Apple has released its first Rapid Security Response update, but many iPhone users have complained that they are having problems installing the ‘iOS Security Response’.
The tech giant announced Rapid Security Response in June 2022, when it informed customers that the feature would become available in iOS 16 and macOS Ventura.
This feature enables Apple to deliver important security patches to Macs and iPhones between standard software updates, and the company initially said the fixes would be applied automatically without requiring a reboot.
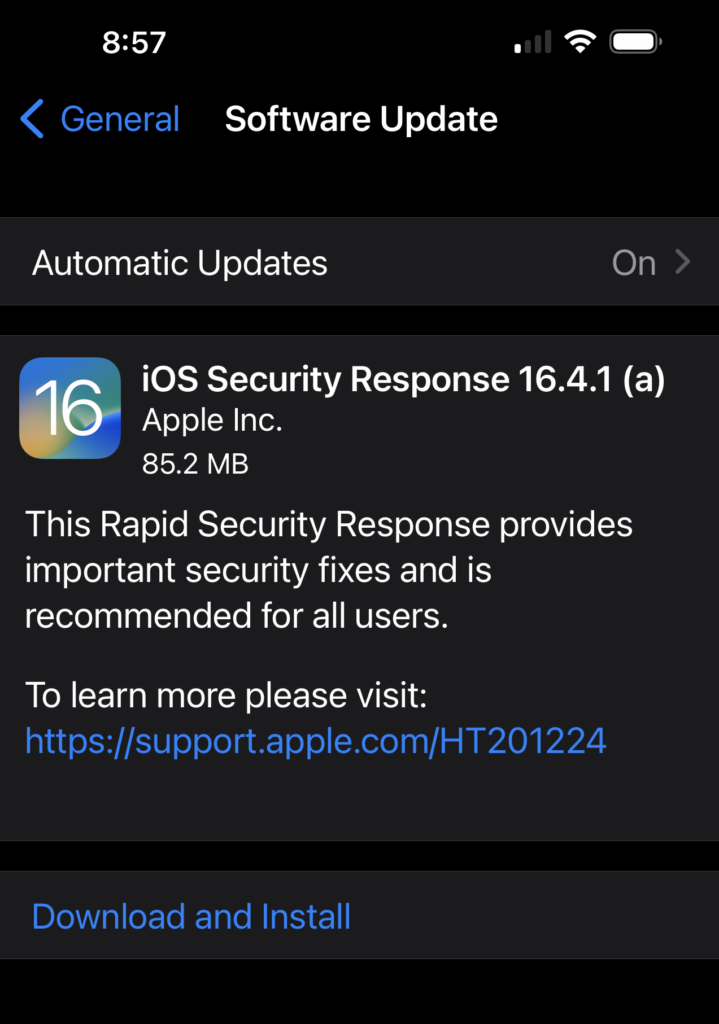
The first Rapid Security Response update was rolled out to iPhones running iOS 16.4.1 and Macs running macOS 13.3.1 on Monday. However, Apple has not published any new security advisories so it’s unclear what vulnerabilities have been addressed with the update.
Many of the recently patched iOS flaws have been exploited in attacks by the products offered by commercial spyware vendors.
In a support document published on Monday, Apple clarified that Rapid Security Responses can deliver improvements to Safari, WebKit or other critical system libraries.
“They may also be used to mitigate some security issues more quickly, such as issues that might have been exploited or reported to exist ‘in the wild’,” Apple explained.
However, many iPhone users complained that they were unable to install the critical update, receiving an error that reads “Unable to Verify Security Response”.
Some of the impacted users later reported being able to install the update, but SecurityWeek can confirm that the update still doesn’t work on some iPhones, more than 12 hours after it started rolling out.
When users install a Rapid Security Response update, a letter will be added to their software version number — for example, in this case it’s 16.4.1 (a) or macOS 13.3.1 (a).
“If you choose to turn off this setting or not to apply Rapid Security Responses when they’re available, your device will receive relevant fixes or mitigations when they’re included in a subsequent software update,” Apple said.
The company has clarified that a reboot of the device might still be needed in some cases. This first update does require a device reboot.
Related: Apple Ships Urgent iOS Patch for Newly Exploited Zero-Days
Related: iOS Security Update Patches Exploited Vulnerability in Older iPhones
Related: Apple Patches Exploited iOS Vulnerability in Old iPhones













