Google Details Its Implemenation of Tiered Access to Secure Devices for its Global Workforce
The easiest solution to access control is binary: network access is either granted or denied. It’s a blunt tool that doesn’t suit the modern business culture of maximizing user productivity and creativity. Granularity in access control, allowing users to access what is needed when it is needed, is a more suitable model for the modern business.
Google chose the Tiered Access model for its own workforce of some 61,000 employees. In a new whitepaper (PDF) and blog published today, it explains that it has “a culture of innovation that requires the freedom and flexibility to connect many different devices to many different assets and services.”
This is an attitude that will resonate with many modern businesses.
“Tiered access was implemented in order to provide an access model appropriate for [Google’s] very heterogeneous environment. It helps ensure the security of corporate resources while allowing users to make informed trade-offs around access and security controls.” Many organizations offer their staff flexibility in the devices they use — especially where a BYOD policy is in place.
Tiered access is achieved by first analyzing the client base devices and data sources; analyzing the services that are to be accessed; and choosing a gateway/access technology that can evaluate policies and make access decisions between the client base and service.
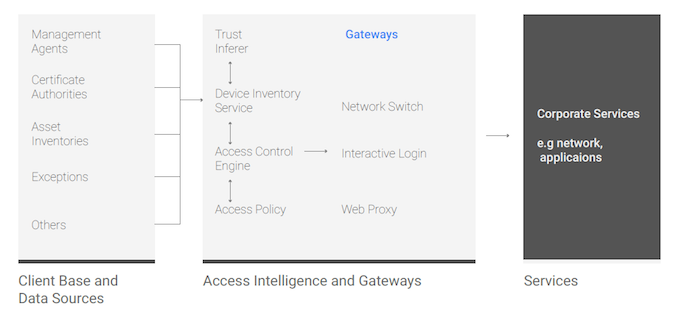
Google uses its own internally developed tools to collect the device data; but suggests other companies could use security reporting systems (logs), patch management systems, asset management systems and centralized management dashboards. The purpose is to gather device attributes and device state into a central repository.
The device attributes allow the definition of device baselines, based on things like vendor and operating system, and built-in security features. The device state, continuously monitored, highlights deviations from the device baseline. These two attributes can be used to associate devices to the different tiers.
“For example,” explains Google, “an Android device at Google may access more sensitive data in higher trust tiers if it is a ‘Fully Managed’ device, meaning it provides full device control and access to detailed system and network logs.” A lower trust tier is made accessible to BYOD devices with a work profile.
Between the device and the service sits an Access Control Engine that provides a service-level authorization to enterprise applications on a per-request basis. It queries the central repository in order to make policy decisions on what access is allowable — it is where policy is defined and managed by security.
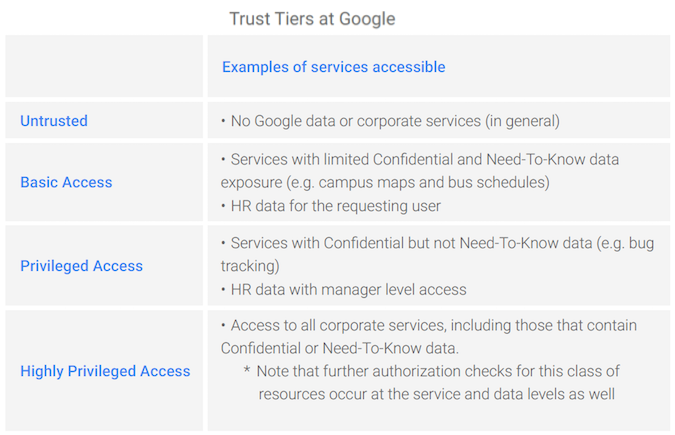
The ‘tiers’ in tiered access are levels of sensitivity applied to the organization’s different services. Google uses just four tiers: untrusted; basic access; privileged access; and highly privileged access. It chose four tiers as a compromise between too many (making the system over-complex), and too few (which effectively recreates the binary access that the tiered approach seeks to improve).
While this is the current state of Google’s tiered access solution to its on-site and mobile workforces, development is ongoing. It has four areas currently under consideration. The first is to increase the granularity of the system by improving “the precision of access decisions while balancing the need for users to understand security requirements.”
The second is to add user attributes to the device attributes by considering “the user’s observed behavior and how that compares to normal activity as analyzed with machine learning.” This will allow access based on both the device and current user behavior.
The third is to drive self-selection of trust tiers by encouraging people to voluntarily move across trust tiers in real-time; for example, to be at ‘fully trusted’ for the next two hours only.
Finally, Google hopes to improve the service on-boarding process. Since services are added or updated all the time, they all need to be classified in terms of risk and sensitivity. “To scale,” suggests Google, “service owners must be empowered to make the right tier assignments themselves, which is a process that is constantly improving.”
Google hopes that by sharing its own experiences in developing and deploying tiered access, IT and security admins will feel empowered to develop a flexible and powerful access control system that better suits today’s business. Its Tiered Access project goes hand-in-hand with the larger BeyondCorp project that challenges traditional security assumptions that private or ‘internal’ IP addresses represented a ‘more trusted’ device than those coming from the internet. Part of BeyondCorp is discussed in the Google Infrastructure Security Design Overview.









