Cisco paints a grim picture for 2014 in its annual security report, predicting “unprecedented growth” for advanced malicious attacks. The barrage of non-stop attacks is also taking a toll on the defenders.
Cyber-attackers are increasingly more organized and sophisticated, launching attacks with clearly defined goals, Cisco said in its 2014 Annual Security Report, released Thursday. Threats range from fairly-simple-but-effective social engineering attacks to steal passwords and other credentials and more elaborate network infiltrations. Cisco specifically highlighted the exponential growth in mobile malware as well as the trend of compromising Web hosting data centers.
The increasing level of attacks are compromising “the trust required for economic transactions, government services, and social interactions,” the report said.
 Internet Infrastructure Under Attack
Internet Infrastructure Under Attack
Perhaps the most worrying finding in Cisco’s report is the fact that cyber-criminals have learned that targeting Internet infrastructure—large Web hosting data centers with powerful servers and extensive bandwidth—yields very high returns, said Levi Gundert, Cisco’s technical lead for threat research, analysis, and communications. The attackers are building up networks of these powerful machines to launch a broad array of attacks against other networks and machines, such as distributed denial-of-service (DDoS) attacks, Gundert said. More attacks launched by compromised servers are on the way.
Attackers are launching campaigns to gain access to these servers “with the goal of proliferating attacks across legions of individual assets served by these resources,” the report said.
The wave of DDoS attacks targeting financial institutions throughout 2013 was tied to Brobot, a group of compromised Web servers in several data centers around the world. More attacks to compromise Web hosts are on the way, and more powerful attacks are looming.
Threats and Vulnerabilities
Overall vulnerabilities and threats reached their peak since 2000, according to the report. Based on a sample of 30 of the world’s largest Fortune 500 companies, all of them had traffic going out from their network to Websites hosting malware. All of them had also been targeted by malicious traffic, as well.
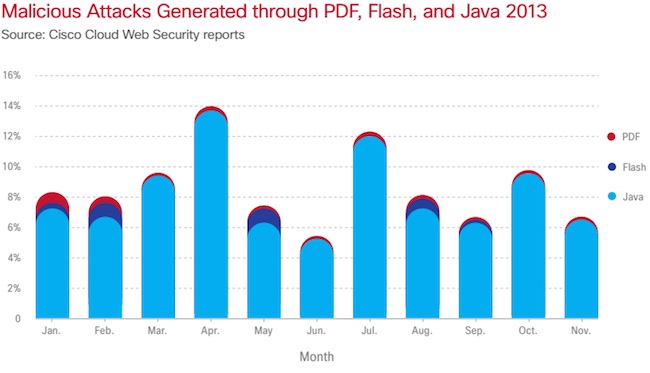
Cyber-attackers are focusing a bulk of their energies exploiting vulnerabilities in Adobe Reader, Microsoft Office software, namely Word, Excel, and PowerPoint, and Java. What was surprising, however, the fact that Java accounted for a whopping 91 percent of all indicators Cisco looked at in 2013. Gundert said he had expected the other technologies to have a slightly larger piece of the overall pie.
The popularity of mobile devices and cloud computing expands the attack surface, giving criminals more opportunities for attack. “New classes of devices and new infrastructure architectures offer attackers opportunities to exploit unanticipated weaknesses and inadequately defended assets,” the report found. Nearly all mobile malware, or 99 percent, target the Android operating system, Cisco said.
Targeted Organizations
Organized crime is firmly entrenched in cyber, with cyber-criminals shifting away from fairly simple but attention-grabbing attacks to much more sophisticated, well-funded attacks. Cyber-criminals have clearer motivations, whether it’s for financial gain or reputational damage. They are also far more focused in their targets, whether it’s targeting public organizations or the private sector, and even by the industry.
Agriculture and mining, pharmaceutical and chemical, and electronics were the most frequently targeted sectors, according to the report. Attackers are also increasingly targeting oil, energy, and gas companies, Cisco found. The finding feels prescient, considering Kaspersky Lab’s announcement of Javafog, a sophisticated malware which targeted at least one independent oil and gas company, just this week.
Organizations need to examine their security model holistically so that the defenders understand who the attackers are, the motivations behind the attack, and the methods used, Gundert said.
Skills Gap
Cisco also touched upon the oft-discussed skills gap in its report, claiming a “worldwide shortage of nearly a million skilled security professionals.” Organizations are struggling to find security professionals who have the skills to monitor and secure networks from the sophisticated technology and tactics used by online criminals. Most organizations do not have the people of the systems to continuously monitor extended networks and detect infiltrations, and then apply protections in a timely and effective manner, Cisco said.
But it isn’t just finding enough security professionals to defend against threats. Gundert acknowledged part of the problem lies in the fact that many security professionals don’t have the deep industry knowledge necessary to effectively deal with specific threats and issues the organization is facing.
With the shortage, more businesses will be looking to outsource their services. This means providers and technology companies have to first secure their supply chain, and then be able to assure customers they take security seriously, Gundert said.
Organizations need to decide what is the “most important from a cybersecurity perspective,” Gundert said.
Cisco’s full report is available online in PDF format.















