BKA has provided SecurityWeek the following statement:
Within the framework of the criminal procedural measures carried out at international level, the Bundeskriminalamt has arranged for the malware Emotet to be quarantined in the computer systems affected. An identification of the systems affected is necessary in order to seize evidence and to enable the users concerned to carry out a complete system clean-up to prevent further offences. For this purpose, the communication parameters of the software have been adjusted in a way that the victim systems no longer communicate with the infrastructure of the offenders but with an infrastructure created for the seizure of evidence.
UPDATE 2: Cybersecurity firm Team Cymru told SecurityWeek that while it was not involved in this aspect of the operation, it believes that the Emotet cleanup will actually start in April, not March.
“Reports are out showing reverse engineers claim that the replacement binary will uninstall Emotet on March 25. We believe this report contains an error. In many programming languages, the month values start counting at 0, where 0 = January, 1 = February, etc. This maps to April instead of March. The date structure corresponds to 25 April 2021 at noon.”
Related: NetWalker Ransomware’s Sites Seized by Law Enforcement
Related: CISA Warns of Emotet Trojan Targeting State, Local Governments













