Hackers could in many organizations easily gain access to industrial environments from the corporate network, according to an analysis conducted by Positive Technologies.
The study, based on data from nearly a dozen companies around the world in the oil and gas, metallurgy, and energy sectors, found that the corporate network perimeter can be penetrated in 73% of cases, often due to misconfigurations.
All of the tested companies had SSH, Telnet, RDP and other administration interfaces exposed, and 91% relied on dictionary passwords for privileged users. Other types of security holes on the corporate network perimeter included exposed DBMS interfaces (82%), vulnerable software (64%), use of insecure protocols (64%), arbitrary file upload flaws (45%), remote command execution vulnerabilities (36%), and excessive software and user privileges (36%). The difficulty of exploiting these flaws was in nearly 80% of cases described as “low” or “trivial.”
Within the corporate network, researchers found a wide range of weaknesses that could have allowed malicious actors to escalate privileges and move laterally. Weak passwords, vulnerable software and operating systems, and flaws in network segmentation and traffic filtering were the most commonly found issues.
Once inside the corporate network, attackers could have moved to industrial environments in 82% of cases. In nearly two-thirds of the analyzed companies, hackers could have gained access to the industrial network using special control channels that bypass the demilitarized zone (DMZ). In 45% of cases, investigators found poor traffic filtering between the networks, and in other organizations there was either no DMZ between the networks (18%) or no network segmentation (18%).
“These flaws are of high severity because if the attack is successful, critical servers are compromised. It might seem that having a dedicated channel for remote control of gateway servers is less risky, because an attacker would need to obtain access to specific workstations in the corporate information system. But it is an illusion that such a solution is secure. This method of penetrating the industrial network was successfully demonstrated in most test cases,” Positive Technologies said in its report.
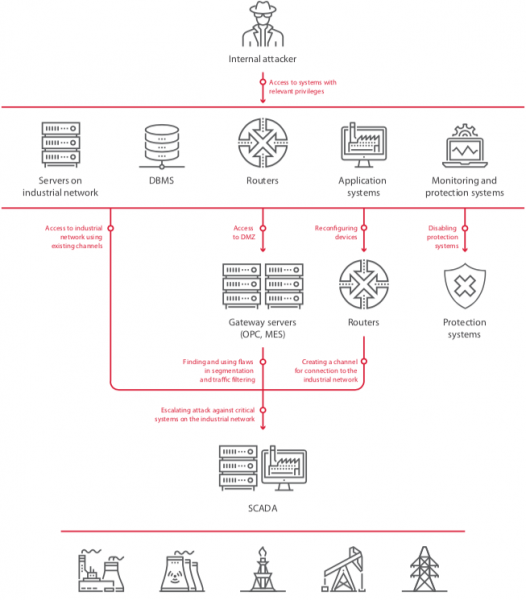
Even if network segmentation has been properly implemented, an attacker can often still gain access to industrial systems, the study shows. This involves accessing the firewall with admin privileges and reconfiguring it to allow a connection from a malicious or compromised device.
Researchers found that obtaining the needed credentials is in many cases easy, again due to weak or poorly protected passwords. Attackers can obtain credentials from corporate IT systems where they are often stored in clear text, through brute-force attacks aimed directly at the firewall, or by obtaining encrypted passwords and cracking them.
Related: Energy Sector Most Impacted by ICS Flaws, Attacks
Related: Oil and Gas Sector in Middle East Hit by Serious Security Incidents
Related: Industrial Firms Slow to Adopt Cybersecurity Measures












