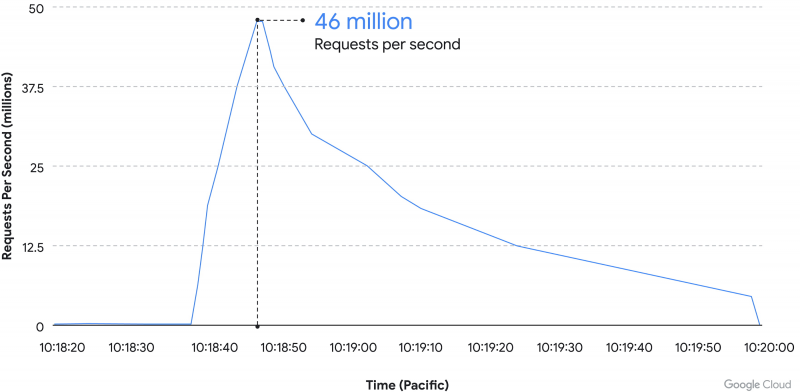
In June 2022, Google mitigated a Layer 7 distributed denial-of-service (DDoS) attack that peaked at 46 million requests per second (RPS).
Disclosed this week, this is the third HTTPS attack this year to reach tens of millions of RPS, after two lower-volume assaults were mitigated by Cloudflare.
The first of them peaked at 15.3 million RPS, Cloudflare announced in April, while the second reached 26 million RPS, the web security company announced in June.
What makes these assaults stand out from the crowd is the use of encrypted requests (HTTPS), meaning that they need significantly higher computational resources compared to typical DDoS attacks.
The attack that Google disclosed this week clearly dwarfs the previously disclosed incidents, as it was roughly 76% larger compared to the previous record.
The attack, Google says, started at 9:45 am PT, on June 1, and lasted for roughly 69 minutes. For most of its duration, the attack was low-intensity – it jumped from 100,000 to 46 million RPS within 10 seconds, but decreased over the next minute and a half to the initial levels.
According to Google, the assault originated from 5,256 source IPs from 132 countries, with 31% of the traffic coming from the top 4 countries.
Based on the characteristics of this attack, it appears that the Mantis DDoS botnet that Cloudflare detailed last month might have been responsible for the new record-setting incident as well.
“The geographic distribution and types of unsecured services leveraged to generate the attack matches the Mēris family of attacks. Known for its massive attacks that have broken DDoS records, the Mēris method abuses unsecured proxies to obfuscate the true origin of the attacks,” Google said.
Mantis – which uses a small number of compromised servers and virtual machine platforms – represents the evolution of the Meris botnet – it has migrated from MikroTik devices to far more powerful systems, Cloudflare has pointed out.
Google also notes that roughly 3% of the attack traffic came from Tor exit nodes – which accounted for 22% (1,169) of the observed source IPs. The presence of these exit nodes in the attacks, Google says, is likely incidental, caused by the nature of the compromised services.
Related: Powerful ‘Mantis’ DDoS Botnet Hits 1,000 Organizations in One Month
Related: Palo Alto Networks Firewalls Targeted for Reflected, Amplified DDoS Attacks
Related: Mitel Devices Abused for DDoS Vector With Record-Breaking Amplification Ratio















