Smart or Not, the Grid is an Important Piece of our Critical Infrastructure that Must be Carefully and Thoroughly Secured.
It seems that you can’t go a week without hearing something about the Smart Grid. Typically, you hear something that’s either wildly optimistic about the benefits of the Smart Grid, or something that’s incredibly gloomy about the state of Smart Grid cyber security. However, you rarely, if ever, hear an actual definition of what a Smart Grid is. This is because the term “Smart Grid” is so nebulous that it’s difficult to talk about. It’s really nothing more than an attempt to add “intelligence” to many aspects of energy transmission and distribution, in order to make the delivery of power more efficient and economical. The ultimate prize is greener, less expensive power. It’s the same power, of course, but there is less waste due to all of those efficiencies in transmission and distribution.
 What this equates to in terms of technological enhancements to T&D is difficult to outline, because it entails so much, including improvements in power management, better readings from synchrophasers, improved fault management, and of course, the poster child of the Smart Grid, advanced metering. “But wait,” you might say, “all of that is already here, today. Isn’t that the Smart Grid?” Some might agree with you, while others might claim that the Smart Grid is something grander and more elusive. The problem is that it’s part fantasy and part reality, and each area is being developed and deployed differently depending on who you talk to.
What this equates to in terms of technological enhancements to T&D is difficult to outline, because it entails so much, including improvements in power management, better readings from synchrophasers, improved fault management, and of course, the poster child of the Smart Grid, advanced metering. “But wait,” you might say, “all of that is already here, today. Isn’t that the Smart Grid?” Some might agree with you, while others might claim that the Smart Grid is something grander and more elusive. The problem is that it’s part fantasy and part reality, and each area is being developed and deployed differently depending on who you talk to.
Instead of trying to make sense of all that, I’m going to talk about the “Grid” and leave out the “Smart.” Looking at what is available and widely used today in energy T&D, we can see a lot of intelligence built into devices, as well as a lot of potential attack vectors.
Energy transmission involves the delivery of high-voltage electric energy to substations, where that energy can then be distributed to the consumer. From a cyber security perspective, energy transmission involves several important information paths and several unique digital assets. Important information paths include the communications of data regarding energy load and quality, because load-balancing is integral to the safe and efficient operation of the transmission system. This requires that measurements be taken frequently, throughout a highly distributed system, and that those measurements are communicated back to a central management resource. This requires new digital assets. Newer synchrophasers are able to take a much higher sample rate than before, and communicate more relevant data back to a central management unit than before using Transmission SCADA (TSCADA) systems. The communication might occur over radio, microwave, parallel fiber optics, or even over the power lines themselves. Capacitors, energy storage facilities, and safety systems are also becoming “smarter,” and many of these assets are interacting with TSCADA systems in a similar way.
From the substations to the energy consumers, energy is moved in lower voltages but involves similar management requirements. Energy distribution is very highly distributed, and high costs can be associated with outages and metering. Outages must be identified, located and, in many cases, a truck must be rolled to resolve the issue. Therefore, one of the key communications that must occur in order to make energy distribution efficient involves the availability of a power line (i.e., is the line delivering power, or has a circuit has been closed). Advancements in reclosers have started to address this– now if a circuit is tripped due to a temporary condition, it can be automatically reopened to keep the power flowing. These reclosers communicate through Distribution SCADA systems. Again, how they communicate varies, and includes radio, microwave, fiber and power line communications.
Lastly, there is metering. Metering gets the most attention in “Smart Grid” discussions because a smart meter is easy to understand, and because many smart meters have already been deployed globally. The meters are smart because they can communicate more data about energy usage than before, and they can do so over an Advanced Metering Infrastructure (AMI), communicating back to a central resource. The tired meter-reader of yester-year is replaced with an automated, efficient digital communications system.
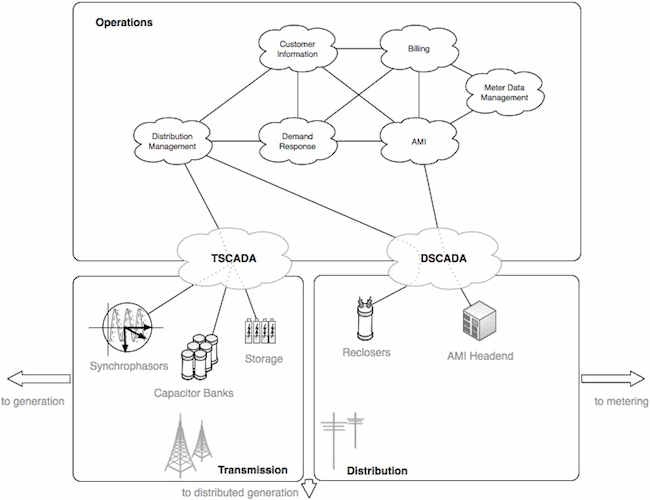
Add a variety of interrelated applications—from billing and customer management to demand response—and it becomes clear just how complex T&D really is. Now, within the context of SCADA cyber security, it should be very clear why there is so much concern about the nebulous “Smart Grid.” The grid today is already smarter than before, and as a result we have:
• More reliable and efficient energy T&D
• A larger digital attack surface against that same T&D system
Making the grid even smarter won’t change this, but it could intensify positive and negative implications.
Cyber security seems to be focused on energy generation, but what if a Stuxnet-class attack was engineered to target transmission and distribution systems? If the Phase Measurement Units (the aggregation point for synchrophaser readings) were compromised, could the safety of high-power lines be guaranteed? What if the distributed synchrophasers were targeted individually? What happens when demand response systems within the advanced metering infrastructure communicate misinformation?
The answer could be catastrophic disaster, or it could simply mean that the carefully tuned and balanced T&D system would become less so—it ultimately depends upon two things: how malicious and creative the cyber attacker is, and what their ultimate goal is; and how diligently we include T&D systems within our cyber security plans and procedures. For those who read my column regularly, this is where the record skips and my mantra can be clearly heard: protect every communication perimeter, and monitor everything. Monitor everything that is communicated to and from your PMUs and synchrophasors; monitor these devices directly; monitor distributed storage capacity, customer demand, recloser activity, and absolutely everything that occurs digitally within the grid. Then, bring it all together and correlate it against what you know already—including baseline behavior in the grid as well as activity within all of the energy generation facilities that can possibly influence that grid. There are a lot of inbound vectors into the grid, and they must all be watched.
So, is the grid smart? The semantics don’t really matter. There’s intelligence in the grid today, and it’s getting smarter every day. Unfortunately, the same is true for risk and vulnerability. Smart or not, the grid is what it is: an important piece of our critical infrastructure that must be carefully and thoroughly secured.
Related Reading: Industrial Control Systems Security One Year After Stuxnet
Related Reading: Bridging the Air Gap: Examining Attack Vectors into Industrial Control Systems
Related Reading: Are Industrial Control Systems Secure?
Related Reading: How to Make the Smart Grid Smarter than Cyber Attackers
Related Reading: The Increasing Importance of Securing The Smart Grid
Related Reading: Stuck on Stuxnet – Are Grid Providers Prepared for Future Assaults?













