Google revealed last week that its infrastructure was targeted in a record-breaking distributed denial-of-service (DDoS) attack back in September 2017.
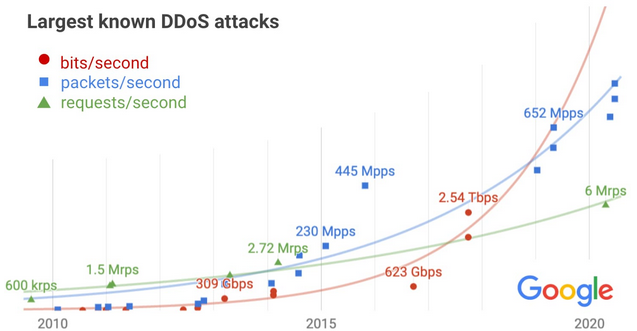
When measuring DDoS attacks, Google looks at three main metrics: bits per second (bps) for attacks targeting network links, requests per second (rps) for attacks targeting application servers, and packets per second (pps) for attacks targeting DNS servers and network devices.
The tech giant says DDoS attacks have increased significantly over the past years in each of these metric categories.
In terms of bits per second, Google spotted the largest attack in September 2017. The attack was aimed at the company’s infrastructure and it reached 2.5 Tbps, being described by Google as “the culmination of a six-month campaign that utilized multiple methods of attack.”
“Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact,” explained Damian Menscher, a security reliability engineer at Google, whose team focuses on DDoS defenses. “The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us.”
AWS reported this summer that a DDoS attack it mitigated in February 2020 peaked at 2.3 Tbps. When AWS disclosed the incident, it was considered the largest DDoS attack ever recorded, but apparently, bigger attacks were seen much earlier. Google now says that the attack it observed in 2017 is still the “highest-bandwidth attack reported to date.”
“[Even] though the 2.5 Tbps attack in 2017 didn’t cause any impact, we reported thousands of vulnerable servers to their network providers, and also worked with network providers to trace the source of the spoofed packets so they could be filtered,” Menscher said.
In terms of packets per second, the largest attack seen by Google reached 690 Mpps and it was generated by an IoT botnet earlier this year. While this was a significant attack, Akamai reported in June that it had seen a DDoS attack peaking at 809 Mpps.
As for attacks that involved sending a large number of HTTP/HTTPS requests, Google provided as example an incident from March 2014, when malicious actors injected JavaScript code into thousands of websites, causing the sites to flood YouTube with requests. The attack peaked at 2.7 Mrps (million requests per second). However, Google says it’s also aware of a more recent attack, aimed at a Google Cloud customer, which peaked at 6 Mrps.
Google has various tools and mechanisms designed to protect its customers against DDoS attack, but the company called on users and businesses to join the fight against such threats by ensuring that botnets cannot abuse their devices for attacks and, in the case of organizations, by analyzing attacks, reporting them to law enforcement, and sharing information with the community.
Related: NXNSAttack: New DNS Vulnerability Allows Big DDoS Attacks
Related: Hoaxcalls Botnet Expands Targets List, DDoS Capabilities
Related: DDoS Extorters Claim to Be Armada Collective, Fancy Bear













