An exploit kit is a framework that automates the exploitation of client-side vulnerabilities, targeting browsers and programs that can be invoked through the browser. These kits can be obtained on the cyber black market, where they are sold or rented.
These kits allow cybercriminals to outsource the infection part of their malware campaign and focus on the development and management of their malicious payload. Therefore, Exploit kits are a highly popular choice for client side exploitation. Dell estimates that “70%-80% of [client side malware] attacks via the Internet now originate from exploit kits and expects to see continued focus and growth of these kits”.
Currently, exploit kits are mostly targeting Java related vulnerabilities. In this article we will dive into the history of exploit kits and their exploitation of other products, in order to find out what should a vendor do to better protect its customers.
Taking a deep dive into the exploit ocean
Last year, Deep Research had published an excellent poster, visualizing the different active exploit kits and the vulnerabilities they are exploiting, clustered by the targeted product.
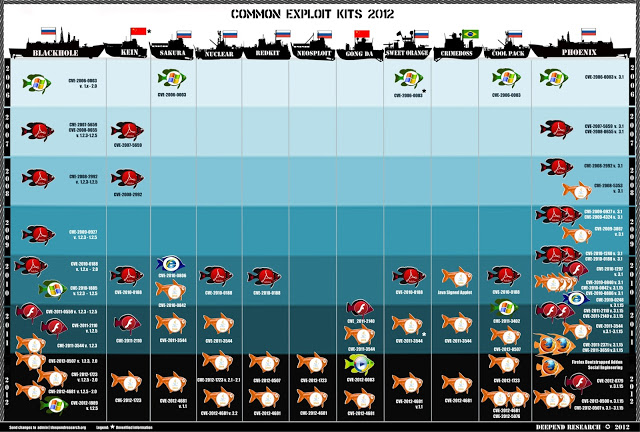
Exploit Kit Vulnerabilities’ Exploitation by Vendor (Original image by Deepend Research)
One of the hallmarks of a good visualization is the ability to derive meaningful insights out of it, and this one is no exception. Diving into the deep water depicted by the poster, we can clearly define four distinct eras within the described timeframe:
• Internet Explorer (IE) Exploitation era ( until early 2007)
• PDF Reader Exploitation era (early 2007 – late 2010)
• Flash Exploitation era (late 2010 – mid 2011)
• Java Exploitation era (mid 2011 – present)
By correlating the end dates of the different eras with the relevant product news, an interesting connection between the end of the exploitation era and increased “software genetic diversity” becomes visible.
Internet Explorer (IE) Exploitation era ended on early 2007. On November 2006, Internet Explorer version 7 was pushed as a high priority automatic update, which made the execution of the vulnerable ActiveX depend on further user interaction. Additionally, on the first quarter of 2007, IE dropped from 80% marketshare for the first time.
On the first quarter of 2007, Internet Explorer dropped from 80% market share for the first time The PDF exploitation era ended on late 2010, just when (December 2010) Google Chrome version 8 introduced the PDF sandbox. The Flash exploitation short era was ended on mid-2011 when Chrome introduced (March 2011) the Flash Sand box.
Those who cannot learn from history are doomed to repeat it
A clear corollary of this article, is that creating a greater “gene pool diversity” is vital for protecting the users of a certain product from mass exploitation. The diversity changes the economic equation for the attackers and makes them search other, less diverse environments to attack. Ever since the browser market has moved from the Internet Explorer monopoly to the oligopoly of Google’s Chrome, Firefox and Internet explorer, we see very little large scale direct browser attacks.
Java should follow the example of Flash and PDF and artificially generate such diversity, by shielding the problematic software with a browser implemented sandbox. By following that method, we create genetic diversity as the sandbox implementation varies between different browser vendors and make the attacker to work harder in order to find two holes (original exploit in the sandboxed component plus sandbox exploit) instead of one. Note that this method seems to be effective even when only some of the possible victims are protected. When Google Chrome provided that extra shielding around PDF and Flash, it was enough to drive exploit kits away from the technology.













