A Higher Education Student Database is an Identity Thief’s Dream Come True…
No more fertile ground for security breaches exists in the United States than our colleges and universities. The confluence of enormous stores of identity data, atmospheres of freedom of information, and ready-made teams of socially motivated hackers chosen from the best and brightest our country has to offer make this claim close to a certainty.
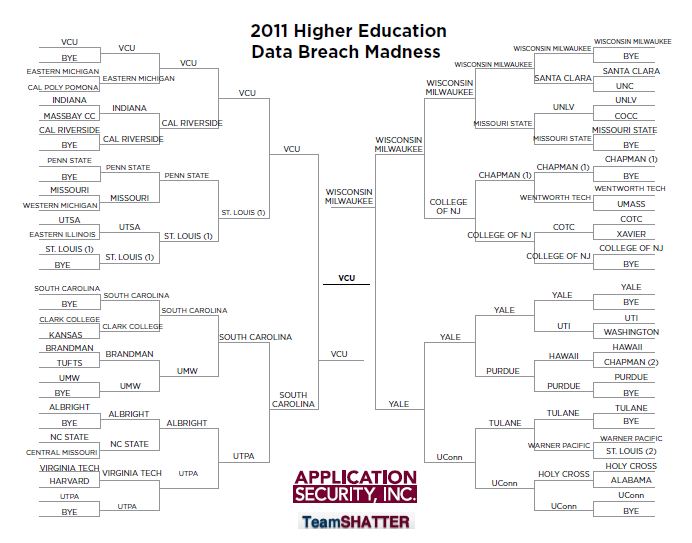
To wrap some humor and substance around this perfect-storm prediction: Database security researchers at Application Security, Inc. have put together a “Higher Education Data Breach Madness” bracket competition.
While 2011 witnessed a dramatic decrease from 2010 in the number of reported records affected (478,490), 48 institutions still suffered breaches. The 2011 Higher Education Data Breach Madness “champion” was Virginia Commonwealth University, which reported a breach of 176,567 records on Nov. 11, 2011. Rounding out the 2011 “Final Four” were the University of Wisconsin Milwaukee (79,000), Yale University (43,000) and the University of South Carolina (31,000).
Even with the each of the forces of the storm working against a college or university, survival (avoiding a breach) is a viable option. Let’s look at these forces and consider defense options for each that should be part of every higher education’s mentality:
Stores of identity data As far as higher education is concerned, the question is not, What information do we have in our databases? but rather, What information don’t we have? One doesn’t just sign up for college with a name and address. Students provide scholarship information, class placement, ethnic and religious backgrounds, medical information, former education, placement tests and the like. And not just for the student, but also for parents and, sometimes, siblings as well. Financial aid, sought by the majority of students, requires intimate financial and personal information about the student’s family. Once in school, additional student data is collected on classes taken, grades, academic problems, additional medical history, clubs and associations, student credit cards and anything else that can be recorded.
Compound this collection of data with the fact that a new set of identities is collected every year for new students as well as for students who apply but are not accepted or choose not to attend, then multiply this by the age of the college – and you are looking at a huge number of identities.
It gets better, or worse. The collection of student identities from years back will have transformed itself into a collection of business professional identities, by the very fact that most students will (hopefully) find themselves in the business world. A student’s age may have changed, but not his Social Security number or the answers to those tricky questions used for verification (e.g., mother’s maiden name, first sibling’s name). As a student moves from being poor to earning a living, his identity becomes worth much more. And, if the college is deeply into alumni funding (and which college is not?), former student information is being updated as quickly as possible.
Truly, a higher education student database is an identity thief’s dream come true. A student’s identity record reads like a credit application, with all the information there for the using. The data is prime bait for a spear phishing attack; who better to get your attention (and your dollars) than the Society of Professional Curlers (or its fraudulent equivalent) that you used to belong to?
My advice for any institution of higher education is to purge and encrypt. For example, even if basic medical data (i.e., childhood diseases and immunizations) was needed during the enrollment and attendance, it may not be needed once the student has graduated. Build your IT systems so that certain data types are automatically purged after the student reaches a certain age. If you make it automatic, unneeded data won’t be there to be stolen.
Making data breaches even more disastrous is the frequent ability for the thief to make quick use of the stolen information. Storing data in unencrypted databases is always distressing. IT systems built before our current age of web application access can no longer rely on a sturdy physical door and firewalls for protection. Today, with a web application server sitting next to your student information database, a single SQL Injection might allow a hacker to quietly steal the identities of your entire (past and present) student population.
Database encryption is fast, easy and relatively inexpensive. An encrypted database, even if stolen, cannot be used maliciously. Carefully read any news reports on security breaches; when you see the words ‘but the data was encrypted,’ you are really reading, “We are embarrassed, but we’re not going to get our butts sued.” I would suggest encrypting anything that is remotely private. And, make sure your encryption practices are solid – at a minimum, use the latest algorithms and safe storage of encryption keys.
Finally, make sure you periodically back up your database, then save the backups to an offsite location in an encrypted format. This is easily implemented and free with most commercial backup software.
Freedom of information
The primary target of cyber crime is access to information – financial (credit cards, bank accounts), identity (Social Security numbers, names, addresses), and government and commercial (i.e., product information, plans, strategies). The primary goal of security protection is the guarding of this information against unauthorized access.
While businesses understand the need to protect information, colleges and universities often struggle with a culture of freedom of information that makes security implementations difficult. Large companies are in business to make money; higher education institutions are in the knowledge business, making it is far more difficult to consider limiting access. As said by Phillip Britt (July 1, 2005, Information Today), “Institutions of higher education have a special philosophy: Their desire is to supply knowledge to all those who seek it. But they are now finding that they have to balance this desire with adequate measures to protect sensitive student and alumni information.”
Corporations can set policies or change processes that provide for improved security fairly easily. Colleges and universities must fight philosophically charged battles that sometimes span decades of culture to incorporate those same changes. The transient nature of the higher education work force compounds the problem, where staff often comes from the student population itself and is replaced at least every four years. Access is granted to users who, from a security standpoint, have no business having access and should not be expected to keep access information confidential.

Colleges and universities need to maintain the same security focus as corporate America, on three fronts: fortified internal information systems, limited access to identity data, and awareness of social engineering attacks.
Fortified internal information systems – While nowhere as insecure as even a few years ago, colleges and universities still need to update and fortify their information systems. Inexpensive and easy preventions such as system updates and patches should be done as soon as they are available, all sensitive data should be encrypted, server rooms should be physically secured and robust password rules should be enforced.
Limited access to identity date – User access to any information system should be allowed only to the level of the user’s need. The clerical person at the university bookstore should be able to look up the class assignment of a student but not the student’s SSN. IT systems should support multi-level login permissions that permit the least invasive access possible.
Awareness of social engineering – The following excerpt is from SearchSecurity.com: Security experts propose that as our culture becomes more dependent on information, social engineering will remain the greatest threat to any security system. Prevention includes educating people about the value of information, training them to protect it, and increasing people’s awareness of how social engineers operate.
With students staffing many positions throughout the university, opportunities abound for fellow students or professional hackers to gain IT system access. What college sophomore would not hold the door to the server room open if an officious-looking workman with a toolbox approached? How much trouble would any caller using the words “This is IT. I have a trouble ticket here and need access to your login …” have of obtaining login credentials?
In a recent poll at social-engineer.org, 86% of the votes agreed that social engineering is the worst threat to security today. This reinforces the obvious: an understanding of social engineering is extremely valuable to anyone with access to computer systems; thus, it makes sense to educate university workers about the mechanism and hazards of social engineering.
Without staff awareness of social engineering scams and techniques, con artists will find the college and university environment an easy target.
Conclusion
Colleges and Universities are truly at the centers of perfect security storms. They contain identity information worth billions of dollars on the cyber black market, encourage cultures of information freedom, and don’t understand social engineering. This is compounded by often underfunded IT departments and transient administrative staffs who may be part of the hacker community or easily fooled into giving up computer system information.
The ramifications of a successful data breach are far wider than just bad press. The costs to institutions leaking data are large, often including payment for subsequent personal security monitoring and the need for expensive security teams brought in to determine and remediate security issues. Even more distressing, at least one university has been on the wrong side of a student filed class-action lawsuit based on a stolen student data.
However difficult it might be, institutions of higher learning need to think like businesses AND consider the enormous financial and reputational dangers of a data breach. Unlike many businesses, colleges and universities are under constant attack, from within as well as without.
Related Reading: College Cybersecurity Tightrope: Higher Ed Institutions Face Greater Risks















