Moscow-based Kaspersky Lab on Thursday unveiled its analysis on a series of targeted attacks that hit numerous online gaming companies around the world.
According to the research posted today, the attacks came to the attention of its researchers toward the end of 2011, when a Trojan had infected a large number of computers, which an investigation determined that virtually all were used by players of a popular online game.
“It emerged that the piece of malware landed on users’ computers as part of a regular update from the game’s official update server,” Kaspersky Lab noted a post to its Securelist blog. “Some even suspected that the publisher itself was spying on players. However, it later became clear that the malicious program ended up on the users’ computers by mistake: the cybercriminals were in fact targeting the companies that develop and release computer games.”
The goal of the attacks is to gain access to source code and legitimate digital certificates from software makers, Kaspersky said. If the attackers are able to compromise gaming platforms, in some cases they are able to manipulate in-game currency that players can use to convert into real-world money.
The hacking group behind the attacks is alleged to have Chinese origins, which Kaspersky is calling “the Winnti group“—named after Symantec had first labeled the malware family Winnti.
Kaspersky said the affected game publisher had approached them to ask if they could analyze the malware that was discovered on its update server.
Kaspersky researchers determined that the malware was a DLL library compiled for a 64-bit Windows environment and came along with malicious, but properly signed (legitimate) driver. The DLL contained a backdoor payload, which gave attackers a fully functioning Remote Administration Tool (RAT), allowing them to control victims’ computers without their knowledge.
What the researchers also discovered was that the digital signature used belonged to South Korea-based KOG, another online video game maker. Kaspersky said that they contacted KOG and also alerted Verisign, the CA that issued the certificate, which was eventually revoked.
The KOG certificate was not an isolated one-time event, and it appears that the attackers have a hunger for stolen certificates.
“When we discovered the first stolen digital certificate we didn’t realize that stealing the certificates and signing malware for future attacks against other targets was the preferred method of this group,” Kaspersky said. “Over the next 18 months we discovered more than a dozen similar compromised digital certificates.”
“Moreover, we found that those digital certificates seemed to have been used in attacks organized by other hacking groups, presumably coming from China,” Kaspersky added.
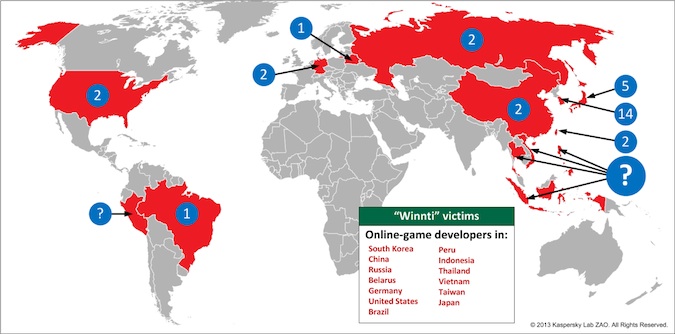
Throughout its investigation, Kaspersky Lab found more than 35 gaming companies that had been infected as a result of the Winnti attacks.
While most were online video game maker from East Asia, other firms in Germany, the United States, Japan, China, Russia, Brazil, Peru, and Belarus were hit, Kaspersky said.
Kaspersky did acknowledge that they were not the first to disvover the attacks, noting that HBGary investigated an incident for a US-based video game company in 2010 that turned out to be related to the Winnti group.
Where did the attacks originate from?
While vendors (Mandiant aside) are always hesitant to point fingers on the record, Kaspersky Lab at least says the attackers can speak Chinese, and noted that some of the code contained text in Chinese Simplified GBK coding. Other supporting evidence was that the authors of the malware used AheadLib to create the malicious libraries, a program that has a Chinese interface. However, the analysis showed that that the authors may not be 100 percent Chinese speaking, and found that some of the attackers were working on a Korean Windows operating system.
Additionally, the Winnti group makes use of a popular backdoor known as PlugX which also has Chinese origins and has been seen used in attacks targeting Tibetan activists, Kaspersky said.
“Our research revealed long-term oriented large scale cyberespionage campaign of a criminal group with Chinese origins,” Kaspersky said.
Kaspersky said the Winntigroup has distinguishable features that make it stand out from others:
• Massive abuse of digital signatures; the attackers used digital signatures of one victim company to attack other companies and steal more digital certificates;
• Usage of kernel level 64-bit signed rootkit;
• Abusing great variety of public Internet resources to store control commands for the malware in an encrypted form;
• Sharing/selling stolen certificates to other groups that had different objectives (attacks against Uyghur and Tibetan activists);
• Stealing source codes and other intellectual property of software developers in online gaming industry.
In terms of the command and control infrastructure, Kaspersky identified over one hundred malicious programs, each one compiled to attack a particular company, with separate C&C domains typically assigned to each individual company.
“Virtually all the C&C domains were arranged as follows: a second-level domain was created without a DNS A-record, i.e., there was no IP address assigned to it,” Kaspersky said.
More details in the C&C infrastructure and domains used in the attacks can be seen in Kaspersky’s blog post.
A full (longer) technical analysis from Kaspersky Lab is available here.
















