On the heels of news earlier this week that Microsoft led an operation that resulted in the takedown of several Zeus botnets, on Wednesday more news came from the security industry on the successful takedown of yet another large botnet.
On Wednesday, experts from Kaspersky Lab along with others including experts from newly formed security firm CrowdStrike, Dell SecureWorks and members of the Honeynet Project, announced the successful takedown of the second Hlux/Kelihos botnet. (Microsoft refers to the botnet as Kelihos, while Kaspersky calls it the Hlux botnet.)
The History
 Back in September 2011, Microsoft led the takedown of the original Kelihos botnet that was estimated to have as many as 40,000 bots. Kaspersky Lab, SurfNet and Kyrus Tech also contributed to the effort. Not long after that takedown, however, evidence that whoever was behind the operation appeared to still be in business and producing malware, though the botnet was not yet been back in action. That evidence was a sign of what was to come.
Back in September 2011, Microsoft led the takedown of the original Kelihos botnet that was estimated to have as many as 40,000 bots. Kaspersky Lab, SurfNet and Kyrus Tech also contributed to the effort. Not long after that takedown, however, evidence that whoever was behind the operation appeared to still be in business and producing malware, though the botnet was not yet been back in action. That evidence was a sign of what was to come.
In January 2012, Kaspersky Lab released new research showing that a second Hlux/Kelihos botnet was operating in the wild– one that would end up being almost triple the size of its predecessor. According to Kaspersky’s numbers, the second version of the botnet had an army of more than 116,000 infected systems, or bots.
The malware used in the botnet had been built using the same coding as the original Hlux/Kelihos botnet but also contained few new updates, including infection methods and Bitcoin features for mining and wallet-theft.
The Takedown Process
During the week of March 19, 2012, the collaborative effort including Kaspersky Lab, CrowdStrike, Dell SecureWorks and the Honeynet Project kicked off a “sinkholing” operation that resulted in the successful takedown of the botnet.
In order to be more resilient and not rely on a single command and control (C&C) server to stay in operation, both Hlux/Kelihos botnets utilized peer-to-peer (P2P) type technology, which enabled every bot in the network to act as a server and/or client.
According to Kaspersky Lab, in order to neutralize the flexible P2P botnet, the group created a global network of distributed machines that were installed into the botnet’s infrastructure.
“After a short time, our sinkhole-machine increased its “popularity” in the network – which means that big part of the botnet only talks to a box under our control,” explained Stefan Ortloff, a Kaspersky Lab Expert in a blog post.
At the same time, the sinkhole started to prevent the cybercriminal operators from accessing and sending commands to the bots. “As more infected machines were neutralized, the P2P architecture caused the botnet’s infrastructure to ‘sink’ since its strength weakened exponentially with each computer it lost control of,” Kaspersky Lab explained in a statement.
“We also distributed a specially crafted list of job servers,” Ortloff added. “This prevents the bots from requesting new commands from the malicious bot-herders. At this point, the bots can no longer be controlled by the bad guys.”
But the botnet operators would not go down without a fight. These operators put significant effort into developing and growing their botnet empires and have much to lose when their operations are taken offline.
“A few hours after we started our takedown operation, the bot-herders tried to take countermeasures by rolling out a new version of their bot,” Ortloff explained. “We also noticed that the bot-herders stopped their network from sending out spam and DDoS-attacks. Also the botnets’ fast-flux-network list remains empty since a few hours.”
Botnets Can’t Be Sinkholed Forever. What Now?
As Ortloff explains, until the cybercriminals behind these botnets are permanently brought down, new botnets with updated malware will continue to emerge and infect computers. The current sinkhole can’t be in operation forever, and is a temporary action that will ultimately will need to come down.
“The only real solution would be a cleanup of the infected machines,” Ortloff noted. “We expect that over time, the number of machines hitting our sinkhole will slowly decrease as computers get cleaned and reinstalled.”
But for the time being, there are many things that can be learned as a result of the operation that could help neutralize the botnet for the long term. “There is one other theoretical option to ultimately get rid of Hlux: We know how the bot’s update process works. We could use this knowledge and issue our own update that removes the infections and terminates itself,” Ortloff said. “However, this would be illegal in most countries,” he concluded.
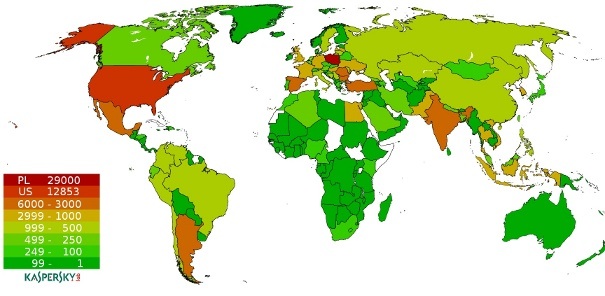
A map provided by Kaspersky Lab showing the infections by geographic location for the latest Hlux botnet is below.