Enterprises Blind to up to 36% of Their Network Traffic, According to Recent Study
Sunnyvale, California based Palo Alto Networks released the latest edition of its Application Usage and Risk Report today. These types of reports are always interesting, as they give a true view into what’s happening inside business networks around the globe. Different in scope than survey based reports, this report is based on data collected from 1,253 Palo Alto Networks participating customers.
The report revealed that more than 40% of the 1,042 applications that were identified on enterprise networks in the study, can now use SSL or hop ports to increase their availability within corporate networks. This segment of applications will continue to grow as more applications follow Gmail (by default), Twitter, Facebook, and others, who all have enabled SSL either as a standard setting or as a user-selectable option.
 While a shift to SSL brings additional privacy and security to end users, it’s creating a significant challenge for IT security departments and making enterprises more vulnerable to threats and data loss.
While a shift to SSL brings additional privacy and security to end users, it’s creating a significant challenge for IT security departments and making enterprises more vulnerable to threats and data loss.
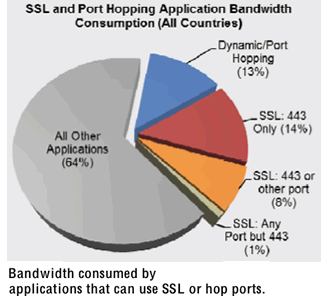
According to the report, roughly 36% of enterprise network traffic is comprised of hundreds of applications that can evade the controls of conventional security solutions by either using SSL or port-hopping capabilities. Interestingly, the majority of this traffic is not from browser-based applications using HTTP over SSL on port 443.
Encrypted SSL sessions typically bypass most security measures provided by many firewalls, intrusion detection systems, and DLP systems, creating a blind spot that most IT organizations have not yet adequately addressed.
“This data should be a wake-up call for IT teams who assume encrypted traffic is mainly HTTPS or for those who still believe that social networking usage is not taking place on their corporate networks,” said Rene Bonvanie, vice-president of marketing at Palo Alto Networks.
These concerns over SSL traffic in the enterprise aren’t meant to suggest that SSL is bad, and should not be used. SSL clearly provides significant benefits, helping to protect data, financial transactions, Web-based communications, and much more. It’s important, however, to highlight just how many applications can use SSL and what may be hiding within enterprise networks. Palo Alto Networks notes that there are many obvious cases where the use of SSL is duplicitous: On one hand, it is meant to secure the payload, while on the other, it is used because it will easily traverse a firewall because it can use a commonly open port. The company advises organizations to consider policy adjustments to account for those applications that can use SSL in some way, shape or form.
Also highlighted in the report is the undisputable fact that the workplace has become more social. Compared with 12 months ago, Instant Messaging (IM) traffic, as a percentage of overall traffic has more than doubled, while webmail and social networking increased nearly five times.
“What we learned from analyzing this tremendous amount of enterprise application traffic is to never assume anything about end-user behavior,” Bonvanie added.
The data used to compile the report came from Palo Alto Networks next-generation firewalls placed within customer networks, running in either tap mode or virtual wire mode, where they monitor traffic crossing the Internet gateway. The latest report, in its 7th edition, provides an interesting view into application usage by assessing 28 exabytes of application traffic from 1,253 enterprises around the world between October 2010 and April 2011.















