Hackers can abuse legitimate features present in industrial controllers to hijack these devices and leverage them to gain a foothold in a network, a researcher warns.
Programmable logic controllers (PLCs) allow users to control and monitor physical processes in industrial environments. While these types of devices are known to have vulnerabilities, including ones that could be leveraged to create a dangerous worm, researchers have shown in the past that malicious actors may also be able to abuse legitimate PLC features to achieve their goals.
Roee Stark, a senior software engineer at industrial cybersecurity firm Indegy, has now demonstrated another type of attack that only leverages legitimate features. The expert has analyzed PLCs made by Rockwell Automation and found that certain Common Industrial Protocol (CIP) commands can be abused for malicious purposes.
“The cip commands in question are any commands relating to the cip socket object,” Stark told SecurityWeek in an email interview. “The socket object exposes a well known interface that allows its user to send and receive TCP or UDP traffic with minimal limitations. The socket interface is very robust and one can cause a controller to collect reconnaissance, exfiltrate data and even carry out attacks using known vulnerabilities. The 2nd feature involves cip’s advanced routing capabilities. It’s possible to cause a cip controller to forward cip requests that are encapsulated using various protocols (Ethernet/IP, ControlNet, DH+ etc.). This can be used to allow unauthorized access to networks that otherwise might be inaccessible to an attacker from a remote network.”
The attacks can be launched against any controller that supports these socket commands as long as the attacker has network access to the targeted PLC, the expert said.
However, he noted that the method leverages specific CIP commands and features and not the CIP protocol itself. The abused capabilities are documented, but not very well known.
Learn More About ICS Attacks at SecurityWeek’s 2019 ICS Cyber Security Conference
These types of attacks pose a risk not only to PLCs – the attacker can hijack any endpoint on the compromised network, including IT and industrial devices.
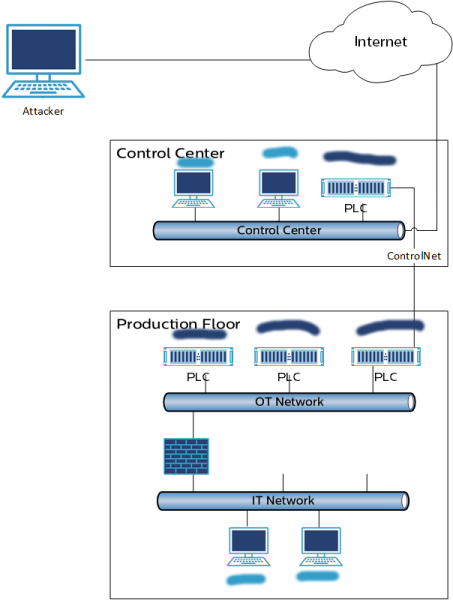
“Let’s assume there’s a SCADA control center that’s connected to the internet where there’s a controller that reads data from a controller on the production floor (with no internet connection) using ControlNet,” Stark explained. “If an attacker has access to the controller in the SCADA center, be it from the local network or via the internet, the attacker can identify the ControlNet connection and using a complex path gain access to the other controllers on the production floor. With access to the controller, the attacker can collect information by triggering various queries and scans using the socket interface. Once an endpoint is discovered, there’s nothing preventing the attacker from gaining access to it.”
Stark told SecurityWeek there is no evidence that this technique has been abused for malicious purposes, but warns that these types of weaknesses are more problematic than actual vulnerabilities as they cannot be easily addressed with a patch that has minimal impact. However, there are steps that the vendor and users can take to prevent potential attacks.
“The main problem is the lack of authentication,” Stark said. “If only authorized parties were allowed to execute these commands, it would make exploiting them much more difficult. Furthermore, there should be some sort of route whitelist so that forwarding packets via a complex path is much more controlled. There is also a huge blind spot with regard to these features, so better visibility is required to detect if someone unauthorized is using them.
“As for users, practicing proper network hygiene and monitoring activity will make it a lot more difficult for an attacker to remain undetected. This is not a security vulnerability, but rather the exploitation of a product’s intended capabilities,” he added.
Researchers have previously disclosed actual vulnerabilities in Rockwell Automation products that could have been exploited using CIP messages.
Related: Flaw in Schneider PLC Allows Significant Disruption to ICS
Related: PLCs From Several Vendors Vulnerable to Replay Attacks
Related: Severe Vulnerabilities Expose MicroLogix PLCs to Attacks













