New Information Security Resource Provides Guidance that Addresses the People, Process, Organization and Technology Aspects of Information Security.
The ISACA this week published the Business Model for Information Security (BMIS), as an educational resource for security professionals and to provide comprehensive guidance that addresses the people, process, organization and technology aspects of information security.
The Business Model for Information Security (BMIS) presents a holistic, dynamic solution for designing, implementing and managing information security. As an alternative to applying controls to apparent security symptoms in a cause-and-effect pattern, BMIS examines the entire enterprise system, allowing management to address the source of problems.
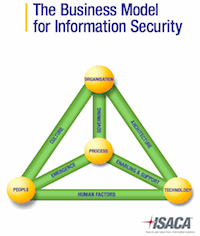
BMIS can be used in enterprises of all sizes and was developed to be compatible with other information security frameworks that may already in place. It’s vendor and technology neutral and is applicable across all industries, countries, and regulatory and legal systems. It encompasses traditional information security and privacy, and provides links to risk, physical security and compliance.
“Too much time is being spent on providing reactive, short-term, technology-focused solutions to constantly changing environments,” said Jo Stewart-Rattray, CISA, CISM, CGEIT, director of information security at RSM Bird Cameron and a member of ISACA’s Knowledge Board. “This type of fix is short-sighted. It does not prevent security weaknesses resulting from poor governance, a dysfunctional culture or untrained staff—all aspects addressed by this new model.”
“ISACA has transformed the theoretical model into a practical tool that security practitioners can use to connect security projects with business strategy,” said Rolf von Roessing, CISA, CISM, CGEIT, international vice president of ISACA. “The Business Model for Information Security takes a business-oriented approach, focusing on people and processes in addition to technology.”
The ISACA says that to understand the model, it is important to distinguish amongst models, standards and frameworks. While BMIS can help overcome some of the known difficulties in information security, it is primarily a model that must be supported by additional standards and frameworks.
The ISACA is a nonprofit association that serves more than 95,000 information security, assurance and IT governance professionals.
BMIS is available as a free download to ISACA’s members. Nonmembers can purchase print editions for $60 and members can purchase print copies for $45. A free introductory guide is available to all at: www.isaca.org/bmis.












